Cyber Security Assignment on Data Leakage Issues & Prevention Techniques
Question
Task: Prepare a detailed and well-researched cyber security assignment critically discussing the digital data leakage issues and prevention techniques.
Answer
2.1.1 History of data leakage
The issues around data leakage discussed herein cyber security assignment have gained a lot of attention in the recent times because of the increase in the frequency of such issues. A large number of industries and businesses now rely on the digital technologies and data sets with sensitive business information that is stored on the cloud storage mediums. There are numerous opportunities for the attackers to violate the access controls and gain access to the data sets and network channels.
Data leakage issues did not initiate when the organizations started storing the sensitive information digitally. Rather, these issues have been in picture since the records were maintained by the organizations and stored in any form. Earlier, the data leakage issues were associated with the paper-based records that were either handed over to the unauthorized entities or were no disposed of properly. The publicly disclosed issues started to come in focus in the early 1980s. The leakage issues around the computing technologies and mediums could be noticed from the beginning of 2000s (Singh 2017).
There are several laws and regulations developed to make sure that the data leakage and other security and privacy concerns can be avoided. These laws and regulations vary based on the regions and the industrial sector. For example, HIPAA is the security standard and legislation followed in the United States to protect the healthcare information (National Business Institute 2016). PCI data security standards are developed to share guidelines for the organizations dealing with sensitive customer data.
With the aid of such regulations, the business firms can have an understanding of the specific practices and norms they shall follow to prevent the issues around data leakage and breaching of the data sets.
The majority of the information on the data leakage issues is based on the timeframe of 2005 and beyond. It is primarily because of the technological advancements and increase in the use of the electronic information in this period. With such advancements, the attackers also came up with new methodologies and mechanisms to carry out the data leakage issues. Currently, these issues can have an impact on millions of users from a single instance of an attack.
Privacy Rights Clearinghouse maintains detailed records of data leakage issues that impact the customers and also maintains chronology of such events dating back to 2005. The issues around breaches and leakage comprise of the ones in which confidential details of the end-users are compromised. For example, the cases in which the financial details or social security numbers are captured are considered to be critical.
Apart from the major issues, there are other issues of data leakage also reported so that detailed understanding of the possibilities and nature of impact can be determined. With every passing year, the volume and variety of the data sets generated and processed by the business firms has been increasing exponentially. It gives the malicious entities the opportunity to violate the data properties and capture the sensitive pieces of information (Subhashini & B 2015).
Cloud is one of the integral elements used by the business firms in the present times. Most of the business activities now conducted is based on the cloud technologies. It has been stated that over one-third of the entire data is currently present or passes through the cloud. The data production in 2020 has increased 44 times as it was in the year 2009. The individual are responsible for the creation of around 70% of the data and 80% of the data sets are stored by the enterprises.
There are several researchers engaged in the determination of the data breaches and leakage issues that have been occurring across the globe. Cyberattacks and cybersecurity issues are increasing with millions of users and records impacted as an outcome of these attacks. For example, in 2014, 783 cases of data breaches were reported in the United States and these resulted in the security compromise of more than 85.61 million records. These numbers have been doubling and tripling in a few years which are a major cause of concern for the business firms and industrial units. This is primarily because of the adverse implications of the data leakage and its access by the unauthorized entities (Statista 2018).
The trend associated with the cyberattacks and issues of data leakages are not consistent. For instance, the total issues of breaches in the US reduced to 498 from 656 in 2008. On the other hand, the number of records exposed in these breaches increased with a huge margin from 35.7 million in 2008 to 222.5 million in 2009. The impact of the data leakage and issues of security breaches has been worsening with each passing year. This is because of the exposure of the private and confidential information in such cases of security violation.
According to a report published by Forbes, there are over 300 data breaches in the last 10 years that have been successful in stealing over 100,000 records. There are many issues around data leakage that are not revealed in public and not reported.
One of the largest data leakage issues reported in history indirectly involved Experian which one of the main credit reporting agencies. Experian acquired another company by the name of Court Ventures that was engaged in the collection and compilation of data from public records. The acquisition happened in March, 2012. Court Ventures was engaged in another contract with another firm called US Info Search when Experian acquired the company. As per the existing contract, US Info Search has the rights to access the organization information to find out the individuals’ addresses to map the records with the details for review (Krebsonsecurity 2020).
Court Ventures sold the confidential details to numerous third-parties and one of these parties was Vietnamese fraudster service. The fraudulent company then provided its customers with the ability to search the personal information of the users along with their financial details and other confidential data. It led to identity theft in multiple cases.
Experian released an official statement describing the entire situation and claimed to have been working to resolve the issue. The company also said that no internal databases were involved in the issue and the database of US Info Search was the one that was being used to obtain the consumer details. Some of the media houses reported that more than 200 Million records were impacted in the incident and it continued for over 10 months after Experian acquired Court ventures.
There are numerous other incidents and occurrences of data leakage issues in the past wherein millions of the customer records and information has been exposed. One such issue was reported for Heartland Payment systems that suffered massive cybersecurity attack in 2008-2009 and it led to exposure of over 130 Million records (Lewis 2015). The company is based out of New Jersey and it is a payment processor. Malware was used to execute the attack and it was launched on the internal network of the organization. With the aid of the malware, the credit card information as received from the retailers was recorded and it was accessible to the malicious entities. It is, therefore, considered as one of the worst cases of cyberattacks in the credit card industry.
There are different measures and mechanisms adopted by the attackers to carry out these data leakage issues. The major share of the issues is a result of the hacking attacks. There are insiders also usually involved in these security attacks which may cause significant damages. For example, one such attack took place on AOL and it led to the comprised security of more than 92 Million records. The insider was involved in carrying out the security attack. This issue was reported in 2005 and again in 2006 sensitive data was published by AOL and there were more than 20 Million records involved this time.
