Cyber Security Assignment: Android Mobile Application Threats
Question
Prepare a cyber security assignment about Android Mobile Application Threats discussing:
- Mobile App development
- Mobile application usage
- Mobile security challenges
- Key problem factors,
- Why attacks against mobile application are successful, mentioning backdoor threat and why we choose to use for our simulation, also why we generated with MSFvenom and Metasploit frame
- Android platform, OWASP mobile risks
- Application fundamentals
- Analyze the web application threat and its significance
Answer
Introduction
There has been an increase in the number and frequency of the security attacks on the mobile applications and platforms in the past few years. Kaspersky, Moscow based cyber security and anti-virus provider stated that there were 1,245,894 malicious installers identified in the second quarter of 2020. It was 93,232 more than the previous quarter. The mobile security attacks and threats can vary on the basis of the platforms and operating system. Android is one of the popular operating systems and it is exposed to several mobile security attacks.
Mobile Application Fundamentals
A mobile app is an application that is designed so that it may run on any of the mobile device. These devices could be Smartphones, tablets, or other devices. The mobile apps can be classified broadly in three categories as native apps, web apps, and hybrid apps. The native apps are the ones that are developed for only one operating system. For example, there are apps that can run only on Android or only on the iOS platforms. The applications that are platform-independent and use browsers to run are referred as the web apps. The combination of the two is known as the hybrid apps (Chell et al. 2015).
There are various programming languages available that can be used to develop the mobile apps. For instance, Android apps are usually developed using Java, C++, or Kotlin as the programming languages.
Mobile Application Development and its Process
There is a certain development methodology used to create the mobile apps. These applications are the software packages that can use the various software development methodologies. For example, the mobile apps may be developed using Waterfall, Spiral, Agile Scrum, or other development methods defined.
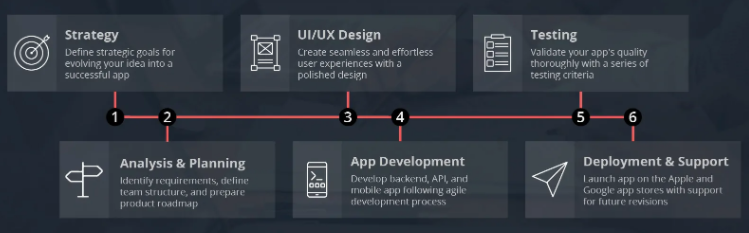
Mobile App Development Process
The crucial steps involved in the mobile development process are illustrated in the figure above. These steps may be executed in a linear sequence or parallel to each other depending on the development model and methodology used. UI/UX design is one of the very important stages in the mobile app development process. This is because the resolution and specification of the mobile device screen is different from the desktop or other computer systems. The design needs to be precise and responsive so that the development and deployment is streamlined.
Mobile Application Usage
The mobile applications can be developed for a variety of uses. There are numerous sectors and industries wherein the apps are used, such as finance, education, healthcare, etc. E-commerce is one of the significant sectors and there is a lot of business conducted through the mobile apps. For example, Amazon has a website and a dedicated mobile app which is used by the customers to place their orders, browse the items, cancel the orders, etc. Education is an important area in which the mobile apps are now being used for online learning sessions and classes. There are smart mobile applications being developed using the technologies, such as Artificial Intelligence and Internet of Things (IoT) (Mukherjea 2017). These integrated apps offer the efficient and smart functioning. Healthcare apps are the fine examples of such applications that keep a track of the user’s activity and health conditions and generate alerts accordingly.
Mobile Security Threats
Challenges
The mobile devices and applications are exposed to several security threats and challenges. These challenges are primarily due to the involvement of cloud in the mobile apps. The network connectivity is mostly essential to access the services provided by the mobile app. This leads to the occurrence of the security threats and challenges, such as data breaches, leakage, and loss of the data sets, malware attacks, denial of service, and other security attacks (Sardasht, Bakhtiar & M. 2016). The mobile device may be stolen or may get misplaced and the poor access control on the device and the mobile apps can compromise the security of the information and the user.
