Cyber Security Assignment On Phishing Email Frauds In Banking
Question
Task: Choose one category of online fraud crime and produce a report on cyber security assignment focused on the following topics:
- Definition and scale of the crime
- Context of the crime problem
- Common offender methodologies
- Risk factors associated with victimization
- Law enforcement and regulatory responses (specifically, reporting)
- Promising Crime Prevention Approaches (specifically, tips for protecting yourself online)
Answer
Introduction
Banking companies are now using information technologies and computing devices in order to perform business operations where IT-enabled systems help to reduce business problems and perform banking operations effectively. Most of the users are accessing banking accounts into mobile devices and computers where it is difficult to manage and handle security risks and frauds. Criminals have the potential to target banking systems and computing devices used in the banks in order to reduce the confidentiality of sensitive data. Phishing is an online fraud technique used by the criminals in order to get accessibility of the user’s computers and banking accounts. The aim of this report is to find the characteristics of phishing mail frauds that occurred in the banking sectors and propose effective countermeasures.
Definition and scale of the crime
Online fraud refers to the hacking where the hackers develop effective programs and networks in order to gain accessibility of the computer devices. Phishing is a leading online fraud faced by the banking companies and users because the hackers are capable to reduce confidentiality of communication channels and phishing helps to send frauds or spam to the servers so that banking activities can be obtained in a significant manner. Alabdan, (2020) agreed and determined that phishing is defined as a cyber-attack that helps the criminals to decrease accessibility and privacy of businesses and in the case of banking systems, phishing process helps to reduce the security of banking accounts without user's experience.
There are major two parameters of phishing fraud such as hacking and accessing accounts. In order to perform hacking operations, the criminals develop malicious programs and codes which are capable to reduce security and privacy of computing networks linked with the banking systems. On the other side, accessing accounts can be done by transferring frauds developed using malicious programs and users are not capable to manage and address spam mails from their servers due to which accessibility of computer devices and banking systems may be exploited. In terms of effectiveness, phishing fraud is more effective which is able to perform data breach and hacking concerns in the banking sectors and users can suffer from financial problems. Alsayed, &Bilgrami, (2017) reported that in order to scale the impact of a phishing attack, the DREAD model can be used which is capable to provide a way where risk value and impact of cyber-attacks can be analyzed in a significant manner. The below table shows the risk of phishing frauds at various levels of the DREAD framework:
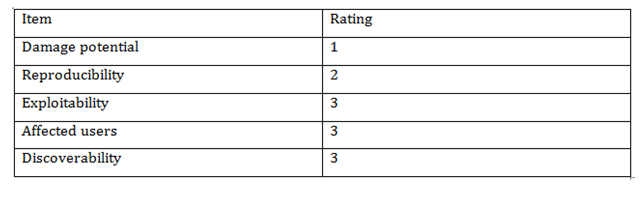
Total risk value= 12
Risk rating= higher
It is found that the risk value of phishing attack is 12 that shows that the impact of phishing frauds on victims and personal details are higher by which the family members can lose accessibility of computer devices and sensitive data stored in the banking servers. Therefore, it is highlighted that banking companies need to focus on frauds and spam mails transferred by the hackers using phishing servers so that banking information of the consumers can be secured from the criminals.
Context of the crime problem
Today, banking companies are delivering online internet banking facilities to consumers by which banking operations can be done using communication channels and internet servers. However, internet and communication servers both are major platforms (environments) that help the criminals to perform online frauds and reduce confidentiality of the personal data. Most of the computing devices are linked through internet and communication servers where it is easy for criminals to develop phishing programs and malware networks and transfer to victim's devices using the internet. Baking companies and users are not capable to find the risk factors producing phishing online frauds in the systems because of this reason the rate of online fraud is growing effectively. Gupta, Arachchilage, &Psannis, (2018) proposed research and determined that internet plays a major role in facilitating online frauds and hacking activities as banking systems are connected with the internet servers where hackers can send frauds and unusual threats from one server to another in less time.
Because of less secured internet connections, more than 60% of the banking companies are suffering from data breach and phishing threats yearly due to which personal data of users may be hacked. Mobile technology, information and communication technologies are not capable to identify phishing threats and online frauds due to which the data loss related problems cannot be managed from banking sectors. There are numerous advantages of the internet for example help to connect two or more computing devices easily, reduce problems in accessing banking accounts, improved communication among companies and users and many more.