One of the massive issues of data leakage impacted the US military in 2009. In this case, 76 million records were compromised and these records were lost or stolen. Many notable business firms across the globe have suffered from the leakage and security breaches. For example, E-bay was a victim of security attack in 2014 in which 145 million records were compromised. JP Morgan was also exposed to a cybersecurity attack in 2014 and it resulted in the exposure of 76 million records (Rushe 2014). Yahoo was targeted and was a victim of a massive data security attack in 2016 which resulted in compromised security of more than one billion records. 198 million voter records were captured in 2017 by carrying out cybersecurity attack on deep root analytics.
Most of these issues were a result of the hacking activities leading to massive impacts on the consumers and the business entities involved. This is because of the significant impact on the customers as the security and privacy of their records is compromised.
With the increase in the occurrence of the issues around data leakage, breaches, and other forms of security attacks, it has become necessary that significant measures are adopted to control the occurrence of these issues. It is also necessary that the measures are in place to detect the possibilities of the security violations in advance so that the effective control measures and counter techniques are in place.
2.1.3 Data leakage vector
The data leakages that are carried out may be executed through the use of different attack vectors and measures. Based on these vectors, the data leakage issues can be further classified. For example, the parties that caused the leakage can be used as one of the measures to classify the leakage issues. There can be insiders that may be involved in the occurrence of the leakage issues. These issues may also be shaped by the external parties. The intentional leaks may be caused by the external parties or the malicious insiders. The external issues are usually conducted with the involvement of a hacker, social engineering techniques, or with the use of a malware. For example, a malicious external entity may exploit the backdoor of the system to misconfigure the access controls and the attempts can then be made to bypass the server’s authentication mechanism so that the access to confidential and critical data can be obtained.
Social engineering techniques are being largely used to carry out the data leakage attacks. The employees of a business firm or the customers are tricked by the cyber attackers to share the internal and confidential information with them (Nagpure et al. 2019). The information captured using these techniques are then misused by these malicious attackers. The internal issues around data leakage can be caused due to the deliberate actions of the insiders or there can also be unintentional actions that may cause the exposure of the data sets. A comprehensive criterion has been proposed in one of the research works based on the 1259 cases of data leakage and the resulting issues of data breaches. The outcomes showed that more than 60% of the issues were given shape by the insiders and the combination of technical as well as non-technical measures were adopted to carry out the security attacks.
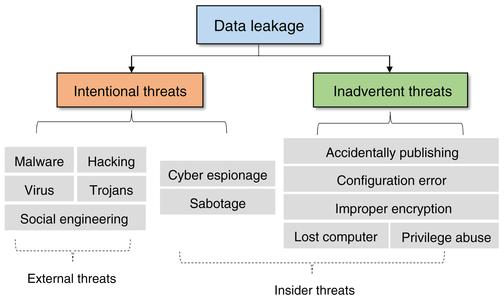
FIGURE 2.1 Classification of the data leak threats
(Hauer 2015)
The attributes involved with the issues of data leaks can also be utilized to categorize these issues. The report published by Identity Theft Resource Centre (ITRC) states that the total data leakage issues continue to rise in the last five years. For example, the rise of 40% was recorded in the leaks and breaches from 2015 to 2016. The figure below shows the stacked histogram plot of the data breaches and leaks based on the associated industry sector. The primary share of these leaks is associated with the healthcare sector. These made up for 34.5% of the total number of leaks. The second figure below shows the categorization of the leaks based on the occurrence. The majority of the issues are a result of the activities performed by a malicious external entity. These make up for 55% of the total number of incidents. For the business firms, the major cause of concern is the insider threats that cause data leaks and breaches. This is because of the privilege provided to the insiders. The rights and permissions are violated by the insider entities to share the confidential pieces of information with the unauthorized entities. As a result, the overall information properties and security of the information is violated and compromised.
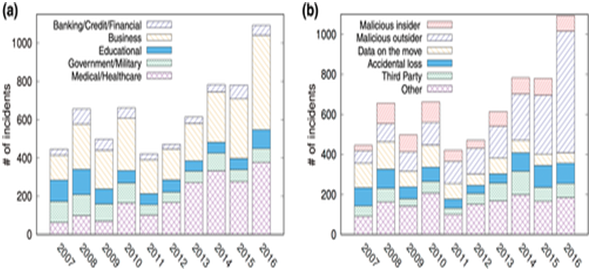
FIGURE 2.2 Number of Incidents
(Statista 2020)
Statistics – Data Leakage Issues
2.4 Data Leakage Prevention (DLP) software/programme
Data Leakage Prevention refers to the solution that has been developed to identify the potential leaks and breaching incidents so that the prevention of such issues is possible. The unauthorized exposure of the private and confidential information outside of the organization’s security perimeter results in the adverse impacts for the company. The DLP solutions and mechanisms promote the overall protection of the data so that the data is not exposed beyond the organization boundaries.
These solutions comprise of three primary data phases in their lifecycle. The first is data at rest; DAR followed by data in motion, DIM, and the last is data in use, DIU. Data at rest can be defined as the data sets that are present in the storage of the organization. To prevent these data sets from being stolen or from the violation of the security principles, the measures, such as encryption of the data sets and the advanced access control is used. Pre-requisite associated with these security measures is the content discovery to determine the storage details of the data sets. The DLP software and products come with the feature of content discovery. For instance, policy may require the storage of the customer credit card details on specific servers. If the data is found to be present on the servers other than the one approved, they can be encrypted or removed altogether. Also, the suitable warnings can be issued to the data owner (Andrianov, Sivkov & Yurkin 2020).
Data in use refers to the data sets with which the users may be interacting with. Endpoint-related systems are the ones that are utilized to preserve these data sets and to monitor the same as the user interacts with these data sets. Quite often, an agent is involved in the monitoring and transport of the data using the associated output devices. It is carried out to detect the malicious attempts involved in data leakage to share the confidential information to the unauthorized sources. DLP software packages come with numerous features to protect the data in use. For example, automated alerts and notifications are issued if the data is shared to the unauthorized sources. There are encryption measures incorporated to make sure that the security and privacy is maintained. The secure sharing is promoted by keeping a track of the source and destination addresses.
