IT Security Assignment: Critical Analysis of two Security Tools Hydra and Nmap
Question
Task: Objective
This assessment item relates to the unit learning outcomes as in the unit descriptor. This assessment is designed to improve the ability of students to critically analyse security tools and present their findings. The assignment provides an opportunity to work in a group and to achieve a joint objective.
Description
Each group is required to critically analyse any 2 security tools from the list and demonstrate the functionality of the tools in a video presentation. The list of tools for the assignment include:
• Hydra
• Maltego
• NMap
• Zed Attack Proxy
• SqlMap
• Metasploit Framework
• Burp Suite
• Nessus
• Nikto
• Snort
The tools need to be launched in Linux terminal (a user could be created for any member of the group).
Each group is required to:
1. Install and launch the 2 security tools in Linux terminal (a user could be created for any member of the group). Screenshots need to be provided with a brief description.
2. Evaluate 4 features of each tool. Description and screenshots need to be provided for each tool.
3. Critically analyse each tool in terms of:
a) Ease of Use
b) Performance
c) Scalability
d) Availability
e) Reporting and analytics
4. Demonstrate the 4 features of the tool in a short video not more than 5 Minutes. Each student is required to demonstrate 1 feature for each tool. If a student does not demonstrate in the video, the student will not be marked for the demonstration marks
Answer
Introduction
This assignment is undertaken to demonstrate the critical analysis of security tools within the network. Two different tools have been selected such as Hydra and Nmap to demonstrate the analysis results. Details along with the screenshots are provided for both the installation as well as feature analysis of the selected tools.
1. Installation and Launch of Two Tools (Hydra and Nmap)
1.a) Installation and Launch of Hydra
1st step Command: Sudo add-apt-repository ppa: pi-rho/security
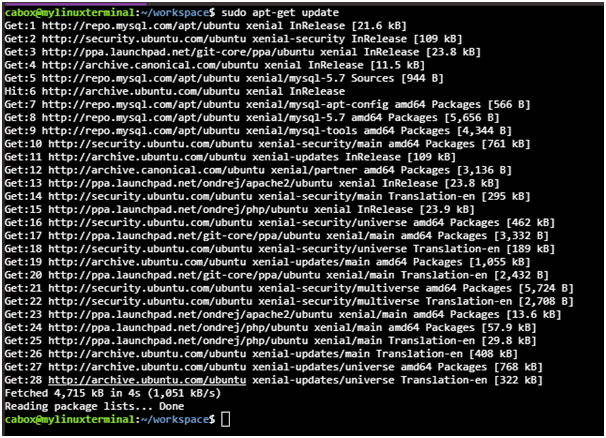
2nd Step: Command: update of Sudo apt-get
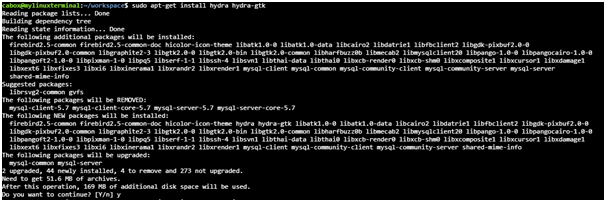
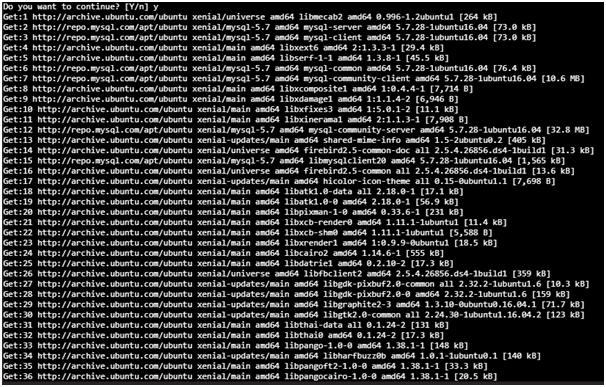
3rd Step Command: Need to type Y and press enter
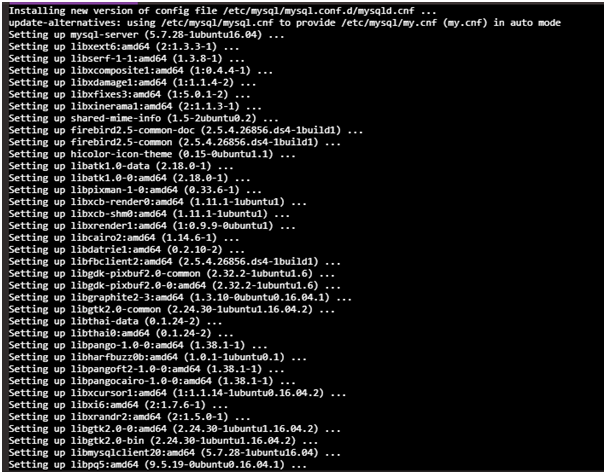
Hydra has been considered as the cracker of parallel login supporting different types of protocols for saving from an attack. It is considered as quite flexible and often it becomes easier to add some modules. Through this tool the security consultants and the researchers are capable of gaining the unauthorized access easily to the remote system. Such module engine on the other hand, is quite easy for effective and new services as this cannot take longer until the support of more services. Planned consists of Oracle, SSH vl and many more. This tool is regarded as the evidence for concept code for giving the security consultants and the researchers certain possibility for exhibiting the fact that it is very easy to receive unauthorized access from that of the remote to the system.
