Network Security Assignment: Top 5 Techniques To Control Security Issues
Question
Task:
Network Security Assignment Brief:
There are several approaches that we use to ensure security of a network. Conventional networks tend to use approaches such as honeypot, sandboxing and anomaly detection. These approaches work well as most environments have sufficient computational capabilities. Things change drastically in case of IoT devices. IoT devices are resource constrained which leads to an issue when applying all these approaches on the device itself. To address this, we tend to use a network structure with a mix of edge computing and cloud computing. In this assignment, you will explain in detail all four approaches, honeypot, sandboxing, anomaly detection, fog computing and cloud computing. You are expected to provide comparison where appropriate with pros and cons mentioned. You will use this knowledge to explain how these approaches can be used in an IoT based implementation. Provide a network diagram to show where each component will be placed and how they will be connected
Answer
Introduction
The current network security assignment is focused on discussing the various security measures as security has become a primary concern in the current times. This is because of the different forms of security risks and issues that can arise on the network channels and systems. Internet of Things (IoT) is the latest technology that provides an inter-connection of the networking and computing equipment and components. IoT devices are also associated with a wide range of security risks and issues.
The report covers five techniques that can be used to control and manage the security issues. These include honeypot, sandboxing, anomaly detection, fog computing, and cloud computing. The report includes the explanation of these techniques along with the pros and cons and comparison between the five techniques.
Background
Honeypot can be described as a security technique that develops a virtual trap to attract the malicious entities. It is the deception technique that assists in determining the attacker behaviour patterns. These can be used by the cybersecurity team to collect information on the operation mechanism followed by the attacker (Bitjoka & Elang 2018).
Sandboxing can be defined as cybersecurity technique that includes running and observing the code in a safe environment that mimics the operating environments of the end-users. Code analysis is also enabled under sandboxing technique. It is developed to prevent the occurrence of the security attacks and to make sure that the untrusted codes are properly analysed.
Anomaly detection is the technique that involves continuous analysis and monitoring of the network channels to determine the unusual behaviours and patterns. The security threats and risks and determined based on the packet signatures (Evangelou & Adams 2020).
Fog computing, also known as fog networking is the technique that uses edge devices to carry out all the computation tasks and processes. The technique involves decentralized computing infrastructure.
Cloud computing is the technique that includes the on-demand resources and networking abilities without directly involving the end-users in the resource allocation and management processes.
Comparison with Pros and Cons
All the five techniques that are described above can have a role in the network and IoT security. The pros and cons of the five techniques and the comparison between these techniques is illustrated below.
Honeypots can assure low false positives and ensure high success in the detection of the malware and other security attacks that may be possible. These can also be utilized to confuse the attackers and slow down the time frame that the attackers may take to access the network. With the aid of a virtual system, an organization can develop a number of decoys that can be useful in distracting the attackers and enhance the time they may take to find out the valuable data. Honey tokens can also be used that refer to fake data seeded within the database records that shall not be accessed in the usual circumstances. When an attacker may attempt accessing the honey tokens, alerts can be generated. Production honeypots can be very useful and these may come in the form of a web server, database, or it can only be a document (Veena & Meena 2018). These honeypots are low-interaction systems and it is easier for the security team to install these systems. The alerts can be generated when the attackers attempt to access the honeypots. These can also be useful in the training of the security team. The specific measures and techniques that the attackers may adopt can be clarified in the training sessions.
There are also a few drawbacks associated with the honeypots.
- If the attackers succeed in accessing the honeypots, they may use the same as a launchpad to carry out other forms of security attacks. The attacks could be conducted internally or on the other systems. Honeypots introduce risks and it may be difficult to control these risks thereafter.
- The honeypot system shall look legitimate to the attackers. There is additional cost that can get associated with the process. It may include hardware costs, cost of maintenance, etc.
- There can be an added complexity to the network with the addition of honeypots. The increased complexity of the network channel can make it further complex to secure with honeypots..
- The detection mechanism can be successful only when the honeypot is directly attacked.
Sandboxing technique also comes with its own share of pros and cons. It provides enhanced security and protection of the hardware along with the operating system and the database. With this technique, unauthorized data access to the host system can be completely avoided. The technique can also be useful in security the online browsers and systems from the malware attacks. However, the lack of updates can lead to the security gaps and vulnerabilities. These may be misused by the attackers to carry out the security attacks. The resource requirements and the cost associated with the technique can be high with the involvement of the complex sandboxes. These may also lead to the development of a false sense of security making it difficult to safeguard the system (Cafasso & Tarral 2018).
