Cyber security assignment on the types of security tools required to protect software infrastructure
Question
Task: How can cyber security assignment research skills be used to determine effective cyber security tools to protect software infrastructure?
Answer
Introduction
Nobody anticipated that the proliferation of the internet in the early 1970s would result in such a significant shift in the globe. The Internet is now deeply ingrained in our routines and cannot be imagined without it. The concept of "cyber" first emerged about the time when people all over the globe began communicating with one another over the internet. The purpose of utilising the internet in the first place is to facilitate the simple sharing of data, information, and expertise. When data is sent via the internet, maintaining its confidentiality becomes an increasingly important concern. Network and data are the two most important components that make up the cyberworld[1]. Cyber security was originally conceived as a means of preventing eavesdropping on computer networks and maintaining the confidentiality of stored data. In this cyber security assignment, we have examined the numerous types of assaults that may be carried out by hackers, as well as the various ways that can be used to defend against these attacks. The field of cyber security has advanced to the point that there are now specific standards and regulations established by numerous organisations all around the world. The goal is to safeguard the many devices that we use on a daily basis, as well as the software that is used by a variety of businesses and the apps that operate on several different platforms. Data leaking, illegal access, web-based harassment for monetary rewards, abusing infrastructure, and gaining a technological edge over competing businesses are just a few of the primary outcomes that may occur from cyber assaults.
Cisco, Juniper, Aruba, and Amazon Web Services (AWS) were among the first companies to establish a robust foundation of cyber security and create hardware and security model. These companies have implemented cutting-edge security mechanisms throughout their networks as well as the physical equipment that may be found in any company. On the other side, there have businesses like as Norton, AVG, Avast, and Kaspersky, amongst others, that are always working on identifying the different malwares and finding solutions to those weaknesses[3]. These apps perform continuous monitoring of both incoming and outgoing packets in order to guarantee that any potential security risk may be located and neutralised as soon as feasible. Mobile devices are now the target of the majority of the cyber assaults that we see today. The goal of these attacks is to obtain access to users' personal and financial information. After gaining access to this information, the perpetrators of the assault will either abuse the victim for financial gain by bothering them or immediately seize access to the victim's bank accounts. The same is true for large IT organisations, where data breaches may provide competitors an edge in terms of both technology and business, causing the former to lose large contracts. The cyber security assignmentresearch shows the banking industry is also negatively impacted; hence, the adoption of cyber security should be an essential component of everyone's daily routine. Let us have a look at some of the models and standards that are utilised in the field of cyber security, as well as the numerous instruments that are employed for the goal of assessing security.
Models and Standards
The cyber security assignment findings show the term "cyber security standards" refers to the procedures or frameworks that have been put into place in order to safeguard different companies or individual users from the dangers that may be found in the digital environment. Users who are connected to the internet are the primary target audience for the models and standards that have been developed with this purpose in mind. All of these different security models and standards are governed by a singular organisation that goes by the acronym NIST[4]. Following this, we will proceed to categorise the various cybersecurity models.
Stride Threat Model
Microsoft's Stride Threat Model, which the firm devised and developed on their own, is widely regarded as one of the most well-known and generally recognised models in the world of cyber security[2]. The model was created by Microsoft. The major purpose of this cyber security assignmentmodel is to forecast assaults and classify them according to the level of severity posed by the threat. The figure that is to come provides an illustration of the Stride model.
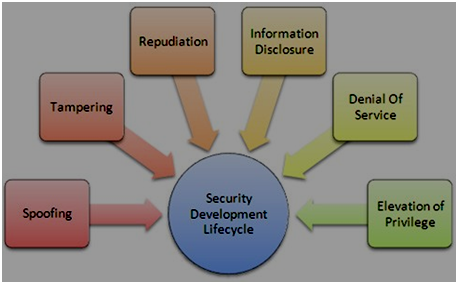
Figure 1: Stride Threat Model
(Source: Self-Created)
Spoofing It is necessary for a user to authenticate the request before he may provide another user access to his data. The identification of the other party is a critical factor in determining not just the safety but also the completeness of the data. This confidence is put at risk whenever cybercriminals make the false promise that they can provide a secure channel for their data[6].
Tampering Since it is anticipated that the overall level of server security would significantly improve over the course of the next several years, the vast majority of hackers have shifted their focus from assaulting the principal servers to assaulting the servers that have weaknesses. They are always monitoring the network in search of weak spots that they may exploit in order to attack these systems. After gaining access to unprotected network devices, the attackers' next goal is to hide either their identity or the flaws they've uncovered by altering data, such as log files, to disguise their tracks.
Repudiation When an attacker uses this method, they try to hide their actions by changing or deleting information about a transaction or login. For instance, the adversary may revoke a purchase transaction so that the target is not alerted to the fact that they are under assault[7]. Information Disclosure When we connect to the internet, many of the browsers and programmes we use need us to input our user credentials before they will allow us to advance. This credential information is often saved in the cache of the browser. Hackers in this sort of assault often steal private user information for the purpose of reselling it online.