Data in motion refers to the data sets that are present over the network channel. These include the data sets that are sent from the source to the destination. The DLP solutions come with the features to detect the security issues associated with these data sets by using intrusion detection and prevention techniques across the communication channels involved. The secure protocols and emails along with the encryption of the data sets is used as some of the techniques to protect the sensitive information and to make sure that the issues around data leakage can be tracked (Andrianov, Sivkov & Yurkin 2020).
There have been numerous cases around data leakage and breaching of the data sets in the past that has promoted the use of the DLP software.
Most of the information on the data leakage issues is based on the timeframe of 2005 and beyond. It is essentially because of the technological advancements and increase in the use of the electronic information in this period. With such advancements, the attackers likewise came up with new methodologies and mechanisms to do the data leakage issues. Currently, these issues can have an impact on millions of users from a single instance of an attack. The issues around breaches and leakage comprise of the ones wherein confidential details of the end-users are compromised (Jadhav 2018). Apart from the significant issues, there are other issues of data leakage likewise reported so that detailed understanding of the possibilities and nature of impact can be determined. As time passes, the volume and variety of the data sets generated and processed by the business firms has been increasing exponentially. It gives the malicious entities the chance to violate the data properties and capture the sensitive pieces of information.
There are several researchers engaged in the determination of the data breaches and leakage issues that have been happening across the globe. Cyberattacks and cybersecurity issues are increasing with millions of users and records impacted as an outcome of these attacks (Hauer 2015).
One of the largest data leakage issues reported in history indirectly involved Experian which one of the primary credit reporting agencies. Experian acquired another organization by the name of Court Ventures that was engaged in the collection and gathering of data from freely available reports. The procurement happened in March, 2012. Court Ventures was engaged in another agreement with another firm called US Info Search when Experian acquired the organization. According to the existing agreement, US Info Search has the options to access the association information to discover the people's addresses to plan the records with the details for review.
Court Ventures offered the confidential details to numerous third-parties and one of these parties was Vietnamese fraudster service. The fraudulent organization then provided its customers with the capacity to search the personal information of the users alongside their financial details and other confidential data. It led to identity theft in multiple cases. Experian released an authority statement describing the entire circumstance and claimed to have been attempting to resolve the issue. The organization likewise said that no internal databases were involved in the issue and the database of US Info Search was the one that was being used to acquire the consumer details. Some of the media houses reported that more than 200 Million records were impacted in the incident and it continued for over 10 months after Experian acquired Court ventures.
There are numerous other incidents and occurrences of data leakage issues in the past wherein millions of the customer records and information has been exposed. One such issue was reported for Heartland Payment systems that suffered massive cybersecurity attack in 2008-2009 and it led to exposure of over 130 Million records. The organization is based out of New Jersey and it is a payment processor. Malware was used to execute the attack and it was launched on the internal network of the association. With the guide of the malware, the credit card information as received from the retailers was recorded and it was accessible to the malicious entities. It is, therefore, considered as one of the most pessimistic scenarios of cyberattacks in the credit card industry.
There are different measures and mechanisms adopted by the attackers to complete these data leakage issues. The significant share of the issues is a result of the hacking attacks. There are insiders additionally usually involved in these security attacks which may cause critical damages. For example, one such attack occurred on AOL and it led to the comprised security of more than 92 Million records. The insider was involved in doing the security attack. This issue was reported in 2005 and again in 2006 sensitive data was published by AOL and there were more than 20 Million records involved this time.
One of the massive issues of data leakage impacted the US military in 2009. In this case, 76 million records were compromised and these records were lost or stolen. Numerous notable business firms across the globe have suffered from the leakage and security breaches. For example, E-bay was a victim of security attack in 2014 in which 145 million records were compromised. JP Morgan was additionally exposed to a cybersecurity attack in 2014 and it resulted in the exposure of 76 million records. Hurray was targeted and was a victim of a massive data security attack in 2016 which resulted in compromised security of more than one billion records. 198 million voter records were captured in 2017 via doing cybersecurity attack on deep root examination.
Due to such security issues and incidents, the need for stronger and effective measures to protect the data sets from leaks and breaches was felt.
…..2.4.2 The security of Data Leakage Prevention (DLP) software/programme
Data leakage prevention solutions come with numerous features and capabilities integrated in these systems. These can monitor the data sets in use and also the ones in motion and at rest. Varied categories of controls and countermeasures are applied to make sure that the data sets remain protected at all times.
DLP is believed to be a paradigm shift in the field of information security as it comes with the capabilities to control and manage the risks. These security risks are based on the handling of specific solutions to discover, monitor, and safeguard the confidential information. There are various types of data sets that can be protected through the effective use of the DLP systems and packages. The personal networks and storage systems can be covered along with the data in motion, databases, and numerous other data sources (Nagpure et al. 2019).
DLP solutions are implemented to manage the business issues around safeguarding the confidential data pieces. These solutions are developed so that the integrated security controls are possible. The DLP solutions make sure that the solution components are created to determine the storage location of the sensitive and confidential information. The components are also included to monitor the sensitive pieces of information in the storage locations and when the data is shared on the external networks. There are four major components included in the DLP systems as network, management, storage, and endpoint.
Network covers the data in motion and it is essential that proper coverage is ensured with the DLP systems and solutions. The DLP systems cover and monitor the data sets that are shared over the network channels and there is a wide range of applications covered under the category. For example, emails as simple mail transfer protocol, file transfer protocol, and others. DLP systems make use of deep packet inspection to determine the actual content present within the data packets. The technique provides the ability to monitor the content across varied packets so that the signatures being searched for can cross the packet boundaries and are found.