1.b) Installation and Launch of NMap
1st step: Need to pu the command sudo apt-get install nmap in linux terminal
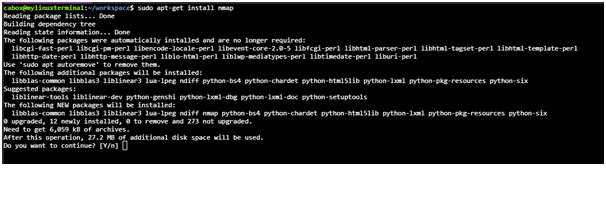
2nd Step: Need to press Y and then press enter
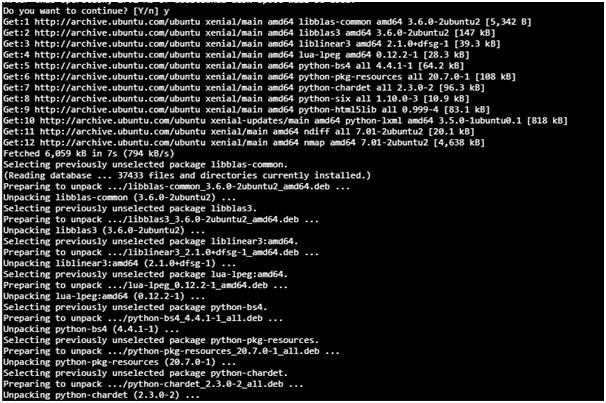
Then it is necessary to run concerned command namely “nmap” on that of terminal and this is supported by that of IP target or the website address and different parameters already available. N-map can be utilized with that of “nmap-help” command for getting proper overview of different parameters. This is regarded as the primary command for the purpose of quick checking when the website stays up (in such case, it is necessary to use howtoforge.com IP) without formulating any of the “loggable” interaction with that of the target server. Four of open ports are there that have been exhibited here. When all of the ports get filtered, (that happens in case of the screenshot) such command of guessing can be considered as the best possible option yet the results can appear to be quite reliable. The numbers of percentage have given proper idea related to uncertainty.
2. Evaluation of Features
2.a) Evaluation of 4 Features for Hydra
1st Feature: Fast Logon Cracker
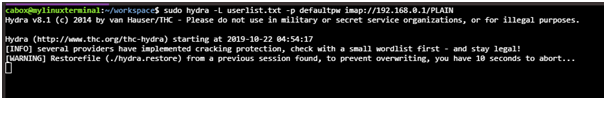
First number of the most important security gaps is associated with passwords as in this case appears as every secret word related to security study. Hydra has been considered as the paralyzed saltine for login supporting the different types of conventions to that of assault. Newer modules are anything but quite tough to include things associated with that and this is quite quick and adaptable. This is considered as quite quick and sometimes considered as the quickest logon system supporting broad range of the administrations. this is considered as best of paralyzed programmer login: for FTP, Samba, POP3, Telnet, IMAP, LDAP, HTTP Auth, MySQL, NNTP, ICQ, VNC, Socks5, Cisco, PCNFS and this is only the upper art of iceberg. This is also responsible for incorporating the SSL support and this is also the part of Nessus.