Key Problem Factors
The network channels are the primary threats agents that are involved in the security attack on a mobile device. The users often connect their devices to public Wi-Fi or such unsecure network. In such cases, the attackers can easily penetrate in the device and can violate the security of the mobile app and the device. The lack of updates is another major problem. The mobile apps and the devices are often not updates which lead to the exploitation of the security vulnerabilities by the attackers. The negligence from the users is another major factor that leads to the occurrence of several security threats and attacks (Fakunle 2016).
Threat Types
The mobile security threats can be classified in different categories. One of these classifications is on the basis of the threat agent involved. These can include the physical security attacks, network-based security attacks, application-based attacks, and web-based attacks. Other classification is one the basis of the information properties that are attacked. These include the confidentiality attacks, integrity threats, and availability threats. For example, denial of service is a mobile security threats in which the availability of the information sets and the network channels is targeted (Rocha, Souto & El-Khatib 2020).
Mobile Apps Backdoor Threats
Backdoor Threats
The mobile app backdoor threats and attacks are the ones that provide the attackers with an unauthorized access to the system by violating the security norms and mechanisms. The threat works in the background as the users do not get to know about its functioning and it is difficult to identify and detect. The malicious attackers often use the malware to install the backdoors and obtain the remote access and administration to the system. The backdoor access enables them to modify the system files, application information, and take the application control. The confidential information in the mobile app can be accessed and modified by the attackers. As a result, the attack can have extremely severe consequences (Elenkov 2015).
There are numerous such backdoor threats identified for the mobile applications. Android APK backdoor named GhostCtrl is one of the popular Android backdoors that can masquerade as a legitimate mobile app (Priya, Samy & Nya 2018). ShadowPad is another popular backdoors that was identified in 2017 and it was created specifically for the server management applications. Due to the devastating impacts that the backdoor threats can cause, there are certain measures that are created to control and prevent the occurrence of the backdoor attacks and threats.
Metasploit Framework
Metasploit framework is one of the extremely powerful tools that can be utilized by the cybercriminals, cyber attackers, and the ethical hackers to probe the systematic vulnerabilities on the networking channels and the servers. The framework is open-source and therefore, easy customization is possible.
The Metasploit framework is selected as it provides the ease of installation and it is also platform-independent and reliable. The framework is popular and it is open-source making it a familiar tool in the world of cybersecurity. There are 1677 exploits that are covered under the framework and these are organized across 25 different platforms. These platforms include Android, Java, PHP, and numerous others (Prakoso, Riadi & Prayudi 2020). These frameworks also comprise of over 500 payloads and some of these cover the command shell payloads that provide the users with the ability to run the scripts or generate random commands. There are dynamic payloads that can provide the testers with the ability to generate the uniquely identifiable payloads. Meterpreter payloads can assist the users in commandeering the device monitors with the aid of VMC. These can be used to manage the sessions and also upload/download the files. Port forwarding is one of the tasks that can be executed using the static payloads.
There are numerous benefits that the Metasploit framework provides apart from the exploits and payloads as described earlier. There are modules included for the auxiliary functions and encoders along with the listeners, shell code, and post-exploitation code. Once the framework is installed, there is detailed information about the target that can be easily obtained. This can be carried out through port scanning or OS fingerprinting, or other methods. The vulnerability scanner can also be used. Once the information is gathered, the adequate exploit can be selected along with the payload (Putra & Mardianto 2019). The exploit in this case refers to the weakness to make sure that the security of the mobile app, device, or the network is made complex.
Benefits of MSFVenom
The Metasploit Framework includes a number of effective tools, such as msfpayload and msfencode for several years. These are the tools that can be effectively used for generating the payloads in numerous formats. Also, these can then be encoded with the aid of a wide range of the encoder modules available. The amalgamation of the two tools in the one provided significant benefits. Some of the benefits include the standardization of the various command line options, enhancement of the overall speed using the single framework instance, and management of the different output formats. The payload generation is better handled with the combination of the tools (Talouki & Chemazi 2018).
MSFvenom provides the effective combination of these two tools as it puts both of these in a single framework instance. There are a lot many benefits offered with such a combination. Apart from standardization and speed as the primary benefits, there is a wide range of options available under MSFVenom. Also, there is a wide range of platforms that the user can enter using MSFVenom. Some of these include Cisco, Firefox, JavaScript, Linux, Android, PHP, Unix, and several others.