Deep content inspection used in DLP comprises of various features and elements. The first is content matching. It is applicable for structured and unstructured data sets and makes use of the keywords, pattern matching, and file types, file properties, etc. to determine the extent and type of the data lost in an incident. The technique uses a number of algorithms and codes, such as MatchJoin algorithm to match the content and come up with the outcomes.
The second is learning method. DLP technique makes use of this approach and the major idea is to utilize machine learning concepts to understand the confidentiality level of the associated data sets. ML techniques, such as Vector space model is suitable in this case. Vector represents the documents and the vector features include the terms along with the frequency of their appearance (Nedogarok et al. 2020). The vectors are utilized as the learning sets to come up with a probabilistic model and the decisions on the confidentiality level of data are based on these sets. The technique can provide significant outcomes if it is used to detect unstructured content in scenarios wherein deterministic technique is complex and not easy to implement.
The first method that was explained was content matching and it is an effective method as it can provide information on all the keywords and regular experience but it is not effective if the document format keeps on changing. This is because the requirement of putting huge sample of documents to improve the accuracy and rate of false positives/negatives can be witnessed (Singh et al. 2020).
Based on the study of the DLP systems and mechanisms, there are certain pros and cons associated with each system. The existing systems make sure that the networks are protected from any of the external security issues and the periodic reports are delivered based on regular analysis. Also, the alarms and alerts are issues in the case of the occurrence of an attack. These systems make use of the ad-hoc approach and are not dependent upon the centralized approach to detect and prevent the issues of data leakage and other forms of security risks and attacks. DLP systems work in combination with the data security tools that the business firms may have implemented in advance over the network channels or as endpoint solutions. There are various forms of network security tools and controls that may be used, such as intrusion detection and prevention systems, firewalls, antimalware tools, encryption, and others.
The primary difference between DLP system and the existing security techniques is that the DLP systems are content-aware. These systems are developed to provide improved visibility to the security of the data storage systems and also cover the aspects around access control, privilege management, and authentication of the users. The existing security techniques and measures may not be efficient enough to carry out such tasks and activities. DLP systems shall come with integrated functions to make sure that the sensitive information is not exposed to security risks and attacks. There are also a few drawbacks associated with the DLP systems that must be acknowledged. These systems currently do not have the capabilities to read the encrypted information and the information hidden in the images or in the audio or video files. These can lead to the security and accuracy gaps if the business firms rely only on the DLP systems for the purpose of information security and privacy.
Deep packet inspection is developed to make sure that the network packets are properly analysed and investigated. The ability of these techniques enables firewalls to implement the blocked network access policies. It can have information around the intent of the packet covering the aspects as packet source, destination of the packets, and the specific ports that will be covered by these packets. Deep content inspection on the other hand has the ability to determine the information present inside the data packets (Ghosh & Senthilrajan 2019).
There are numerous challenges identified with dealing with the malicious entities and a number of methods are being developed to manage the issue. One of the primary goals of the insider attackers is to leak the data to the external entities. As a result, primary share of methods proposed for managing the insider threat detection are applicable in detecting and preventing the issues of data leakage. A number of techniques are used and followed to ensure that the warnings are issued to detect and manage the malicious activities of an insider. These may include the use of honey tokens or may also utilize knowledge-based algorithms. The structured analysis and data fusion is made possible with the use of these techniques and processes. Host-based profiling is one of the effective mechanisms to detect the insider threat and prevent the issues of data leaks that may result as an outcome. Intrusion detection and prevention systems can also be implemented internally in the organizations to detect the presence of malicious insiders. These systems have the option to issue alerts and showcase the specific patterns so that it becomes easier to get hold of the malicious activities of an insider and also prevent the other security threats that may come up.
2.5 Security awareness and information security
Information security incidents and attacks are increasing with every passing day. Many attempts are being made by the companies and the technology experts to make sure that the attacks can be prevented and control. However, the frequency is increasing with increase in the generation of the data sets and use of the technological tools and systems.
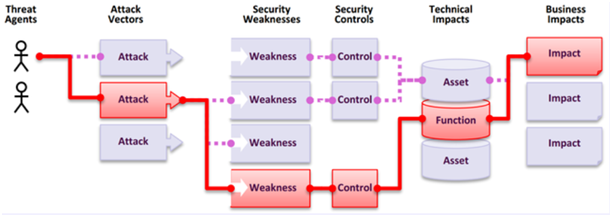
FIGURE 2.3 Information Security Attack – Flow and Impact (Haggag 2017)
The above figure shows the normal flow of a security attack and the possible impact of these security attacks. These impacts can be technical impacts and business impacts and the degree of these impacts varies.
There can be insiders that might be involved in the occurrence of the leakage issues. These issues may likewise be shaped by the external parties. The intentional leaks might be caused by the external parties or the malicious insiders. The external issues are usually conducted with the involvement of a hacker, social engineering techniques, or with the use of a malware. For example, a malicious external entity may exploit the secondary passage of the system to misconfigure the access controls and the attempts would then be able to be made to sidestep the server's authentication mechanism with the goal that the access to confidential and critical data can be obtained.
Social engineering techniques are being largely used to complete the data leakage attacks. The employees of a business firm or the customers are tricked by the cyber attackers to share the internal and confidential information with them (Haggag 2017). The information captured using these techniques are then misused by these malicious attackers. The internal issues around data leakage can be caused due to the deliberate actions of the insiders or there can likewise be unintentional actions that may cause the exposure of the data sets. The vast majority of the information on the data leakage issues is based on the timeframe of most recent 10 years. It is essentially because of the technological advancements and increase in the use of the electronic information in this period. With such advancements, the attackers likewise came up with new methodologies and mechanisms to do the data leakage issues. Currently, these issues can have an impact on millions of users from a single instance of an attack. The issues around breaches and leakage comprise of the ones wherein confidential details of the end-users are compromised. Apart from the huge issues, there are other issues of data leakage likewise reported so that detailed understanding of the possibilities and nature of impact can be determined. As time passes, the volume and variety of the data sets generated and processed by the business firms has been increasing exponentially. It gives the malicious entities the chance to violate the data properties and capture the sensitive pieces of information.