2nd Feature: Reading Password
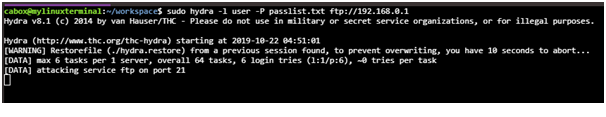
PW-Inspector is responsible for pursuing the passwords in and the prints addressing the necessities or requirements. Arrival of the code can be discovered secure password numbers and 0 if nothing can be found. For security check passwords is important and decision for secret purchase gets dismissed with the return of 0. For hacking use: trim record for word reference to the requirements of PW related to objective. Utilization is regarded for the lawful objectives.
3rd Feature: Listing collective passwords
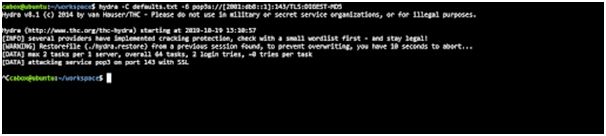
For hacking passwords and usernames of web structure it is necessary to have proper parameters related to the login page of web structure regarding this structure responds to fizzled or troubled logins.
4th Feature: Reading length of passwords
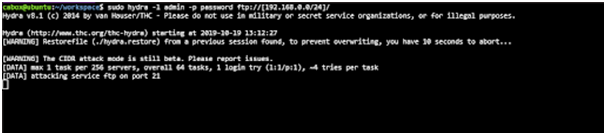
For receiving THC-Hydra in order to chip away at the web structures, disappointment message appears to be critical. It is considered as message based on books for such particular situation and yet on certain occasion it can also be the treat though the most important part is finding out the way such application is associated with the frizzled login.
2.b) Evaluation of 4 Features for Nmap
1st Feature: Hostname and IP address scanning system
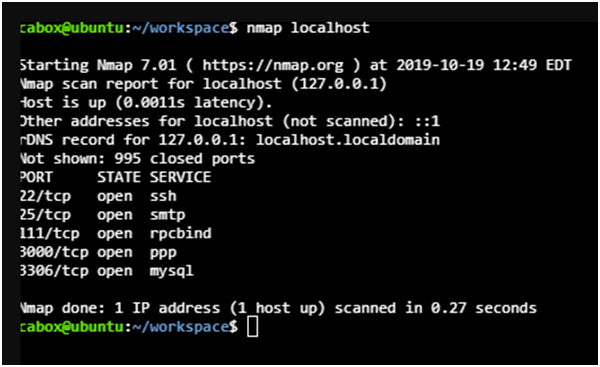
Nmap device is responsible for offering various strategies for framework filtering and in such model; output hostname has been used like server2.tecmint.com for finding out each of open port, MAC address and administrations on the framework.
2nd Feature: Allowing information perspective of the Remote Machine
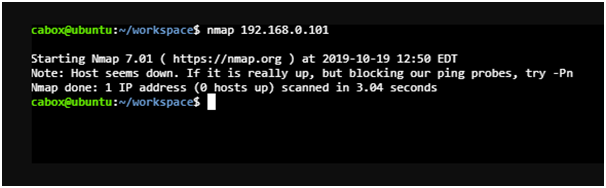
In this output, Nmap can be seen and can be assumed TCP?IP finger impression related to running OS on that of the remote and being explicit progressively regarding the administrations and running on those remote hosts.
3rd Feature: Multiple Hosts scanning
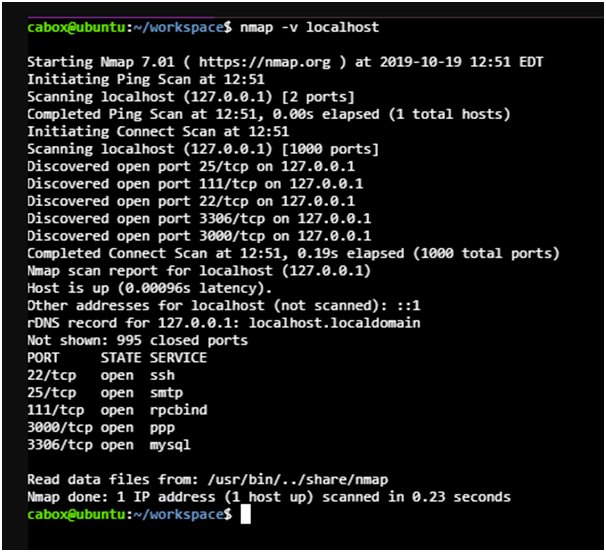
IP addresses can be conducted through last octet related to IP address.