Denial of Service The goal of this sort of assault is to overwhelm the victim's servers to the point where they either crash or cease responding to queries. The cyber security assignment research reports this kind of assault is often conducted out with the intention of impeding the web-based operations of an organisation. Elevation of Privilege This form of attack is very similar to spoofing; however, in order for the attacker to get access to the system, they must grant themselves certain extra rights.
CIA Model
The CIA model may be broken down into three primary stages, each of which is discussed in more detail below.
1. Confidentiality
Privacy is a close approximation to the concept of confidentiality. In this regard, we are required to take precautions in order to allow the sensitive data to be accessible by the authorised users, while simultaneously preventing the data from being accessed by those who are not permitted to do so or by hackers. The risk that a piece of data poses if it is obtained by an unauthorised party may be used to classify the data, and the level of protection that should be afforded to that data can be determined based on that classification. Some instances identified on this cyber security assignment include, user credentials may be of the biggest value to the companies, but log files may be of a lesser relevance to the organisations.
2. Availability
Maintaining all of the hardware, carrying out any required repairs, and checking to see that the software and operating system are free from any conflicts are the most effective ways to maximise availability. In this setting, it is crucial to always use the most recent versions of available software and hardware. In order to prevent any bottlenecks, the bandwidth that is made available should be sufficient to deal with the request[9]. In addition, disaster recovery procedures have to be in place in order to facilitate the seamless transition between environments in the event of an outage. It is important to have backup plans in place for sensitive data in the event that the original data is deleted by mistake. The cyber security assignment shows that additional security measures had to be put into place to protect the systems against DoS and Network assaults.
3. Integrity
The integrity of the data may be preserved by the implementation of procedures designed to guarantee the data's precision, coherence, and dependability over the whole of its storage time. The data should not be changed while it is in transit, and precautions should be made to prevent hackers and other malicious actors from tampering with it afterwards. It is possible to avoid this kind of data modification by putting in place safeguards such as access restrictions and file permissions. Some of the data may also be encrypted in such a way that even if it were to get into the wrong hands, the person trying to decrypt it wouldn't be able to do so[5]. In addition to this, vital data should be backed up on a regular basis in order to make it simpler to retrieve data that has been lost or damaged.
cyber security assignmentCVE & CWE
• CVE
The entire public has access to a list of vulnerabilities and exposures that is titled “Common Vulnerabilities and Exposures”. Every item on this list has a number that identifies it, an explanation of what it is, and references that offer information about the cybersecurity flaws that are present in the software product that it is referring to. It corrects a vulnerability that manifests itself each time a specific instance of the software is accessible.
• CWE
“The Common Weakness Enumeration”, sometimes known as CWE, is an initiative that offers a standardised forum for sharing the system's full list of hardware and software vulnerabilities.
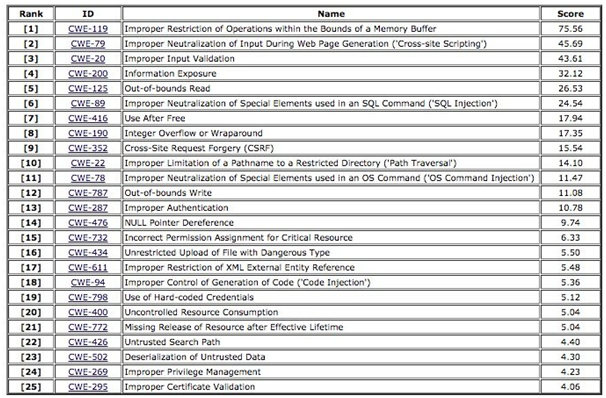
Figure 2: Represents the CWE's top 25
(Source: virsec.com, 2019)
CAPEC
In order to fully comprehend the vulnerabilities and to add advanced security safeguards prior to the programme entering the production process, programmers, testers, and analysts should use the “Common Attack Pattern Enumeration and Classification” or CAPEC.
ISO/IEC27001
To govern the safety of information sent over the network, the “International Organization for Standards (ISO)” came up with the “ISO/IEC 27001 international standard”. This standard is known as an “information security management system (ISMS)”. It covers information on the establishment of the information security management system, as well as its “implementation, maintenance, and maintenance procedures (ISMS)”[8]. Its purpose is to assist businesses already in possession of information collecting and processing systems in making such systems more secure. Following the conclusion of a comprehensive security review, organisations that satisfy the prerequisites outlined by “ISO/IEC 27001” have the option of having their company officially certified.