There are several researchers engaged in the determination of the data breaches and leakage issues that have been happening across the globe. Cyberattacks and cybersecurity issues are increasing with millions of users and records impacted as an outcome of these attacks. The security techniques can screen the data sets being used and furthermore the ones moving and at rest. Varied categories of controls and countermeasures are applied to make sure that the data sets remain protected consistently. These security risks are based on the treatment of specific answers for discover, screen, and safeguard the confidential information. There are various types of data sets that can be protected through the effective use of the security systems and packages (Bishop 2016). The personal networks and storage systems can be covered alongside the data moving, databases, and numerous other data sources. The arrangements are implemented to manage the business issues around safeguarding the confidential data pieces. These arrangements are developed so the integrated security controls are possible. These make sure that the arrangement components are created to determine the storage area of the sensitive and confidential information. The components are likewise included to screen the sensitive pieces of information in the storage areas and when the data is shared on the external networks.
The techniques used provide the capacity to screen the content across varied packets so the signatures being searched for can cross the packet boundaries and are found. Based on the investigation of the security systems and mechanisms, there are certain advantages and disadvantages associated with each system. The existing systems make sure that the networks are protected from any of the external security issues and the periodic reports are delivered based on regular examination. Likewise, the cautions and alerts are issues on account of the occurrence of an attack. These systems make use of the ad-hoc approach and are not dependent upon the centralized way to deal with detect and prevent the issues of data leakage and other types of security risks and attacks. The systems work in mix with the data security devices that the business firms may have implemented in advance over the network channels or as endpoint arrangements. There are various types of network security instruments and controls that might be used, like intrusion detection and prevention systems, firewalls, antimalware devices, encryption, and others.
These systems are developed to provide improved visibility to the security of the data storage systems and furthermore cover the aspects around access control, privilege management, and authentication of the users. The existing security techniques and measures may not be efficient enough to complete such errands and activities. The advanced systems will come with integrated capacities to make sure that the sensitive information isn't exposed to security risks and attacks. There are likewise a few downsides associated with the security systems that must be acknowledged. These systems currently don't have the capabilities to read the encrypted information and the information hidden in the images or in the sound or video files. These can lead to the security and exactness holes if the business firms rely just on a specific security system with the end goal of information security and protection (Bishop 2016).
Deep packet inspection is developed to make sure that the network packets are properly analyzed and investigated. The capacity of these techniques enables firewalls to implement the blocked network access policies. It can have information around the intent of the packet covering the aspects as packet source, destination of the packets, and the specific ports that will be covered by these packets. Deep content inspection then again can determine the information present inside the data packets.
There are numerous challenges identified with dealing with the malicious entities and a number of methods are being developed to manage the issue. One of the essential objectives of the insider attackers is to leak the data to the external entities. As a result, essential share of methods proposed for dealing with the insider threat detection are applicable in detecting and preventing the issues of data leakage. A number of techniques are used and followed to ensure that the alerts are issued to detect and manage the malicious activities of an insider. These may include the use of honey tokens or may likewise utilize knowledge-based algorithms. The structured examination and data fusion is made possible with the use of these techniques and processes. Host-based profiling is one of the effective mechanisms to detect the insider threat and prevent the issues of data leaks that may result as an outcome. Intrusion detection and prevention systems can likewise be implemented internally in the associations to detect the presence of malicious insiders. These systems have the choice to issue alerts and showcase the specific patterns so it becomes easier to get hold of the malicious activities of an insider and furthermore prevent the other security threats that may come up.
These aspects show that the mere implementation of the security tools and protocols is not sufficient to ensure that the security management is in place. Detailed awareness and knowledge on information security is crucial to stay one step ahead of the attackers. The security incidents are occurring event when the advanced measures are developed to avoid and prevent the risks. Many of the business organizations are still struggling to control these issues and suffer the negative outcomes of the security incidents on their reputation and the customer engagement aspects.
For instance, there are training programs that are developed and implemented by a number of industries and businesses to make sure that information security and privacy is covered as a subject in these trainings (Tasevski 2016). The employees, customers, and stakeholders get to know about the significance of information security through these training programs and also get the knowledge of the need to maintain and improve the security of the information sets. The best practices and specific aspects to avoid are also included in these trainings. Many of the security risks occur due to the negligence of the users. For example, passwords are used to implement access control and authentication on the information sets. It is necessary that the users make changes in the default passwords and also make sure that the weak passwords are not used. However, many of the users fail to do so.
There are also instances wherein the users share the confidential and private information with the external entities and the information can be misused by these entities. Accessing the internal systems on unsecure network channels also promotes the issues around information security and privacy.
Formal security awareness trainings also cover the aspects of ethical and unethical principles and approaches. As discussed earlier, a majority of the security violations in the business systems are due to the presence of the malicious insiders. The insiders shall have awareness on the ethical norms and legal obligations that my result with the violation of the compliance levels. Some of these issues also occur by mistake and the security trainings can avoid such mistakes.
The organizations can also link these trainings with the performance measurement and management aspects. Quite often, it is seen that the employees do not take these trainings seriously. As a result, the effectiveness of the training processes is not up to the mark. With the inclusion of the training hours and the results of the training assessments in performance and rewards cycle, it will be possible to gain the engagement and attention of the employees. It has been witnessed that the end-users practice unsafe computing behaviours without the understanding of the potential harm.
A research study was conducted to determine these aspects of the user behaviour. It could be determined that 49% of the participants used to engage in the risky behaviour occasionally and 28% were frequently involved in such issues. Many of the institutions and business organizations consider information security and privacy as one of the primary issues of the modern times. However, there are only a handful of the organizations that have formal training procedures and awareness sessions on information security and privacy.