Android Specific Threats
Android is one of the most popular mobile operating systems and it is exposed to various security threats and attacks. Broken authentication and the broken access control are determined as one of the major security threat that the Android applications and devices are exposed to. This is due to the weaker and poor authentication and access control methods that are still used. For example, a number of users put weak passwords, such as their name or date of birth to access the confidential applications. The attackers can compromise these passwords or session tokens to gain access to the Android apps (Adagale 2017).
There are several Android apps and APIs that do not provide the security to the confidential and sensitive information. The sensitive data is exposed and the APIs are exploited to violate the confidentiality and security of the information sets. Cross-site scripting or XSS attacks are common in the Android apps and devices. These are the attacks in which the malicious entities execute the malicious scripts on the victim’s browsers. The user sessions can be hacked through these attacks or the confidential information can be accessed and misused. There are different forms of malware packages and codes developed to attack the Android apps. One of the recent additions is the ransomware. These are the malware packages that are launched and these encrypt the device or application files and data sets. The user access is blocked and a ransom is asked to provide the access again. There are several forms of injection attacks also executed on the Android applications and devices. These can include the SQL injection, NoSQL injection, or other (Abdalla et al. 2016). The malicious queries are used in the SQL injection attacks to retrieve the private and sensitive information from the database.
The Android apps and devices are also exposed to the denial of service and distributed denial of service attacks. These are the attacks in which the availability of the application or the device is targeted and is compromised. The garbage traffic is loaded on the application channels or the devices to block the effective functioning.
Conclusion
The mobile applications and devices are exposed to a large number of security threats and attacks. There are newer forms of such attacks being created with the development and advancement of the technology. It is necessary that these advancements are used and implemented in the control and handling of the security threats and attacks. The integrated security management and handling is of the utmost importance to make sure that the mobile application security is maintained. The administrative and technical controls along with the physical security measures must be used to ascertain the security of the mobile apps and devices.
References
Abdalla, HB, Lin, J, Li, G & Gilani, SMM 2016, ‘NoSQL: Confidential on Data Security and Data Management by Using a Mobile Application’, International Journal of Information and Electronics Engineering, vol. 6, no. 2, pp. 84–88.
Adagale, MsSS 2017, ‘A Review of Android Smart Security’, International Journal Of Engineering And Computer Science.
Chell, D, Erasmus, T, Colley, S & Whitehouse, O 2015, The mobile application hacker’s handbook, John Wiley & Sons, , Cop, Indianapolis (Ind.).
Elenkov 2015, Android security internals?: an in-depth guide to android’s security architecture, No Starch Press, San Francisco, Ca.
Fakunle, DO 2016, ‘Software Security and Privacy Risks in Mobile e-Commerce’, TEXILA INTERNATIONAL JOURNAL OF ACADEMIC RESEARCH, vol. 3, no. 1, pp. 130–132.
Mukherjea, S 2017, Mobile application development, usability, and security, Information Science Reference, Hershey Pa.
Prakoso, DC, Riadi, I & Prayudi, Y 2020, ‘Detection of Metasploit Attacks Using RAM Forensic on Proprietary Operating Systems’, KINETIK: Game Technology, Information System, Computer Network, Computing, Electronics, and Control, pp. 155–160.
Priya, SS, Samy, KA & Nya, AS 2018, ‘Android Platform for the Mobile Application Security System’, International Journal of Mobile Computing and Application, vol. 5, no. 1, pp. 1–8.
Putra, RD & Mardianto, I 2019, ‘Exploitation with Reverse_tcp Method on Android Device using Metasploit’, Jurnal Edukasi dan Penelitian Informatika (JEPIN), vol. 5, no. 1, p. 106.
Rocha, T, Souto, E & El-Khatib, K 2020, ‘Functionality-based mobile application recommendation system with security and privacy awareness’, Computers & Security, vol. 97, p. 101972.
Sardasht, M, Bakhtiar, M & M., R 2016, ‘Mobile Application Security Platforms Survey’, International Journal of Computer Applications, vol. 133, no. 2, pp. 40–46.
Talouki, M & Chemazi, M 2018, ‘Toward signature extraction of Metasploit encoding algorithms using static analysis’, International Journal of Security and Networks, vol. 13, no. 2, p. 71.