Security Assessment Tools
The cyber security assignment shows that in order to keep up with the rapid development of technology and the increasing sophistication of its components, the instruments that are used to safeguard that technology have likewise become more sophisticated. In order to meet the requirements of these various security measures, the market offers a wide variety of security products. The vast majority of these tools may be used without charge; however some ones are protected by a pay wall. The majority of the premium products are extraordinarily complicated and are developed with the intention of protecting a big enterprise from the majority of security threats. Instead, we will be concentrating on open source tools like as SNORT and NESSUS since they are the most widely used tools and are used by a great number of companies.
Network Intrusion detection System
In order to identify any potentially harmful actions taking place on the network, a “Network-based Intrusion Detection System”, abbreviated NIDS, is used. “The Network Intrusion Detection System (NIDS)” might be based on either software or hardware. The majority of the time, NIDS works on two different interfaces simultaneously[10]. Both reporting and control are done via the other interface, whereas the first interface is utilised to actively listen to the network. “The Network Intrusion Detection System (NIDS)” inspects each and every packet that moves across the whole network for malicious behaviour and will issue an alert if it identifies anything that is acting in an unusual manner.
Snort
Snort is a tool that is both open source and free, and it is the network intrusion detection system (NIDS) that is utilised the most. In the year 1998, Martin Roesch was the one who first conceived of the concept. CISCO has taken over management of the Snort network intrusion detection and prevention system since since the company completed its acquisition of Sourcefire in 2013[11]. It is able to do real-time network traffic analysis as well as record packets that are sent and received on the network. It can detect a wide range of security threats, from denial-of-service (DOS) attacks to CGI attacks, OS fingerprinting, buffer overflows, and more, and it can also do other security-related tasks like content matching and searching. Snort makes use of a flexible programming language that enables the construction of rules that can be applied to a network in order to more effectively manage the flow of network traffic. Thesecyber security assignment rules may be implemented by the software to a network in order to improve its ability to govern network traffic.
In addition to having the capability to provide real-time warnings to users, it is outfitted with a detection engine that operates on the principle of an architecture that is built on plugins. This tool was built to detect a broad range of security violations, and it made utilization of the concept of adaptable terminology in order to recognise the many different forms of information accumulation that might be obtained[12]. The end goal of this tool was to recognize a wide variety of various cybersecurity incidents. Before a user can make full use of Snort, they will need to do certain fine-tuning tasks in order to indicate how the programme should behave in each of its three major modes. These cyber security assignmenttasks are essential in order for the user to be able to make full use of Snort.
Figure 3: Snort Intrusion Detection System on Linux
(Source: howtogeek.com, 2020)
SNORT operates based on the following three fundamental modes:
Sniffer mode:During this mode, the programme does nothing more than read all of the packets that are moving over the network and then shows them on the network for the administrator of the network to examine[13].
Packet logger mode:In this mode, the programme does nothing more than create a log of the packets that are stored on the disc.
“Intrusion Detection Mode for the Network (NIDS)”:This is the most significant mode in this programme that is employed to do assessment of the network activity and discover any abnormalities that may be present in the network.
Integrating and setting up Snort
In the next part of this guide, we will cover the steps that must be taken in order to successfully install Snort on a computer that is running the Windows operating system. The WinPcap packet capture programme, the Snort installer, and the Snort rules package are the three primary elements that must be present for the successful completion of the Snort installation process on a Windows-based computer[14]. Installing Snort on a Windows computer comes with a number of benefits, and this is one of them. We are also able to configure a syslog server in the event that we find ourselves in need of a syslog output.
Figure 4: Installing Snort
(Source: linuxhint.com, 2022)
For developers working in the fields of Network Security, Computer Networks, and system software development, as well as for Intrusion Analysts who are tasked with the job of implementing and operating IDS, the fact that Snort is open source software and a widely popular NIDS makes it a very beneficial and worthwhile learning experience. Intrusion Analysts may handle and utilise Snort more efficiently after being familiar with its inner workings, which is a benefit of having this knowledge. An overview of Snort's architecture is provided here, with a focus placed on the workings, features, and inner-level elements that have gone into the creation of Snort.
Snort's Architecture
The cyber security assignmentshows Snort is built using a large number of internal components that are highly adjustable and have a significant impact on the software's overall performance. In order to have Snort work properly and monitor for intrusions in an efficient manner, one must have a solid grasp of the underlying architecture of Snort[15]. The design of Snort comprises five important components, each of which is essential to the process of intrusion detection.
Steps for Installation
Step 1: Installer packages are currently being downloaded.
First, the user will need to go online and download the Snort installation package as well as the Snort rules package. Check to verify that customers are obtaining the most recent package versions of the installer.
Step 2: Installer packages are currently being downloaded.
First, the user will need to go online and download the Snort installation package as well as the Snort rules package. Check to verify that customers are obtaining the most recent package versions of the installer.
Step 3: Performing checks on the installation
Following the procedures outlined below will allow us to validate the installation of all three packages after it has been completed.
• To begin, user need to go to the Snort programme directory, which is located at c:cdSnortbin.