In most of the business organizations, training on information security is a mere formality. The results of these activities are not effective as an outcome. Apart from the organization’s perspective, it is also necessary to consider the user’s perspective in the area of information security trainings and awareness. In most of the business firms, the employees understand the need to maintain security and are interested in taking the training sessions and awareness programs (Abraham & Chengalur-Smith 2019). However, the existing commitments and priorities clash with these training programs. The schedule of most of the employees is tightly packed making it difficult for the employees to enrol in these training sessions. Also, the employees prefer the other trainings, such as skill development or the ones directly applicable to the nature of job. For example, the healthcare employees are more interested in the medical trainings rather than being concerned about the ways to protect the information sets as part of the healthcare firm.
The students in the educational institutions get engaged in the security trainings but are not aware of the practical situations and scenarios. The concepts shared in the trainings are only theoretical leaving lesser impact on the students and their awareness in the area of information security.
2.5.1 Common behaviour influenced the risk of Data Leakage
There are several aspects and behaviour that influence the risk of data leakage in a business environment.
The desktop and laptops are assigned to the users to make sure that the business activities can be effectively performed on these systems. Many times, the employees do not lock these systems while not at their desks. The laptops are not locked or logged off and the information contained within can be easily accessed by an unauthorized entity. For example, in an IT firm, the user of laptops and desktops is very common. These systems are used by the employees to carry out the assigned project tasks and activities. There is a whole lot of information present in these systems. The access of such information sets by the unauthorized entities can result in the security threats and attacks. The fellow employees can access and steal the information from the employee. The web designs of a particular web app in development phase can be stolen or copied by another employee. The same designs may be used in another project and it will lead to massive impacts on the project and the organization. The Copyrights violation and the issues around the security compromises will be witnessed.
Passwords are used to control the access to the application and the systems. There are systems, databases, and applications that often come with a default password which shall be changed by the user upon accessing these systems for the first. Many users do not make changes in these passwords which makes it easier for the attackers to conduct the data leakage attacks. Brute Force technique is the most common in which the attacker guesses the password and then gains entry to the data sets (Pawar & Dani 2017). The default and weak passwords are easy to guess and these make the task of the attackers easy. There are unprotected passwords also used which can be easily acquired from the code.
There are millions of websites and web apps created by the developers for the users to access. There are also several unauthorized websites developed for the purpose of initiating a security attack. These websites comprise of the malware codes and functions that can get downloaded on the users’ system when the user accesses these sites. The technique is used in the phishing scams in which the duplicate sites are developed to trick the users. For example, a duplicate site for a banking website can be created and the same can be shared as a link on the customers’ mail addresses. When the customer clicks on the link the website will show up with the same UI and features as the original website. The users may put in their credentials and these will be shared with the attackers. The information can be misused to gain access to the user account and violate the security of the data sets. The financial transactions can be performed by the attackers using the user credentials.
The devices used for accessing the web applications and systems may be lost. The mobile devices, such as Smartphones can get misplaced or these may also be stolen by the attackers. In the case of loss of device, the information present in the device is put at risk. If the attackers succeed to access the device then the leakage of the information is certain and the impacts can be severe.
Emails and instant messaging apps are exposed to numerous leakage issues. The attackers can send spam mails and messages for the users to click upon. When the users click on such mails or messages, a malicious code may be downloaded on the user’s machine and the security violation can be attempted through the code.
There are certain aspects that can be adopted to make sure that the security risks and privacy violations do not occur. Two-factor authentication, for example, is one such technique. In this technique, multiple modes of authentication shall be used (Certic 2018). It shall include combination of passwords and biometric recognition or the use of one-time passwords to make sure that the violation of access control and authentication does not take place.
Detailed awareness and knowledge on information security is essential to stay one step ahead of the attackers. The security incidents are happening event when the advanced measures are developed to dodge and prevent the risks. A large number of the organizations are still struggling to control these issues and suffer the negative outcomes of the security incidents. There are training programs that are developed and implemented by a number of military organizations to make sure that information security and protection is covered as a subject in these trainings. The employees and stakeholders get to think about the significance of information security through these training programs and furthermore get the knowledge of the need to keep up and improve the security of the information sets. The best practices and specific aspects to keep away from are also included in these trainings. A significant number of the security risks happen due to the negligence of the users. There are also instances wherein the users share the confidential and private information with the external entities and the information can be misused by these entities. Accessing the internal systems on unsecure network channels also promotes the issues around information security and protection.
Formal security awareness trainings also cover the aspects of ethical and unethical principles and approaches (Haggman 2019). As discussed earlier, a greater part of the security violations in the business systems are due to the presence of the malicious insiders. The insiders shall have awareness on the ethical norms and legal obligations that my result with the infringement of the compliance levels. Some of these issues also happen by mistake and the security trainings can stay away from such mistakes. The military organizations can also interface these trainings with the performance measurement and management aspects. Quite often, it is seen that the employees don't take these trainings seriously. As a result, the effectiveness of the training processes is not sufficient. With the inclusion of the training hours and the results of the training assessments in performance and rewards cycle, it will be possible to acquire the engagement and attention of the employees. It has been witnessed that the end-users practice unsafe processing behaviours without the understanding of the potential mischief.
The military organizations consider information security and protection as one of the essential issues of the modern times. However, there are just a small bunch of the organizations that have formal training procedures and awareness sessions on information security and protection. Training on information security is a mere custom much of the time. The results of these activities are not effective as an outcome. Apart from the association's perspective, it is also necessary to consider the military personnel's perspective in the area of information security trainings and awareness. Much of the time, the military personnel understand the need to keep up security and are interested in taking the training sessions and awareness programs. However, the existing commitments and priorities clash with these training programs. The schedule of most of these personnel is firmly packed making it hard for them to enrol in these training sessions.
