ICT infrastructure assignment assessing the benefits of cloud based infrastructure for the commonwealth bank
Question
Task: how can the commonwealth bank use ICT infrastructure assignment research methodologies to identify the benefits of cloud based infrastructure
Answer
Introduction
The ICT infrastructure assignmentaims to analyze “commonwealth bank” information and communications technology (ICT) infrastructure and the required mitigation process. The goals and objectives are consistently related to the business plan, and ICT is already essential to a broad range of corporate operations. Here, the ICT infrastructure in the cloud of Commonwealth bank is to identify the ICT revolutionary ways of designing and implementing as well as controlling computer resources globally with minimum managerial commitment or communication with service providers. Therefore, the aspects of the company's local ICT infrastructure will be examined in this ICT infrastructure assignment. Following that, the justification for cloud migration will be reviewed using logical reasons as well as elements of ICT infrastructure in the clouds of commonwealth bank. On the other hand, a critical analysis of the cloud's ICT infrastructure and an explanation of potential concerns will be provided. However, the proposed mitigation for potential cloud concerns will be properly illustrated in this ICT infrastructure assignment.
Main Body
ICT Infrastructure in Local Data Center
In a local data center, there are two sorts of ICT infrastructure: elements required for the building's activities and technology to assist that fundamental IT architecture. In ICT infrastructure, a local data center incorporates the banks for all the hardware elements in a data center environment. It is data center infrastructure when it exists located within or provides the structural framework of a data center facility in the banks for the user's safety. The actual structure might not have glass, but it could have an entrance that allows sufficient air to keep IT and computing devices from becoming too excessive. The digital local data center has progressed from such anICT building with an on-site infrastructure into one that combines on-premises commonwealth bank systems with cloud architecture in which connections, software, and workflows are virtualized across many public and private clouds (Basmadjian, 2019). The ICT infrastructure assignment findings show Local data centers are available to analyze the companies to establish their infrastructure. Cloud computing centers are primarily built and utilized for personal purposes by just a single corporation. These are frequent among technology powerhouses. In a flexible workspace, data centers operate as a type of rental property, making the resources and space of a network infrastructure available to anyone who chooses to rent them.
Furthermore, the bank always provides safety for the users to protect their data via service management because the data is more important to the bank as well as the users. Service management is a third-party provider, data centers provide services for data processing, and computing, as well as other services to the bank consumers (Sarangi & Pradhan, 2020).However, Cloud data centers are spread and occasionally made available to consumers through the assistance of third-party maintained service providers. In below, diagrams show a local data center in ICT infrastructure for commonwealth bank as follows:
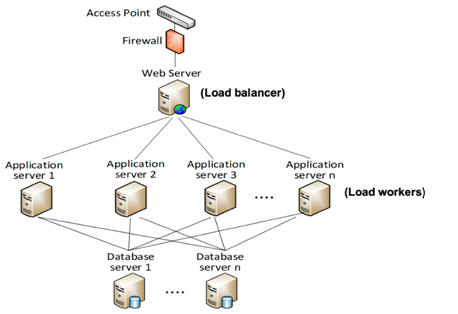
Figure 1: Local data center of commonwealth bank
(Source: Author)
The above figure on this ICT infrastructure assignmentidentifies the ICT infrastructure in the Commonwealth Bank's local data center, containing components such as servers, load balancers, firewalls, and data storage. In Commonwealth Bank, the web server connects to the access point to supply the server of each banking unit's applications server. There are several forms and formats of data output, input, and related technical specifications inside the banking operation units. As a result, specifications and specifications are generated for each activity unit, and web applications are designed to meet the operation component's distinct professional requirements (Arora &Bala, 2020). The virtual assistant is responsible for developing an operational device in the distribution network, assessing the product's life cycle, including sending the created information center to the ICT infrastructure; after that, consumers can access the information center from the banking ICT infrastructure through the gateways.
Justifications for Cloud Migration
The important constraints are indeed a lack of serious application, an insufficient device in the organization, slow internet, a lack of concentration to be using ICT on the part of both banking staff and managers, an absence of appropriate professional training, a lack of an updated ICT hardware, a lack of skilled support team, and poor technical assistance. The limitation of resources and capacity to operate computing power was a serious barrier for the Commonwealth Bank or banking sector in computing for such computer's computational power. ICT administrators are always searching for more efficient as well as faster technologies that will help in the quicker transmission of today's massive quantity of information. Routers protect customers' banking emails, programmed, and internet access, which can generate significant network congestion in TCP/IP systems (Joshi & Shah, 2019). The ICT infrastructure assignmentfindings show this might result in significant data loss and significantly reduced network performance, creating web collaboration unworkable. Such losses may happen when both routers and switches lack the necessary high-speed bandwidth.