• After that, verify the version of Snort that is currently installed by using the following command: c:Snortbin>snort -V
• The "-V" should be capitalised, and all it does is verify whether the directory in question has the most recent version of snort installed[16]. The output will be available to us if the command is executed without error.
• In addition the cyber security assignment shows, before users can configure Snort to listen on the appropriate interfaces, they need to do a cross-check on the network adapters that have been installed in our system. This will allow us to identify any problems. Users will be able to see the whole list of interfaces if they use the following command: snort -W C:/Snort/bin/snort
Step 4: Changing the settings in the snort.conf file to configure Snort
Next, users will need to configure Snort by making changes to the snort.conf file, which can be found in the c:Snortetc directory. Due to the fact that the operating system is in a text format, users are able to change it using either WordPad or notepad. Modifications to the configuration file may be made in one of nine distinct phases
I. Configure the network settings and variables.
? The IP range of our home network has been substituted into the HOME NET statement. Using an expression in CIDR format is one way to accomplish this goal.
? The declaration of EXTERNAL NET is being updated to read!
? $HOME NET
? Modifying the RULE PATH variable definition so that it corresponds with the path of the Snort Rules file that we really use.
? Modifying PREPROC RULE PATH so that it corresponds to the real route that preproc rules take[17].
? The SO RULE PATCH statement is being hashed out since Windows does not employ a shared object rule.
II. Changing the settings on the decoder
There is no menting the first line and adding the path in the code will allow us to make c:Snortlog the default location for log files.
III. Setting up the Detection Engine's Conneed to make any adjustments to the decoder's settings for the vast majority of users.
Within the detecting engine, there is no need to make any modifications to the setup settings.
IV. Configuring libraries that are dynamically loaded
Modifying the library is path on Windows to reflect the new location of the files.
V. Adjusting the settings for the preprocessors
VI. Assembling Plugins for Output
VII. Modification of the existing Rule set
VIII. Modifying both the preprocessor and the decoder's rule set
IX. Modifying the set of rules for shared objects
CVEanalysisofSnort
With the use of Snort, it may be possible to detect and prevent intrusion attempts. If required, suspicious network activity may be readily recorded and later banned. With the use of OpenAppID detectors and rules, the Snort programme can recognise and filter out certain applications. If you're using the graphical user interface of the pfSense® software, you may install the package by going to System > Package Manager. Rules, or detection signatures, are used by Snort to identify threats. Snort may be used with either custom-made rules or a collection of pre-made rules. To access the rule set downloads, click on the Global Settings tab. After selecting the option for either the Snort VRT or the Emerging Threats Pro rules, a new window will open where the subscription key may be input.
A number of rule sets may be downloaded, but only under the following conditions: If a paid subscription is supplied for the Snort VRT rules, the GPLv2 Community rules will also be downloaded in tandem with the Snort VRT rules file[18]. When you sign up for Emerging Threats Pro, you have access to both the Pro rules and the Open rules as well. The limitations of the free edition are removed once you activate Emerging Threats Pro.
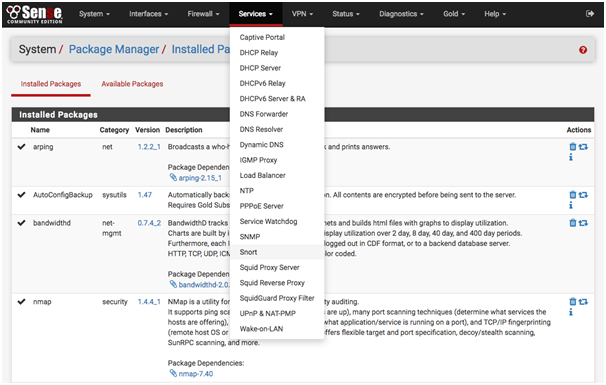
Figure 5: Snort Configuration
(Source: docs.netgate.com, 2020)
cyber security assignment Snort Analysis using STRIDE model
Even though SNORT was designed to be a tool that would assist in the protection of the network, the tool itself is not immune to the dangers that may potentially be encountered. SNORT has been determined to contain a huge number of vulnerabilities, all of which are mentioned on the CVE list that can be found in the part that was just referred above. These vulnerabilities were identified by cybersecurity experts. By installing the most current version of SNORT, the vast majority of these security flaws should be fixed.
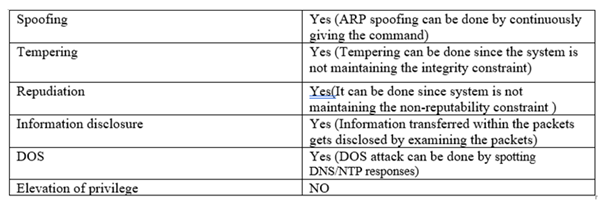
Figure 6: Analysis of Snort using STRIDE model
(Source: linuxhint.com, 2022)
Network Vulnerability Scanner
“A Network Vulnerability Scanner”, often known as an NVS, is a piece of software that can examine an entire infrastructure in search of previously unknown security flaws and report them to an administration of the network[19]. A quick grasp of a company's current safety precautions may be gained via this analysis, allowing the firm to further strengthen its defences against network attacks and adopt further preventative actions. To begin the process of securing a network, the initial step often entails installing and running a vulnerability scan throughout the whole network. From the cyber security assignment research, it is clear that A network vulnerability scanner offers the user or organisation the opportunity to examine their own network for any potential breaches in network security and contributes to the network's overall protection.