Data Leakage Prevention refers to the solution that has been developed to identify the potential leaks and breaching incidents so that the prevention of such issues is possible. The unauthorized exposure of the private and confidential information outside of the organization's security perimeter results in the adverse impacts for the organization. The DLP solutions and mechanisms promote the overall protection of the data so that the data is not exposed beyond the organization boundaries.
These solutions comprise of three essential data phases in their lifecycle. The first is data at rest; DAR followed by data in motion, DIM, and the last is data in use, DIU. Data at rest can be defined as the data sets that are present in the storage of the organization. To prevent these data sets from being stolen or from the violation of the security principles, the measures, such as encryption of the data sets and the advanced access control is used. Pre-requisite associated with these security measures is the content discovery to determine the storage details of the data sets. The DLP software and products come with the feature of content discovery. For instance, strategy may require the storage of the military application details on specific servers. In the event that the data is discovered to be present on the servers other than the one approved, they can be encrypted or removed altogether. Also, the suitable warnings can be issued to the data owner (Usha, K & Surbhi 2020).
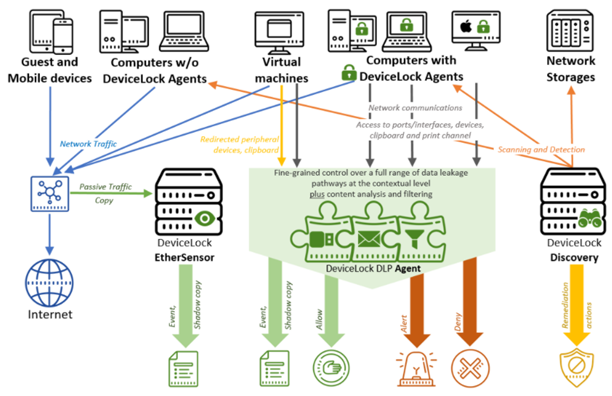
FIGURE 2.4 Data Leakage Prevention System (Rajasekaran, Gupta & Sharma 2018)
Data in use refers to the data sets with which the users might be interacting with. Endpoint-related systems are the ones that are utilized to preserve these data sets and to monitor the same as the user interacts with these data sets. Quite often, an agent is involved in the monitoring and transport of the data using the associated yield devices. It is carried out to detect the malicious attempts involved in data leakage to share the confidential information to the unauthorized sources. DLP software packages come with numerous features to protect the data in use. For example, automated alerts and notifications are issued if the data is shared to the unauthorized sources. There are encryption measures incorporated to make sure that the security and protection is maintained. The secure sharing is promoted by keeping a track of the source and destination addresses.
Data in motion refers to the data sets that are present over the network channel. These include the data sets that are sent from the source to the destination. The DLP solutions come with the features to detect the security issues associated with these data sets by using intrusion detection and prevention techniques across the communication channels involved. The secure protocols and emails alongside the encryption of the data sets is used as some of the techniques to protect the sensitive information and to make sure that the issues around data leakage can be tracked (Rajasekaran, Gupta & Sharma 2018).
There have been numerous cases around data leakage and breaching of the data sets in the past that has promoted the use of the DLP software.
Most of the information on the data leakage issues is based on the timeframe of 2005 and beyond. It is essentially because of the technological advancements and increase in the use of the electronic information in this period. With such advancements, the attackers likewise came up with new methodologies and mechanisms to do the data leakage issues. Currently, these issues can have an impact on millions of users from a single instance of an attack. The issues around breaches and leakage comprise of the ones wherein confidential details of the end-users are compromised. Apart from the significant issues, there are other issues of data leakage likewise reported so that detailed understanding of the possibilities and nature of impact can be determined. As time passes, the volume and variety of the data sets generated and processed by the business firms has been increasing exponentially. It gives the malicious entities the chance to violate the data properties and capture the sensitive pieces of information.
The techniques used provide the ability to screen the content across varied packets so the signatures being searched for can cross the packet boundaries and are found. Based on the investigation of the security systems and mechanisms, there are certain advantages and disadvantages associated with each system. The existing systems make sure that the networks are protected from any of the external security issues and the periodic reports are delivered based on regular examination. Likewise, the cautions and alerts are issues because of the occurrence of an attack. These systems make use of the ad-hoc approach and are not dependent upon the centralized method to deal with detect and prevent the issues of data leakage and other types of security risks and attacks. The systems work in blend in with the data security devices that the business firms may have implemented in advance over the network channels or as endpoint arrangements. There are various types of network security instruments and controls that may be used, like intrusion detection and prevention systems, firewalls, antimalware devices, encryption, and others.
These systems are developed to provide improved visibility to the security of the data storage systems and furthermore cover the aspects around access control, privilege management, and authentication of the users. The existing security techniques and measures may not be efficient enough to complete such errands and activities. The advanced systems will come with integrated capacities to make sure that the sensitive information isn't exposed to security risks and attacks. There are likewise a few downsides associated with the security systems that must be acknowledged. These systems currently don't have the capabilities to read the encrypted information and the information hidden in the images or in the sound or video files. These can lead to the security and exactness holes if the business firms rely just on a specific security system with the end objective of information security and protection.
Deep packet inspection is developed to make sure that the network packets are properly analyzed and investigated. The limit of these techniques enables firewalls to implement the blocked network access policies. It can have information around the intent of the packet covering the aspects as packet source, destination of the packets, and the specific ports that will be covered by these packets. Deep content inspection then again can determine the information present inside the data packets (Lin, Lee & Chen 2016).