4th Feature: Scanning of Whole Subnet
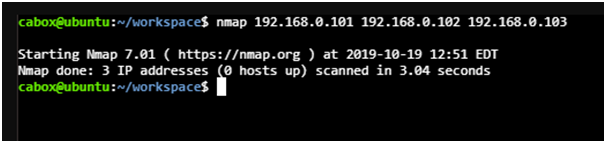
Host subtleties can be written in the record when more outputs are there. Book document can be created and all IP locations can be created that are required for the output.
3. Analysis
a) Ease of Use
Hydra:The successful implementation of this software was carried out in the year 2005 by the company- LCC ICT and since then this product has strongly been growing in the market. If we look at the features of this software which defines the simplicity and comfort of using this product, the below points can help to explain this:
• Even if the technical architecture of this tool is updated regularly and changes are defined in such upgrades, the installation and implementation process has always been easy for the users
• When a company uses this tool to its full potential, it gives them the power to impact their organization in a revolutionary way by working on the portfolios and efficient workforce planning [3].
• The post product sale services provided by the company- the Hydra Management Limited is outstanding compared to the industry expectation levels. With this approach, the tool has also been active in developing solutions which are of distinguishable nature.
• The standardization used in the tool enables it to use its SQL and develop the reports with the learnings inbuilt.
• Last but not the least, it has given an additional visibility into the project delivery and cost budgeting for the organizations.
NMap:The Network Mapper came into the market in the year of Setp-199. Most of its codes are written in English and is also available in the variants of other languages including Lua, C, C++ & Python. The below features of this tool describe the user comfortability it provides:
• Being an open source tool is its best feature and is available for free in the market to be downloaded by the users and used for the purposes of scanning networks and identify the vulnerabilities that exists in such networks starting for the details of all the devices present in the system, their software version, the services offered by these devices and the security threats they pose to the system. All this is possible due to the extensive port scanning feature this tool provides [4].
• If we compare to the other such applications present in the market, it is the best out of them in the filed of network scanning and the number of scans it can perform on the system owing to the diverse set of protocols it can follow for sending the error messages.
• It can easily help the users in identifying the exploits present in a system through auditing
• Its biggest advantage is the large size of the community it serves. This scale helps it to gather data and documents, based on this the system is upgraded to meet the latest demands of the users.
b) Performance
Hydra:In terms of performance, the services provided by this tool is unparalleled in the field of project management. It has been a general opinion and feedback from the market to any user seeking to use a project management solution, whether the user is looking in terms of a high capacity handling software or the number of features it can provide. It can perform a large variety of application efficiently in the field of capacity analysis, resource management, project registration, customization and fixation depending on the individual need and thus supports the complete package of functionality a user would need [5]. Though this software has also few glitches observed over the past years including the scenarios where it has not been able to plan a MS project or handle the project which are of high complexity.
NMap: The Network Mapper tool being free in nature does not, at all, compromises in its functionalities, with credits to the regular updates the tool receives over the year. The freeness of the software also brings some of the negatives in its performance. Firstly, looking at the positives is the beautiful user interface it provides when it complete the work network scanning and comes out with all the results that a user can expect to see after the scanning is complete but the installation process of this software requires that the user also downloads the other application called Zen map so that NMap can function properly. In the initial phase, the time taken for scanning is quite long and user may lose patience with its working [6]. Since, root cause analysis is a time taking process, the software can be very useful for such type of works.
c) Availability
Hydra:This software is easily available in the market and can be downloaded and installed in all the operating systems including Windows, Linux, Ubuntu, Android but not Macintosh. The owner of tis software is the company MPDV-USA. Being used in diverse industries, it covers mostly the organizations in the field of automobiles, food packaging, healthcare, plastic and rubber industry. The technology used in this software is BluTec technology which provides the usage of blueprint creation of all the processes of an organization. With this functionality and application of compliance rules, it further enhances the identification of deviations and all the bottlenecks in a plan and suggests possible solutions for error correction, thus enabling creation of a repeatable management process [7]. It also possesses other features of assessing impacts, calculate what if scenarios and develop capacity models.