Nessus
Most people use Nessus since it is a free and open-source Network vulnerability scanner. It examines every device in the company's network, including those that are linked to the internet, in search of any potential vulnerability. It is capable of running about 1300 tests throughout the whole of the network on which it has been deployed[20]. Before beginning the installation of Nessus, we need to examine our computer to ensure that it satisfies the prerequisites, both in terms of its hardware and its software, for a successful installation of Nessus.
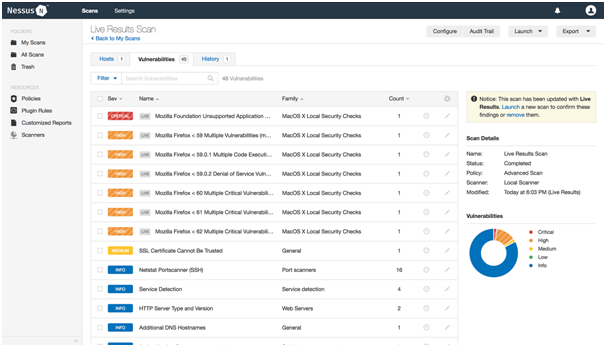
Figure 7: Downloading Nessus
(Source: tenable.com, 2021)
Integrating and setting up Nessus
After obtaining Nessus from the internet, setting it up is a simple procedure. To continue, we will install WinPcap on the workstation once we have downloaded and installed the Nessus package. Nessus will prompt the user to install WinPcap if it is not already present on the target computer. Once everything has been properly installed, the Application window will show up, as seen in the following image[21].
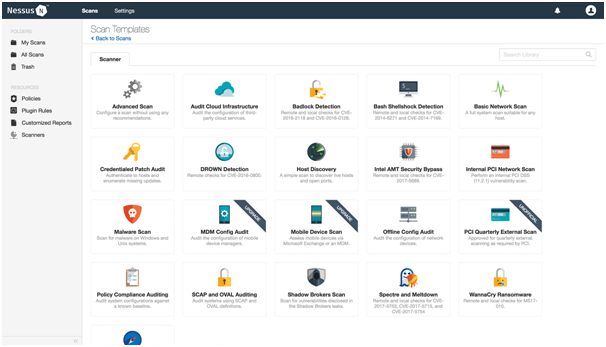
Figure 8: menu screen of Nessus
(Source: tenable.com, 2021)
DifferentScans
The above cyber security assignmentscreenshot demonstrates that the programme supports a wide variety of distinct scans, as can be seen from the options that are shown to the user. In the next parts, we are going to examine some of these scans.
|
Basic Network Scan |
The first thing that has to be done in order to do a fundamental network scan is to provide a list of IP addresses that may be accessed on the network. After then, Nessus will investigate each of those IP addresses to determine whether or not the network has any vulnerability[22]. In addition, the solutions are provided in order to safeguard certain Internet Protocol (IP) addresses. |
|
Port Scan |
During this phase of the scan, Nessus examines a range of IP addresses or ports in search of potential security flaws[23]. In order to reduce the amount of time necessary for scanning the whole network, we may also choose to focus on a specific port. |
CVE & CWE analysis of Nessus
Despite the fact that Nessus is a vulnerability scanner, it is still vulnerable to assaults on the network. In the snapshot that follows, we can see a list of the vulnerabilities that Nessus has discovered.
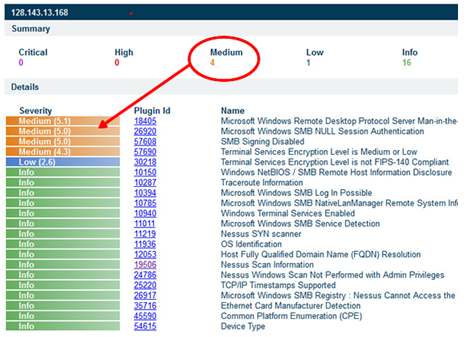
Figure 9: vulnerability Report of Nessus
(Source: virginia.service-now.com, 2019)
Stride analysis of Nessus
Performing threat modelling right at the beginning of a project allows for a more objective perspective on the work that is being done. In additionthe cyber security assignment shows, it will be helpful in determining the locations of any potential security flaws[26]. After a broad concept for the design has been decided upon, the following phase in the process may be carried out. “PASTA, VAST, Trike, OCTAVE, and NIST” are some other methods that may be employed in lieu of STRIDE because of the qualities that come with each of these methods individually[24]. Some are more suited to some sectors of information technology than others, such as applications rather than networks.