However, security or fraud is a major problem linked with the internet by which the offenders or criminals can easily perform hacking operations and reduce the privacy of banking systems. Protecting internet servers from phishing and other online frauds is one of the major scopes of banking companies for which it is important to execute security plans and policies so that level of security can be improved. Olusolade, & Mat Aji, (2020) proposed research and found that hackers target communication technologies and internet servers linked with the banking systems for which proper security tools need to be implemented so that users can confidential their data and baking details.
Common offender methodologies
There are the following types of methods used by the offenders in order to perform phishing online frauds in banking systems:
Email phishing scams
Email phishing is one of the major techniques used by offenders in order to perform phishing operations and reduce privacy. Padmaavathy, (2019) reported that most of the users are using email servers in banking sectors where communication can be done easily and hackers target email servers and transfer fraud signals or mails to the servers so that accessibility of banking systems can be reduced. Moreover, assailants will generally attempt to drive clients vigorously by making a need to keep moving.
Spear phishing
It is capable to target database systems used by the banking companies in order to gain sensitive information of the consumers. Salihovic, Serdarevic, &Kevric, (2018) reported that while using the spear technique, the offenders develop malicious programs which are capable to reduce privacy and help to perform phishing related operations effectively. It's a more top to the bottom adaptation of phishing that requires extraordinary information about an association, including its capacity structure. One of the most popular information penetrates in ongoing history, the hacking of the Democratic National Committee, was finished with the assistance of lance phishing. It is important for the companies to handle and reduce such kinds of threats from the computing devices and banking systems effectively so that data can be secured.
Whaling
The major of whaling method is to help the criminals or offenders for targeting baking servers and computing systems used by the companies so that phishing related operations can be done effectively. More than 50% of the criminals utilize the whaling process for implementing phishing attacks in banking systems and send fake links or malicious programs to the banking servers. Vayansky, & Kumar, (2018) examined that with the help of walling technique, phishing processes can be done effectively and capable to reduce the privacy of the banking accounts of the consumers and companies easily.
Smishing and vishing
With both smishing and vishing, privacy of the mobile devices and communication systems can be hacked by the criminals. Smishingcontains crooks sending instant messages, and vishing includes a hacker discussion. A typical vishing trick includes criminal acting like a misrepresentation hacker telling the casualty that their record has been penetrated. The criminal will at that point request that the casualty gives instalment card subtleties to check their character or to move cash into a 'protected' account by which they mean the criminal's record. Therefore, all these are major methods and techniques used by criminals or offenders in order to perform phishing related threats and online frauds in the banking sectors.
Risk factors linked with victimization
According to Vayansky, & Kumar, (2018), phishing uses malicious programs and transfer frauds or spam to the banking servers and victims are not able to find and address these frauds by which data loss issues may be produced in the society and workplace. There are major three risk factors producing such problems among victims and banking sectors for example lack of awareness, improper security implementation and miss-configuration of banking servers.
Most of the victims are not experienced and aware of cyber-crimes and phishing frauds due to which the hackers can take advantage and perform phishing operations to the banking systems easily. There are numerous types of victims linked with the phishing mail frauds where the hackers gain sensitive data and accessibility of banking accounts, for example, users of mobile devices, small and medium enterprises, stakeholders, third parties linked with the banking systems and employees of the banking sectors. Moreover, weak passwords, the oldest computing software, unauthorized activities and ransomware threats all these are major vulnerabilities that enable the criminals to reduce the security of banking systems easily.
Law enforcement and regulatory responses
The rate of phishing frauds and mails are growing quickly and banking companies are suffering from serious cyber-crimes and security threats. In order to provide responses to phishing frauds, banking companies are trying to provide training to the employees so that awareness related concerns can be managed from the businesses and banking systems. Moreover, companies are communicating with the police departments in order to find the criminals that are sending frauds and spam mails to the users in order to hack banking accounts. Most of the government agencies and associations have hired IT security experts in order to find risk factors from the banking and computing systems.
Adoption of IT experts is a major process that enables the companies to control and reduce the rate of cyber-crimes from businesses in a significant manner. GDPR is a leading security regulation which is provided by the European Union in order to manage and address phishing and other cyber-crimes from the business communities and improve the security of data. Vayansky, & Kumar, (2018) reported that phishing is a cycle of hacking utilized by the hoodlums and fit to give availability to the correspondence networks related to the financial frameworks. Rossi, et al., (2020) inspected that in a phishing danger, the crooks impart spam messages and signs to the clients which don't know about dangers and access the got misrepresentation sends because of which they can convey the availability of records to the programmers.