The massive amounts of information currently available create challenges for ICT administrators. Because stopping sending more workers to these techniques, high-performance cloud technology for these massive amounts of data would demand computing and robotics.
The key obstacle for ICT administrators is to speed up or simplify essential banking procedures.
In most situations, cloud technology has assumed over with modern society. Although it provides a cost-effective as well as a flexible database, storage option for ICT.Which contains the data storage architecture required to enable a broad range of applications, according to admins. (Androniceanu et al., 2021).
The ICT prepared to assist with something a little more adjustable in cloud storage options than capacity and affordability.
There are IT administrators now have limited options for extracting valuable information from enormous data volumes. It is vital to identify data trends, analyze them effectively, and use them to create business decisions on communications infrastructure. A reliable network is required for any business to run successfully. Without the requirement for reliable internet connectivity, ICT cloud computing could be difficult for any business's IT executive. Modern software-based approaches and internet architectural style are required for data reliability.
On the other hand, the solution of the “commonwealth bank” business and information technology managers all across the world was upgrading the aging on-premises ICT system with cloud-based computing capacity that is adaptable, accessible, and cost-effective (Sen &Madria, 2020). There are various compelling advantages for the bank to embark on such a cloud migration route identified on this ICT infrastructure assignment and they range from reduced IT costs to increased creativity. Furthermore, the lack of a well-developed plan and cloud understanding makes organizational change challenging. The usage of new general-purpose graphics computer processors and multi-core computers could be a simple solution to this challenge. Because better financial systems are being employed, outdated software must be optimized and modified to produce the best results. Many efforts have begun to develop faster computers with lower costs and energy needs. As a result, IT directors must seek high-performance network speed with huge datasets, as well as a reliable bridge to collaborate with globally disparate scientific groups.Companies will also be needed to employ more complicated techniques for data collection, filtering, and storage via high-speed connections. In the coming, information security will be a top focus.
Businesses may improve their ICT infrastructure while also protecting their programs from dangerous hacker operations by moving to the cloud.
One critical issue to remember is that many leaders mistakenly believe that cloud-based infrastructure is what safeguards businesses.
This issue can be solved by utilizing distributed applications. Big tasks are divided into smaller, independent chunks that can be executed by several networked computers together via a network.
Cloud technology is a virtual machine of assets in the banking industry that permits operations across numerous application elements and assists in the execution of challenging tasks. To boost ICT infrastructure, cloud service choices must become more configurable. The ICT infrastructure assignment research shows cloud storage infrastructure should be simple to optimize depending on the software offered. It needs to be more trustworthy, cost-effective, and competent of managing a diverse range of workloads and user needs. Alternative options to cloud storage should be long-term and everlasting instead of a short-term remedy for such ICT environment (Atieh, 2021). The most basic solution to this problem is to design an ideal system with a standards-based framework that enables for effective data transmission among multiple tools as well as levels. This will help with faster information transfer and better data analysis. These findings will be used in banking building automation as well as information and network security monitoring. The ability to change the IP address may aid in the transfer of technology solutions to new devices. The solution to this problem involved expanding understanding of both conventional and wireless network connections. This will help networks optimize traffic allocation in order to cut costs and implement appropriate steps.
ICT Infrastructure in the Cloud
The ICT infrastructure in cloud computingis the on-demand deployment of computation, storage, apps, as well as other IT infrastructure alongside usage-based charging. Cloud technology is a popular Internet-based processing tool in which a large number of devices are linked together via public or private connections to provide constant infrastructure services for software, communications, and data backup.Here, the Core operations should be the final choice to migrate to the cloud, whereas Customer relationship management and Data-driven insights will most likely be the initial ones. It is apparent that banks were investigating cloud computing and may perhaps be running a few of their operations on it. Cloud infrastructure appears to be the most intriguing option, particularly in its initial stages of implementation. Hybrid or communal clouds can supplement private cloud resources as per the ICT infrastructure assignment findings. Cloud computing, a novel information and communications technology (ICT) architecture, is finally entering a full-scale implementation phase in the finance industry like a business development structure as well as in different fields including the production sector, healthcare, and banking to enhance efficiency.Figure 2depicts an ICT infrastructure model for cloud technology such as cloud storage, server, mobile phones, switches, application servers, and computers are given below:

Figure 2: Cloud infrastructure network
(Source: Author)
The above figure has providedcloud ICT infrastructure services, such as servers, storage areas, wireless routers, virtual machines, and data storage. Amazon's online computing is the greatest example of identifying the entire organization's network system. Cloud computing is a web-based service that enables clients to rent, instead of acquiring, servers and machines to execute their services.In the cloud infrastructure user sources the situation to the cloud provider, who gives information to the management, protection, and software cloud solutions (Umamaheswari, 2020). The Cloud-based ERP approach requires the user to make the infrastructure accessible both publicly and privately. It communicates with both the Virtual infrastructure periodically and uses the application capability the Cloud service gives. The banking sales invoices, fulfillment, and shipping are all managed in a sustainable mannerand responsibly. The cloud is utilized to distribute the services to a large number of client-servermodels. There are a few advantages of cloud infrastructure identified on this ICT infrastructure assignment as listed below:
Cloud storage:Cloud storage seems to be a cloud services concept in which data is stored on the cloud by a cloud computing solution that maintains and administers data cloud-based services (Tahir et al., 2020). It is offered on request with just-in-time capabilities and rates, and it removes the need for users to acquire and manage their existing data storage architecture.