There is no one approach to threat modelling that is optimal for use in every situation. On the other hand, the DevOps team need to be incentivized to alter the pre-existing threat modelling methodologies so that they are more suitable to the requirements of their organisation[27]. Remember that the threat model is a living document that has to be inspected and updated on a regular basis. This is important for the future. After a comprehensive system-wide threat model has been developed, a secure engineering design requirement may call for the employment of miniature threat models[25].
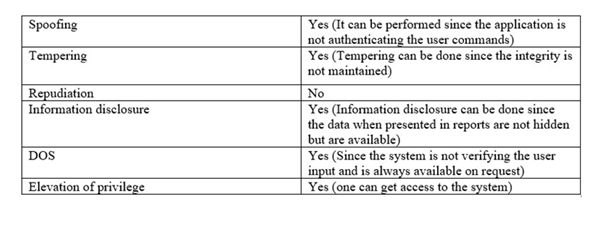
Figure 10: Stride analysis of Nessus
(Source: virginia.service-now.com, 2019)
Conclusion
When utilising the internet, we were aware of the many potential dangers that may befall anybody at any time. We were also aware of the many models and standards that had been developed by a variety of organisations with the purpose of protecting data sent over the internet. On the other hand, as a result of developments in technology, the vast majority of platforms for the storage of data and the hosting of applications have begun shifting into the cloud. The term "cloud technology" refers to nothing more than safe data centres, which use the highest levels of security to protect the stored data and are designed to be readily accessible from any location in the globe. The need of safeguarding both individual electronic devices and the whole network was brought to our attention by this cyber security assignment. In the field of intrusion detection systems, Snort is without a doubt one of the top open source technologies that are now accessible to reduce danger. On the other hand, we have an incredible tool called Nessus that assists in doing a full scan of the whole network, beginning with the initial setup and continuing all the way through to the final user. Anyone, from sole proprietors to multinational corporations, may benefit from these cutting-edge open-source technologies in their work.
No one could have predicted that by the year 2022, investments in cyber security would reach an estimated value of 120 billion dollars. Each and every company is putting a significant amount of focus on the optimization and security of its digital assets. When it comes to utilising the internet, there are many potential dangers that one should be aware of, and I think that everyone should be aware of these risks. The cyber security assignmentconsluides that raising awareness, helps cut down on the number of assaults that are carried out and make the world a better and safer place to use the internet.
Reference list
[1] A. Georgiadou, S. Mouzakitis, and D. Askounis, “Assessing Mitre ATT&CK risk using a cyber-security culture framework,” Sensors, vol. 21, no. 9, p. 3267, 2021. Available at:
https://www.mdpi.com/1424-8220/21/9/3267/pdf?version=1620550566 [Accessed on: 07.09.2022]cyber security assignment
[2] B. Uchendu, J. R. C. Nurse, M. Bada, and S. Furnell, “Developing a cyber security culture: Current practices and future needs,” Computers & Security, vol. 109, p. 102387, 2021. Available at: https://arxiv.org/pdf/2106.14701 [Accessed on: 07.09.2022]
[3] A. Georgiadou, S. Mouzakitis, and D. Askounis, “Designing a cyber-security culture assessment survey targeting critical infrastructures during covid-19 crisis,” International Journal of Network Security & Its Applications,cyber security assignment vol. 13, no. 1, pp. 33–50, 2021. Available at: https://arxiv.org/pdf/2102.03000 [Accessed on: 07.09.2022]
[4] G. Penchev, “Planning and implementing change in Cyber Security Network organisations,” Information & Security: An International Journal, vol. 50, pp. 89–101, 2021. Available at: https://www.researchgate.net/profile/Brett-Van-Niekerk/publication/342501668_A_Change_Management_Perspective_to_Implementing_a_Cyber_Security_
Culture/links/5f05b2aa45851550509488b3/A-Change-Management-Perspective-to-Implementing-a-Cyber-Security-Culture.pdf [Accessed on: 07.09.2022]
[5] T. Gundu, M. Maronga, and D. Boucher, “Industry 4.0 businesses environments: Fostering cyber security culture in a culturally diverse workplace,” Kalpa Publications in Computing, 2019. Available at: https://wvvw.easychair.org/publications/download/RNxQ [Accessed on: 07.09.2022]