There is a wide range of anomaly detection techniques and the technique have the pros and cons attached with them. The technique can be used to develop and analyse the models with non-standard data types. However, the storage requirements associated with the technique can be significant. It is easier to implement these techniques in a wide range of applications. Also, it is not necessary to reprogram the applications associated with them. Also, the technique has high tolerance to include the uncertain information. However, it requires to be emulated and the processing time attached with the technique is also usually high.
The benefits, features, and drawbacks associated with each of the three is further explained and compared in the table below.
|
Parameter |
Honeypots |
Sandboxing |
Anomaly Detection |
|
Meaning |
Honeypot can be described as a security technique that develops a virtual trap to attract the malicious entities. It is the deception technique that assists in determining the attacker behaviour patterns. These can be used by the cybersecurity team to collect information on the operation mechanism followed by the attacker.
|
Sandboxing can be defined as cybersecurity technique that includes running and observing the code in a safe environment that mimics the operating environments of the end-users. Code analysis is also enabled under sandboxing technique. It is developed to prevent the occurrence of the security attacks and to make sure that the untrusted codes are properly analysed.
|
Anomaly detection is the technique that involves continuous analysis and monitoring of the network channels to determine the unusual behaviours and patterns. The security threats and risks and determined based on the packet signatures.
|
|
Types |
High/low/medium honeypots, research honeypots, and production honeypots |
Developer, developer pro, partial copy, and full |
Clustering-based, density, based, support vector machine-based |
|
Primary benefit |
Low false positive with high success rate |
Security of hardware, software, and database |
Easy implementation |
|
Significant issues |
Inability to detect the attacks if not directly attacked |
Resource requirements, costs, false positives |
High processing time and storage requirements |
Fog computing is a popular computing technique that can also have a role in network and IoT security. There are a number of pros and cons associated with fog computing.
Some of the benefits associated with fog computing are:
- The computing technique offers better security. It is possible to protect the fog nodes with the same procedures as implemented in the IoT environment
- The data selected can be locally processed rather than share the same to the cloud. It is beneficial from the security point of view and also include lower network bandwidth and operational costs
- Quick decisions are possible due to reduced latency
- Local data analysis rather than sharing the data over the cloud platforms resulting in the better privacy and security of the data
There are also a few drawbacks associated with the computing technique.
- Encryption algorithms and techniques can be complex for the arbitrary devices to share the data. The issues in the security algorithms can result in the data exposure. There may also be other security concerns, such as network eavesdropping, IP address spoofing, etc. that may occur as an outcome.
- Achieving and maintaining high levels of consistency can be challenging
- Trust and authentication are identified as the significant concerns in the computing technique (Khan, Parkinson & Qin 2017)
Cloud computing is a technique that is being widely used. From the security aspect, there are numerous pros and cons associated with cloud computing.
Some of the benefits associated with cloud computing security are:
- Automated backups can be assured with the involvement of cloud eliminating the possibilities of data loss
- Hardware failures usually do not occur and even if the problem occurs, the fatal problems to the physical servers do not take place
- Virtual environment of the client is protected as per the cloud model implemented
- Cloud provider has the responsibility to make sure that the cloud security is in place
There are also numerous risks associated with the cloud computing technique in terms of the security.
- Other users present over the cloud channels may carry out the security and privacy attacks (Kumar 2016)
- Denial of service is one of the major concerns which may have direct impacts on the availability of the data and system
The computing techniques as fog computing and cloud computing are compared and the results are as shown below.
|
Parameter |
Cloud Computing |
Fog Computing |
|
Latency involved in the computing technique |
The level of latency involved is high |
Level of latency involved is low |
|
Hops between user and server |
Multiple hops are involved |
Single hop is involved |
|
Computing architecture |
Centralized |
Distributed |
|
End-to-end security |
It is not possible to define |
Can be defined |
|
Possibility of attacks to the data sets enroute |
High |
Low |
|
Location awareness |
No |
Yes |
|
Power consumption involved with the technique |
High |
Low |
|
Nature of failure |
Predictable |
Extremely diverse |
Integration in an IoT Environment
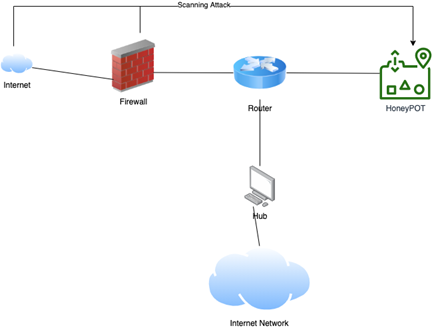
There are different ways and applications of the five techniques covered above with respect to the IoT technology and systems. A number of low-cost development boards can be used in the development of the IoT product. These devices can assure enhanced control and customers along with the support to the virtualization techniques. The development of the honeypot in an IoT environment can be tailored as per the type of the device. For instance, sensor node is associated with limited functionality and it can be mapped with the low interaction honeypot. Router, on the other hand can host the high-interaction honeypot. It can cover a wider number of attacks and detections (Gadde et al. 2018).