There are numerous challenges identified with dealing with the malicious entities and a number of methods are being developed to manage the issue. One of the essential objectives of the insider attackers is to leak the data to the external entities. As a result, essential share of methods proposed for dealing with the insider threat detection are applicable in detecting and preventing the issues of data leakage. A number of techniques are used and followed to ensure that the alerts are issued to detect and manage the malicious activities of an insider. These may include the use of honey tokens or may likewise utilize knowledge-based algorithms. The structured examination and data fusion is made possible with the use of these techniques and processes. Host-based profiling is one of the effective mechanisms to detect the insider threat and prevent the issues of data leaks that may result as an outcome. Intrusion detection and prevention systems can likewise be implemented internally in the associations to detect the presence of malicious insiders (Harale & Meshram 2016). These systems have the choice to issue alerts and showcase the specific patterns so it becomes easier to get hold of the malicious activities of an insider and furthermore prevent the other security threats that may come up.
6. Future Work (At least 2 pages)
In future, on the basis of the findings, research can be conducted to identify the extent to which social networks are used for increasing digital security in the military among the Malaysian Armed Forces Personnel. A mixed data collection method can be followed along with quantitative and qualitative data analysis techniques.
There are also numerous other technologies that are being developed which can play a massive role in ensuring the safety of the information sets. Blockchain technology, for example, is being aggressively researched upon to promote the transaction security, Big Data, and IoT security (GOOD POINT, EXPAND IT). Such advanced concepts will be explored in the future to make sure that the security and management of the information in the Malaysian Armed Forces is always maintained and improved.
References list
Abraham, S & Chengalur-Smith, I 2019, ‘Evaluating the effectiveness of learner controlled information security training’, Computers & Security, vol. 87, p. 101586.
Andrianov, V, Sivkov, D & Yurkin, D 2020, ‘PROCEDURE FOR IMPLEMENTATION OF DATA LEAKAGE PREVENTION (DLP) SYSTEM TO COMMERCIAL COMPANY FOR INFORMATION NETWORK USING LARGE DATABASE’, Bulletin of Bryansk state technical university, vol. 2020, no. 6, pp. 38–48.
Bishop, M 2016, Information security., Springer International Pu. Certic, S 2018, ‘Two-Factor Authentication Vulnerabilities’, SSRN Electronic Journal.
Ghosh, A & Senthilrajan, A 2019, ‘An Approach for Detecting Spear Phishing Using Deep Packet Inspection and Deep Flow Inspection’, SSRN Electronic Journal.
Haggag, MH 2017, ‘Social Engineering Attacks Detection Techniques: Survey Study’, International Journal Of Engineering And Computer Science.
Haggman, A 2019, ‘Wargaming in Cyber Security Education and Awareness Training’, International Journal of Information Security and Cybercrime, vol. 8, no. 1, pp. 35–38.
Harale, ND & Meshram, DrBB 2016, ‘Data Mining Techniques for Network Intrusion Detection and Prevention Systems’, International Journal of Innovative Research in Computer Science & Technology, pp. 175–180.
Hauer, B 2015, ‘Data and Information Leakage Prevention Within the Scope of Information Security’, IEEE Access, vol. 3, pp. 2554–2565.
Jadhav, M 2018, ‘Prevention of Data Content Leakage’, HELIX, vol. 8, no. 5, pp. 3989–3992.
Krebsonsecurity 2020, Court Ventures — Krebs on Security, Krebs on security.
Lewis, D 2015, ‘Heartland Payment Systems Suffers Data Breach’, Forbes, 6 June, viewed 6 January 2020,
Lin, Y-S, Lee, C-L & Chen, Y-C 2016, ‘A Capability-Based Hybrid CPU/GPU Pattern Matching Algorithm for Deep Packet Inspection’, International Journal of Computer and Communication Engineering, vol. 5, no. 5, pp. 321–330.
Ma, Z 2017, ‘CPSec DLP: Kernel-Level Content Protection Security System of Data Leakage Prevention’, Chinese Journal of Electronics, vol. 26, no. 4, pp. 827–836.
Nagpure, S, Gandhi, A, Varshney, A & Varshney, B 2019, ‘Data Leakage Agent Detection in Cloud Computing’, SSRN Electronic Journal.
National Business Institute 2016, HIPAA compliance boot camp., Nbi, National Business Institute, Eau Claire, Wisconsin.
Nedogarok, AA, Fedorov, NV, Shvychkov, VS & Kalayda, MI 2020, ‘Software implementation of a DLP-system module for monitoring and controlling corporate network traffic using machine learning’, Bezopasnost informacionnyh tehnology, vol. 27, no. 1, pp. 28–39.
Pawar, AV & Dani, AR 2017, ‘Privacy preserving framework for brute force attacks in cloud environment’, International Journal of High Performance Computing and Networking, vol. 10, no. 1/2, p. 91.
Rajasekaran, M, Gupta, A & Sharma, P 2018, ‘Data Leakage Prevention and Detection System’, International Journal of Engineering & Technology, vol. 7, no. 3.12, p. 366.
Rushe, D 2014, JP Morgan Chase reveals massive data breach affecting 76m households, the Guardian, The Guardian.
Singh, A 2017, ‘Data Leakage Detection Using Cloud Computing’, International Journal Of Engineering And Computer Science.
Singh, AK, Gupta, I, Verma, R, Gautam, V & Yadav, CP 2020, ‘A Survey on Data Leakage Detection and Prevention’, SSRN Electronic Journal.
Statista 2018, U.S. data breaches and exposed records 2018 | Statistic, Statista, Statista.
Statista 2020, U.S. data breaches and exposed records 2020 | Statistic, Statista, Statista.
Subhashini, P & B, PR 2015, ‘Confidential Data Identification Using Data Mining Techniques in Data Leakage Prevention System’, International Journal of Data Mining & Knowledge Management Process, vol. 5, no. 5, pp. 65–73.
Tasevski, P 2016, ‘IT and Cyber Security Awareness – Raising Campaigns’, Information & Security: An International Journal, vol. 34, pp. 7–22.
Usha, R, K, P & Surbhi, D 2020, ‘Sensitive Information and Data Leakage Prevention Using Secured Encryption Algorithm’, Aksh - The Advance Journal, vol. 1, no. 1, pp. 21–24.