[6] H. Aldawood and G. Skinner, “Educating and raising awareness on Cyber Security Social Engineering: A literature review,” 2018 IEEE International Conference on Teaching, Assessment, and Learning for Engineering (TALE), cyber security assignment2018. Available at: https://www.researchgate.net/profile/Hussain-Aldawood/publication/330293734_Educating_and_Raising_Awareness_on_Cyber_Security_Social_Engineering
_A_Literature_Review/links/5d9ae3c192851c2f70f21bf8/Educating-and-Raising-Awareness-on-Cyber-Security-Social-Engineering-A-Literature-Review.pdf [Accessed on: 07.09.2022]
[7] X. Zhu and Y. Zhu, “Extension of ISO/IEC27001 to mobile devices security management,” Communications in Computer and Information Science, pp. 27–35, 2019. Available at: https://link.springer.com/chapter/10.1007/978-981-13-6621-5_3 [Accessed on: 07.09.2022]
[8] N. A. Kamaruddin, I. Mohamed, A. D. Jarno, and M. Daud, “Cloud security PRE-ASSESSMENT model for cloud service provider based on ISO/IEC 27017:2015 additional control,” International Journal of Innovation and Industrial Revolution, vol. 2, no. 5, pp. 01–17, 2020. Available at: http://www.ijirev.com/PDF/IJIREV-2020-05-12-01.pdf [Accessed on: 07.09.2022]
[9] P. Boonkrong and C. Nuansomsri, “Fuzzy rule-based risk management under ISO/IEC27001: 2013 standard for information security,” JCST, vol. 8, no. 1, 2018. Available at: https://www.researchgate.net/profile/Pichit-Boonkrong/publication/326093088_Fuzzy_rule-based_risk_management_under_ISOIEC270012013_standard_for_information_security/links/5b38191faca272
0785fd8dd7/Fuzzy-rule-based-risk-management-under-ISO-IEC270012013-standard-for-information-security.pdf [Accessed on: 07.09.2022]cyber security assignment
[10] H. Asad and I. Gashi, “Dynamical analysis of diversity in rule-based open source network intrusion detection systems,” Empirical Software Engineering, vol. 27, no. 1, 2021. Available at: https://link.springer.com/article/10.1007/s10664-021-10046-w [Accessed on: 07.09.2022]
[11] G. K. Bada, W. K. Nabare, and D. K. Quansah, “Comparative analysis of the performance of network intrusion detection systems: Snort, suricata and bro intrusion detection systems in perspective,” International Journal of Computer Applications, vol. 176, no. 40, pp. 39–44, 2020. Available at: https://www.researchgate.net/profile/Williams-Kwame-Nabare/publication/343022781_Comparative_Analysis_of_the_Performance_of_Network_Intrusion_Detection
_Systems_Snort_Suricata_and_Bro_Intrusion_Detection_Systems_in_Perspective/links/606a513ba6fdccad3f71
51c7/Comparative-Analysis-of-the-Performance-of-Network-Intrusion-Detection-Systems-Snort-Suricata-and-Bro-Intrusion-Detection-Systems-in-Perspective.pdf [Accessed on: 07.09.2022]
[12] D. Zhang and S. Wang, “Optimization of traditional Snort Intrusion Detection System,” IOP Conference Series: Materials Science and Engineering, vol. 569, no. 4, p. 042041, 2019. Available at: https://iopscience.iop.org/article/10.1088/1757-899X/569/4/042041/pdf [Accessed on: 07.09.2022]cyber security assignment
[13] S. A. Shah and B. Issac, “Performance comparison of intrusion detection systems and application of machine learning to Snort System,” Future Generation Computer Systems, vol. 80, pp. 157–170, 2018. Available at: https://arxiv.org/pdf/1710.04843 [Accessed on: 07.09.2022]
[14] H. Haugerud, H. N. Tran, N. Aitsaadi, and A. Yazidi, “A dynamic and scalable parallel network intrusion detection system using intelligent rule ordering and network function virtualization,” Future Generation Computer Systems, vol. 124, pp. 254–267, 2021. Available at: https://www.sciencedirect.com/science/article/pii/S0167739X21001874 [Accessed on: 07.09.2022]
[15] L. S. Sharma and A. Gupta, “A categorical survey of state-of-the-art intrusion detection system- Snort,” International Journal of Information and Computer Security, vol. 11, no. 1, p. 1, 2019. Available at: https://www.researchgate.net/profile/Alka-Gupta-11/publication/344836235_A_categorical_survey_of_state-of-the-art_intrusion_detection_system-Snort/links/606465ae299bf173677e28c5/A-categorical-survey-of-state-of-the-art-intrusion-detection-system-Snort.pdf [Accessed on: 07.09.2022]
[16] A. Tasneem, A. Kumar, and S. Sharma, “Intrusion detection prevention system using Snort,” International Journal of Computer Applications, vol. 181, no. 32, pp. 21–24, 2018. Available at: https://www.researchgate.net/profile/Shabnam-Sharma-2/publication/329716671_Intrusion_Detection_Prevention_System_using_SNORT/links/5ef984e8299bf18816