Intelligent interaction honeypots can be used with the IoT system to promote the IoT security. The primary goal of the interaction is to determine the adequate behaviour for client interaction from zero-knowledge regarding the IoT devices. The adequate response to the client shall be successful in extending the session with potential attackers. It can also be useful to trick them to past the check and share the exploit requests. With the effective interaction with the attackers, it is possible to achieve the required level of learning that can be useful in the optimization of correct behaviour associated with each request.
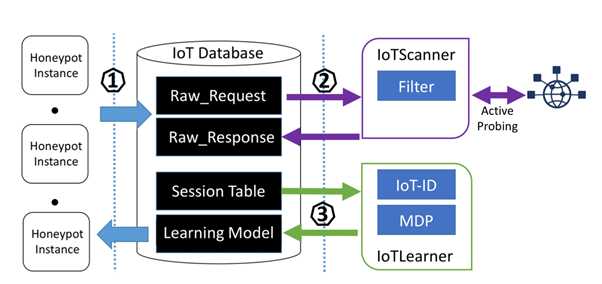
IoT Integration with Honeypots
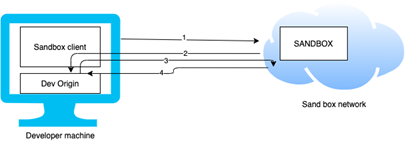
Sandboxing can be an important mechanism associated with the development of the IoT applications. It can provide the ability to separate and protect the application procedures so that effective management and control is possible. Bare bones environments coupled with the sandbox design can be significant from the security aspect of the IoT devices. A majority of the microcontrollers by design are bare bones. Arduino platform, for example, is also bare bones. There have been attempts made to remove Linux from the Raspberry Pi. However, it requires significant amount of effort. There are also attempts being made to include multitasking abilities on the microcontrollers (Borate 2016). The real-time operating systems, RTOS are being deployed for this purpose. However, most of the RTOS environment have their own share of caveats and these need particular resources. Virtualization and scripting are some of the techniques that may be used to provide sandbox environment for the security of the IoT devices. With these techniques, it would be possible to deploy the applications in the form of the scripts. They may also involve cross-platform bytecode.
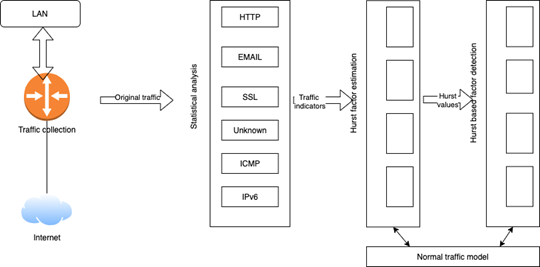
The different techniques and types of anomaly detection can be used to secure and protect the IoT devices and system. One such system has been illustrated below that comprises of a number of components. It includes the security gateway along with the IoT security service. The purpose of the security gateway is to keep a track of the devices and carry out the anomaly detection in the process. It shall be conducted to determine the compromised devices present in the network channel. It is supported by the IoT security which that may be associated with the providers, such as Microsoft, Amazon, or others (Dymora & Mazurek 2019).