NMap:Being an open source tool is its best feature and is available for free in the market to be downloaded by the users and used for the purposes of scanning networks and identify the vulnerabilities that exists in such networks starting for the details of all the devices present in the system, their software version, the services offered by these devices and the security threats they pose to the system. The application results in time savings for the users by providing quick resolution to root cause analysis problems.
d) Scalability
Hydra:With the large number of functionalities that can be covered by this tool, it provides services to more than 50 companies globally. The basic coding of the tool is strong which makes it highly robust in technique, and a great solution provider which is worthy of trust of the users.
NMap:It can easily be scaled for use globally as it works on the all the operating systems available in the world. The latest updates always arrive timely which is a very important factor when considering scalability for a tool as different users have different range of service expectation and it needs to meet these standards for all the users. Its physical location identification for any defect in the system has increased the popularity of this product globally. It uses the protocols present in the market consisting of TCP (Transmission Control Protocol), ICTP (Internet Control Message Protocol), SCTP (Stream Control Transmission Protocol) for sharing of the error messages. With the diversity of the protocols this tool can use, it encompasses many ports [8]. The other features of NMap are also being improved including the capability of capturing packets and scanning of fundamental ports. The other functions that this tool can provide includes detection of operating system and identifying their version and maker details, discovering the version of the software available in the system, audit the security infrastructure of an operating system and detect the vulnerabilities present in them.
e) Report and Analytics
Hydra:This software generates an access point of singular nature along-with maintaining consistency of behaviour across all the data points, irrespective of where the data originates from. The origination point can include the software of Microsoft, Oracle, SAP, SQL and many more. The data analytics feature of this toll is highly user interactive. The report generation process is done from a single point and this eliminates the requirement of maintaining multiple number of password protection system [9].
NMap:This software provides excellent visual data analytics and can provide an output in graphical presentation modes. The report can be extracted from the multitude of software that companies generally use. The reporting of all the system vulnerabilities are also done in a credible manner and it avoids any negligence that could arise during report generation.
Conclusion
This tool is a solution in the field ofprogram management and based on the cloud technology. The major functions that can be carried out by this software includes defining, execution, management and analysis of the project, preferred in the design industry and other areas including R&D, consulting & IT services. This software acts as a central interface for completion of activities not just limited to file sharing, business process & project management, but also for document managing, knowledge capturing, resource management, tracking of expenses & time, etc. Nmap is the abbreviation for Network Mapper and this software can perform the scanning activities on the network as well as discover them. It can further assist in identifying all the devices present in the network, the services that can be offered by these host devices, availability of open ports in the system and detection of the potential security threats in these systems. In terms of capacity, this tool which is an open source, freely available in the market, can handle hundreds of thousands of hosts. The tool has been effectively updating itself though learning over the years, it scans the ports for raw data and sends to the systems, acting as the firewall, and categorises the ports into filtered, open or closed.
References
[1] N. H. Tanner, “Wireshark,” in Cybersecurity Blue Team Toolkit, 2019.
[2] J. Andress and J. Andress, “Chapter 11 – Operating System Security,” in The Basics of Information Security, 2014.
[3] M. H. Bhuyan, D. K. Bhattacharyya, and J. K. Kalita, “Practical Tools for Attackers and Defenders,” 2017.
[4] L. Rosa, M. Freitas, S. Mazo, E. Monteiro, T. Cruz, and P. Simoes, “A Comprehensive Security Analysis of a SCADA Protocol: From OSINT to Mitigation,” IEEE Access, 2019.
[5] B. Middleton, Conducting Network Penetration and Espionage in a Global Environment. 2014.
[6] F. Ullah and T. R. Gross, “Profiling for detecting performance anomalies in concurrent software,” in SEPS 2015 - Proceedings of the 2nd International Workshop on Software Engineering for Parallel Systems, 2015.
[7] N. H. Tanner, Cybersecurity Blue Team Toolkit. 2019.
[8] S. Sinha, Beginning ethical hacking with Kali Linux: Computational techniques for resolving security issues. 2018.
[9] C. V. Arjun, “Penetration testing: Vulnerability analysis in a virtual environment,” J. Eng. Appl. Sci., 2017.