Application server:The application server's task is to operate as a hosting for the customer's core functionality while also simplifying accessibility to and execution of the company applications.
Firewalls:Firewalls protect the PC system or infrastructure from external hackers by screening out harmful or unnecessary network packets. Firewalls can enable and reduce unwanted preventing ransomware from accessing a device or the internet through the web (Alicea&Alsmadi, 2021).
Server:A server's purpose is to exchange information, provide services, and assign tasks. A network server can also provide its unique computer programs; based on the situation, this may be a component of a trade or merely a technological capability.
Switches:Switches are essential components of any network. Connectors link several devices on a single network, including PCs, wireless access points, printers, as well as data centers, inside an organization or campus (Bezin&Pålsson, 2021). A switch enables paired devices to exchange and share information.
Issues in the Cloud
The cloud infrastructure (Cloud Service Provider) issue provides enterprises with IT equipment and resources. There are several difficulties confronting enterprises of all sizes, as utilizing the cloud eliminates the requirement to engage in in-house computational resources. Cloud services minimize management by offering a diverse and flexible solution that is adaptable in response to evolving demand. The primary reasons why many businesses prefer cloud computing identified on this ICT infrastructure assignment is they are modern innovations; but cloud services have some downsides, restrictions, and concerns. It is challenging to retain so much data without overburdening standard computer systems. When large amounts of digital information are stored, it is challenging to keep them safe. The resources necessary to effectively handle and preserve digital information continuously might be costly.Four issues must be explained as follows:
Data Breaches: The obligation of Cloud Service Providers (CSP) and users, maintained the leading cloud safety concern in CSA's survey (Liu, 2022). An unauthorized access can bring a company to its knees, causing long-term image damage, financial issues because of legislative repercussions, legal duties, incident administration costs, and decreased market attractiveness.
Misconfigurations and ineffective change management: As assets are wrongly configured, they become vulnerable to attacks. The hacking was tracked back to a misconfigured web app gateway that exposes Amazon S3 storage. Insufficient authorization and the usage of default settings are two more key causes of problems with unsecured storage (Zhang et al., 2022). In addition, insufficient managing change can result in cloud configuration errors. Misconfigurations, access monitoring, and user accountability are fresh additions to the cloud threat intelligence matrix.
Cloud-based security infrastructure and strategy are lacking:There are several firms that jump into the cloud without first putting into operation the appropriate technology and planning. This threat is specific to the subcategory and is the participant's responsibility. If adequate preparedness were not completed, users would be vulnerable to cyber-attacks, which can result in financial losses, brand damage, compliance issues, as well as legal complications.
Account takeover: The revelation, inadvertent breach, disclosure, or even other breaches of a cloud server that is vital to the management, operation, and preservation of a cloud system is referred to as cloud phishing scams (Volynkin, 2018). If compromised, these extremely privileged or confidential accounts can have far-reaching effects. Account penetration can result in data leaks as well as service outages due to phishing as well as identity stuffing, as well as insecure or stolen passwords, and inappropriate coding.
ICT infrastructure assignment -Cloud migrationsissues
The solution to the issues in the cloud is to understand the input value and the organizational implications of security breaches, if analyzing the encrypting data or implementing a solid, well-tested emergency response plan are both important. Information output and input consistency routines are performed by applying access privileges to access management and rules and processes for secure information removal and destruction.
Safeguard the data, regardless of its location in the system: The majority of the stolen information from the 5 million breached records during 2019 was useless since it was protected by encryption software. Virtual Strongbox’s proprietary end-to-end encryption safeguards banks' as well as their users' information under all circumstances (Wu et al., 2021).
Limit downloads or external bandwidth utilization: Since data are transferred to flash drives, the unsecured application is installed, or data is shared via Wireless links, the data is susceptible. When sending critical data by email, "snail mail," faxing, or even other insecure routes, use a Secured data platform. Whereas the information remains protected on infrastructure, the ICT infrastructure assignment research shows Virtual Strongbox enables users and their users with seamless, instant access to key information and documents.
Safeguard every PC and smartphone device: Check that the bank pcs, laptops, iPad, smartphones, and business servers are all properly secured (Tjostheim& Waterworth, 2020). Use powerful anti-malware software, web firewalls, and cybersecurity suites, and keep a record of who gets access to the devices while frequently installing and evaluating security safeguards.