It is a typical cycle utilized by the digital hoodlums for getting individual data from the financial frameworks and clients can't oversee private subtleties against extortion or spams. Over half of the financial organizations overall are utilizing email workers for correspondence where programmers can adequately perform phishing-related tasks and get the login qualifications of the financial record without the client's information. In order to manage such cyber-crime, companies are adopting and implementing guidelines and security programs provided by GDPR regulations. Moreover, the Scamwatch website can be followed by the banking companies that deliver proper security measures and IT experts in order to deal with phishing emails and frauds. There are numerous security laws and legislations implemented in order to manage phishing related securitythreats which are highlighted below:
- The Data protect act 2018
- Cyber-crime Act 2001
- Computer Misuse Act of 1990
Promising crime prevention approaches
From the above discussion, it is demonstrated that criminals target email servers and communication channels used by the banking companies for which it is important to examine frauds and spam signals from the systems. Lack of awareness and improper security systems both are major problems linked with the banking companies due to which the phishing and frauds are produced in the banking systems. According to deontological ethical theory, employees and IT experts of banking companies need to follow their duties and responsibilities properly so that internal threats can be managed and private bank details of the users may be secured effectively. POP, (2018) determined that for improving the security of banking systems, users need to update their computing systems and software because the oldest systems are not capable to protect data and cannot manage frauds easily. It is prescribed that financial organizations need to convey preparing and warnings to the purchasers so mindfulness related issues can be overseen.
A firewall is the main security strategy that is able to recognize fakes and spams from the financial frameworks that ought to be created and actualized in the financial workers viably. On the opposite side, encryption is more successful that gives a way where banking networks can improve the privacy of the correspondence channels (Vayansky, & Kumar, 2018). Accordingly, all these are successful security procedures that ought to be remembered for the financial frameworks.
Moreover, banking companies need to develop a risk assessment plan which is a common security approach that enables the management to find risk factors producing cyber-crimes and online frauds in the banking systems. All these are effective approaches and techniques that can help to reduce phishing frauds and improve the security of the banking systems.
Conclusions
It may be summarized that phishing is a major online fraud occur in the banking systems for which proper security measures and plans need to be implemented by the banking communities. This research provided a way to understand the impacts of phishing online frauds on banking systems and identified the security risks related to the banking servers. It is found that internet is a leading platform used by the offenders in order to perform phishing operations because banking servers are directly connected to the computing systems using the internet where hackers can access both computing devices and banking accounts easily. Portable innovation, data and correspondence advancements are not able to distinguish phishing dangers and online cheats because of which the information misfortune related issues can't be overseen from banking divisions. There are various favourable circumstances of the web for instance help to interface at least two registering gadgets effectively, diminish issues in getting to banking accounts, improved correspondence among organizations and clients and some more. So, it is recommended that banking communities should follow GDPR guidelines and implement risk assessment plans so that phishing issues from banking systems may be reduced.
References
Alabdan, R. (2020). Phishing Attacks Survey: Types, Vectors, and Technical Approaches. Future Internet, 12(10), 168.
Alsayed, A., & Bilgrami, A. (2017). E-banking security: Internet hacking, phishing attacks, analysis and prevention of fraudulent activities. Int. J. Of Emerg. Techn. and Adv. Activ, 7(1), 109-115.
Gupta, B. B., Arachchilage, N. A., & Psannis, K. E. (2018). Defending against phishing attacks: a taxonomy of methods, current issues and future directions. Telecommunication Systems, 67(2), 247-267.
Ololade, B. M., Salawu, M. K., & Adekanmi, A. D. (2020). E-Fraud in Nigerian Banks: Why and How?. Journal of Financial Risk Management, 9(3), 211-228.
Olusolade Aribake, F., & Mat Aji, Z. (2020). Modelling the Phishing Avoidance Behaviour Among Internet Banking Users in Nigeria: The Initial Investigation. Journal of Computer Engineering and Technology, 4(1), 1-17.
Padmaavathy, P. A. (2019). CYBER CRIMES: A THREAT TO THE BANKING INDUSTRY. International Journal of Management Research and Reviews, 9(4), 1-9.
POP. (2018). Crime Prevention studies. Retrieved from: https://popcenter.asu.edu/content/crime-prevention-studies
Salihovic, I., Serdarevic, H., &Kevric, J. (2018). The Role of Feature Selection in Machine Learning for Detection of Spam and Phishing Attacks. In International Symposium on Innovative and Interdisciplinary Applications of Advanced Technologies, 12(6), 476-483.Vayansky, I., & Kumar, S. (2018). Phishing–challenges and solutions. Computer Fraud & Security, 2018(1), 15-20.