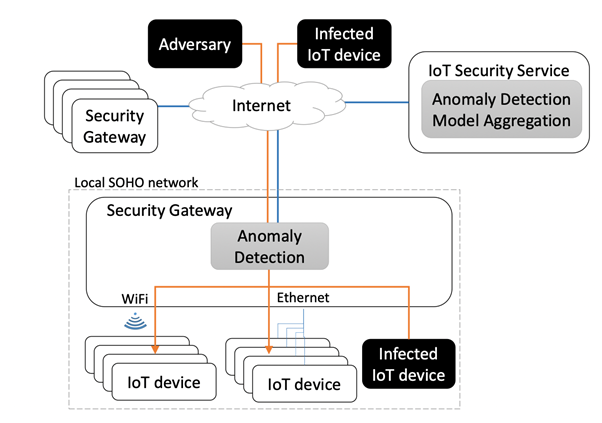
Anomaly-based IoT Environment
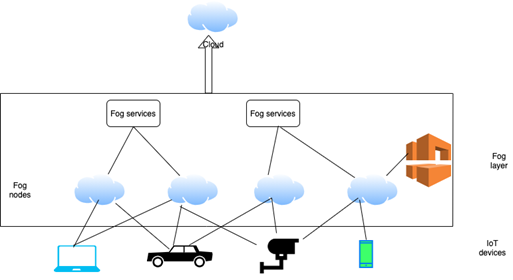
Fog computing comes with a set of unique characteristics that include distributed nature along with remote operations. These can be useful in the promotion of the security of the IoT devices. It can promote the security of the IoT layer as a whole because of the reason that it enabled local security and privacy services. These may include local monitoring and detection of the threats. Fog computing is the technique that supports the local data storage. It also involves the analysis of the time-sensitive information. It brings down the amount of the data along with the distance involved in the transmission to the cloud. As a result, the attack surface is reduced bringing down the probability of the security risks and issues that may occur. Fog nodes can be used as the proxies for the IoT devices. These can be involved in the management of the authorization process and eliminate the security concerns (Ghildiyal, Semwal & Kumar 2019).
Cloud computing can also have a role in the promotion and management of the IoT security services and applications. The flow of data sets from the IoT endpoints to the cloud platforms are required to be secured. It is essential to implement the monitoring and filtering applications at the edge so that the monitoring of the systems and data sets is possible. It can assist in the detection of the suspicious activity and it can also be useful in determining the anomalies (Rajani & Reddy 2016).
IoT and network security can involve a number of issues and it is important to come up with the latest measures to protect the IoT devices, networks, and systems from the security risks and issues.
Conclusion
Network security and IoT security can be major concerns for the service providers and organizations. It is necessary that the measures are implemented to promote and safeguard the security. The use of the techniques as honeypots, sandboxes, and anomaly detection can assist in the detection of the security issues. Fog computing and cloud computing come with their respective traits. Fog computing characteristics can be more useful to promote the security of the IoT devices and systems.
References
Bitjoka, G & Elang, A 2018, ‘Network Malware Laboratory BasedOn Honeypots Technologies’, Journal of Cybersecurity Research (JCR), vol. 3, no. 1, pp. 1–12.
Borate, I 2016, ‘Sandboxing in Linux: From Smartphone to Cloud’, International Journal of Computer Applications, vol. 148, no. 8, pp. 1–8.
Cafasso, M & Tarral, M 2018, ‘Designing flexible sandboxing solutions to adapt to new malware trends’, Computer Fraud & Security, vol. 2018, no. 2, pp. 5–9.
Dymora, P & Mazurek, M 2019, ‘Anomaly Detection in IoT Communication Network Based on Spectral Analysis and Hurst Exponent’, Applied Sciences, vol. 9, no. 24, p. 5319.
Evangelou, M & Adams, NM 2020, ‘An anomaly detection framework for cyber-security data’, Computers & Security, p. 101941.
Gadde, SS, Krishna Srinivas Ganta, R, Gopala Gupta, A, Rao K, R & Mohan Rao, K 2018, ‘Securing Internet of Things(IoT) Using HoneyPots’, International Journal of Engineering & Technology, vol. 7, no. 2.7, p. 820.
Ghildiyal, S, Semwal, A & Kumar, S 2019, ‘Enhancing Security of Internet of Things (IoT) using Fog Computing’, SSRN Electronic Journal.
Khan, S, Parkinson, S & Qin, Y 2017, ‘Fog computing security: a review of current applications and security solutions’, Journal of Cloud Computing, vol. 6, no. 1.
Kumar, R 2016, ‘Cloud computing and security issue’, International Journal Of Engineering And Computer Science.
Rajani, P & Reddy, PA 2016, ‘Security Ecosystem in IoT & Cloud’, International Journal Of Engineering And Computer Science.
Veena, K & Meena, K 2018, ‘An Intrusion Detection System for Network Security Based on an Advanced Honeypots Server’, International journal of simulation: systems, science & technology.