eff4ae/Intrusion-Detection-Prevention-System-using-SNORT.pdf [Accessed on: 07.09.2022]cyber security assignment
[17] A. Erlansari, F. F. Coastera, and A. Husamudin, “Early intrusion detection system (IDS) using Snort and telegram approach,” SISFORMA, vol. 7, no. 1, pp. 21–27, 2020. Available at: https://pdfs.semanticscholar.org/327a/aa762f4db17b3a3960811b0e419dbda70991.pdf [Accessed on: 07.09.2022]
[18] R. F. Olanrewaju, B. U. Islam Khan, A. R. Najeeb, K. N. Ku Zahir, and S. Hussain, “Snort-based smart and swift intrusion detection system,” Indian Journal of Science and Technology, vol. 11, no. 4, pp. 1–9, 2018. Available at: https://www.academia.edu/download/60710997/120917-289847-2-PB20190926-80504-1oicvgz.pdf [Accessed on: 07.09.2022]
[19] I. Chalvatzis, D. A. Karras, and R. C. Papademetriou, “Evaluation of security vulnerability scanners for small and Medium Enterprises Business Networks Resilience Towards Risk Assessment,” 2019 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), 2019. Available at: https://core.ac.uk/download/pdf/195277590.pdf [Accessed on: 07.09.2022]
[20] D. Karabaševi?, D. Stanujki?, M. Brzakovi?, M. Maksimovi?, and M. Jevti?, “Importance of vulnerability scanners for improving security and protection of the web servers,” BizinfoBlace, vol. 9, no. 1, pp. 19–29, 2018. Available at: https://scindeks-clanci.ceon.rs/data/pdf/2217-2769/2018/2217-27691801019K.pdf [Accessed on: 07.09.2022]
[21] R. Antrobus, B. Green, S. Frey, and A. Rashid, “The forgotten I in IIOT: A Vulnerability Scanner for industrial internet of things,” Living in the Internet of Things (IoT 2019), 2019. Available at: https://eprints.lancs.ac.uk/id/eprint/132771/1/PiVOTScan.pdf [Accessed on: 07.09.2022]cyber security assignment
[22] V. Balatska and M. Shabatura, “Exploration of computer network by Vulnerability Scanner nessus,” Bulletin of Lviv State University of Life Safety, vol. 20, pp. 6–11, 2019. Available at: https://journal.ldubgd.edu.ua/index.php/Visnuk/article/download/1581/1595 [Accessed on: 07.09.2022]
[23] C. R. Harrell, M. Patton, H. Chen, and S. Samtani, “Vulnerability assessment, remediation, and automated reporting: Case Studies of Higher Education Institutions,” 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), 2018. Available at: https://par.nsf.gov/servlets/purl/10086712 [Accessed on: 07.09.2022]
[24] I. Chalvatzis, “Reproducible modelling and simulating security vulnerability scanners evaluation framework towards risk management assessment of small and Medium Enterprises Business Networks,” Indian Journal of Science and Technology, vol. 13, no. 37, pp. 3910–3943, 2020. Available at: https://pure.port.ac.uk/ws/portalfiles/portal/25132332/IJST_2020_868.pdf [Accessed on: 07.09.2022]
[25] I. S. M. A. I. L. A. IDRIS, U. M. A. R. M. A. J. I. G. I. MUHAMMAD, M. U. H. A. M. M. A. D. A. B. D. U. L. H. A. M. I. D. SHAFI'I, O. L. A. L. E. R. E. MORUFU, B. A. S. H. I. R. A. B. D. U. L. L. A. H. I. MUHAMMAD, and O. N. W. A. O. C. H. A. VIVIAN, “Secure University Network Architecture, vulnerabilities, risk priority level classification and countermeasures,” i-manager’s Journal on Wireless Communication Networks, vol. 7, no. 2, p. 42, 2019. Available at: http://repository.futminna.edu.ng:8080/jspui/bitstream/123456789/10004/1/SECURE%20UNIVERSITY%20.pdf [Accessed on: 07.09.2022]
[26] M. U. Aksu, E. Altuncu, and K. Bicakci, “A first look at the usability of openvas Vulnerability Scanner,” Proceedings 2019 Workshop on Usable Security, 2019. Available at: https://www.researchgate.net/profile/Muharrem-Aksu/publication/331529924_A_First_Look_at_the_Usability_of_OpenVAS_Vulnerability_Scanner/links/5c7e7ac
8299bf1268d3a846a/A-First-Look-at-the-Usability-of-OpenVAS-Vulnerability-Scanner.pdf [Accessed on: 07.09.2022]cyber security assignment
[27] U. D. Ani, H. He, and A. Tiwari, “Vulnerability-based impact criticality estimation for Industrial Control Systems,” 2020 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), cyber security assignment2020. Available at: https://discovery.ucl.ac.uk/id/eprint/10108350/1/Uani_CameraReady-CyberScience2020_Submitted.pdf [Accessed on: 07.09.2022]