Implement a "strong passwords" strategy and disable auto logins: Require different characters and compel password revisions regularly. Limit the use of obsolete passwords or identical ones for several programmers. Allow workers to instantly log into webpages and email servers only if the sites or machines are protected and authorized.
Conclusions
A brief overview of this ICT infrastructure assignmentis to examine "commonwealth bank" information and communications technology (ICT) infrastructure and the mitigation process. The goals and objectives have been found to link the company plan, and ICT is already crucial to many corporate activities. Here, Commonwealth Bank's ICT infrastructure in the cloud is to identify ICT revolutionary ways of building, executing, and controlling computer resources globally with minimal administrative commitment or communication with service providers. As a result, this research has looked at the aspects of the company's local ICT infrastructure. After that, the rationale for cloud migrations has been examined for utilizing the logical reasoning as well as parts of ICT infrastructure in Commonwealth Bank's clouds. On the other hand, a critical examination of the cloud's ICT infrastructure has been presented, as well as an explanation of potential concerns. Moreover, the proposed mitigation for potential cloud problems has been properly illustrated in this ICT infrastructure assignment.
References
Al Mudawi, N., Beloff, N., & White, M. (2020). Issues and challenges: cloud computing e-government in developing countries. International Journal of Advanced Computer Science and Applications,ICT infrastructure assignment 11(4), 7-11.
Alicea, M., &Alsmadi, I. (2021). Misconfiguration in Firewalls and Network Access Controls: Literature Review. Future Internet, 13(11), 283.
Androniceanu, A., Nica, E., Georgescu, I., &Sabie, O. M. (2021). The influence of the ICT on the control of corruption in public administrations of the EU member states: a comparative analysis based on panel data. Administratiesi Management Public, (37), 41-59.
Arora, S., &Bala, A. (2020). A survey: ICT enabled energy efficiency techniques for big data applications. Cluster Computing, ICT infrastructure assignment23(2), 775-796.
Atieh, A. T. (2021). Assuring the Optimum Security Level for Network, Physical and Cloud Infrastructure. ScienceOpen Preprints.
Basmadjian, R. (2019). Flexibility-based energy and demand management in data centers: a case study for cloud computing. Energies, 12(17), 3301.
Bezin, Y., &Pålsson, B. A. (2021). Multibody simulation benchmark for dynamic vehicle-track interaction in switches and crossings: modelling description and simulation tasks. Vehicle System Dynamics, ICT infrastructure assignment1-16.
Joshi, N., & Shah, S. (2019). A comprehensive survey of services provided by prevalent cloud computing environments. Smart intelligent computing and applications, 413-424.
Khoso, F. H., Arain, A. A., Lakhan, A., Kehar, A., &Nizamani, S. Z. (2021). Proposing a novel iot framework by identifying security and privacy issues in fog cloud services network. Int. ICT infrastructure assignmentJ, 9, 592-596.
Liu, X. M. (2022). A Risk-based Approach to Cybersecurity: A Case Study of Financial Messaging Networks Data Breaches. The Coastal Business Journal, 18(1), 2.
Sarangi, A. K., & Pradhan, R. P. (2020). ICT infrastructure and economic growth: A critical assessment and some policy implications. Decision, 47(4), 363-383.
Sen, A., &Madria, S. (2020). Analysis of a cloud migration framework for offline risk assessment of cloud service providers. Software: Practice and Experience, 50(6), 998-1021.
Tahir, A., Chen, F., Khan, H. U., Ming, Z., Ahmad, A., Nazir, S., & Shafiq, M. (2020). A systematic review on cloud storage mechanisms concerning e-healthcare systems. Sensors,ICT infrastructure assignment 20(18), 5392.
Tjostheim, I., & Waterworth, J. A. (2020, July). Inverting the panopticon to safeguard privacy in ambient environments: an exploratory study. In International Conference on Human-Computer Interaction (pp. 348-361). Springer, Cham.
Umamaheswari, S. (2020). Performance analysis of wireless sensor networks assisted by on-demand-based cloud infrastructure.
Volynkin, A. (2018). ACH Account Takeover Fraud. CARNEGIE-MELLON UNIV PITTSBURGH PA PITTSBURGH United States.
Wu, Z., Li, G., Shen, S., Lian, X., Chen, E., & Xu, G. (2021). Constructing dummy query sequences to protect location privacy and query privacy in location-based services. World Wide Web,ICT infrastructure assignment 24(1), 25-49.
Zhang, Q., Zhu, X., Zhang, M., & Mao, Z. M. (2022). Automated Runtime Mitigation for Misconfiguration Vulnerabilities in Industrial Control Systems.ICT infrastructure assignment












