Penetration Testing Assignment: Pen-Test Portfolio
Question
Task:
This is an individual assessment comprised of two tasks. Task 1 and task 2 carry 50% respectively of the overall portfolio mark. Task 1 will assess your understanding of the statutory and ethical issues surrounding penetration testing and also assess your understanding of the process itself. Task 2 will assess your ability to conduct a full-scale penetration test. You are expected to demonstrate an insight into the implications of the problem introduced in each task by using clear and concise arguments. You will receive formative feedback as part of the module to demonstrate how to be concise in your written work. Please ensure, in completing these tasks you deploy the techniques you have been taught. If you produce work that is not concise and to the point, then marks may be reduced. The reports should be well written (and word-processed), showing good skills in creativity and design. Sentences should be of an appropriate length and the writing style should be brief but informative.
Task 1 – SOP for PenTesting
Task 1 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to undertake research and critically compare the published penetration testing methodologies. You are expected to comment on the statutory and ethical considerations of a penetration tester. You are expected to design/develop a Standard Operating Procedure (SOP), including a decision-making tree, to describe how you will undertake task 2. In particular: intelligence gathering (target profiling), vulnerability identification and analysis, and target exploitation (including post exploitation). An SOP is defined as a set of step-by-step instructions compiled by an organisation to help workers carry out routine operations.
Task 2 – Penetration Test
Task 2 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to conduct a penetration test against a target system that will be provided to you. You are required to present your findings in a factual manner to convince decision makers of a large corporation on business strategies.
Answer
Overview
The penetration testing assignment sheds light on the several aspects of pen testing which is a kind of protection testing, that is utilized to check the insecurity of an application. It is performed to discover the protection risk that can be there in the system. If a system is not protected, then any invader can disturb or gain access to the respective system. The security risk is generally an unintentional mistake that happens whilst creating as well as executing the software.
In this penetration testing assignment, a brief comparison of the various pen-testing methodologies is provided. Further, the legal as well as statutory issues as well as precautions that must be considered by both the client as well as the tester are given. Followed by the Standard Operation Procedure for the second task is given. It is supported by the Decision making tree that is made considering the second task.
Penetration testing methodologies
There are various methodologies for penetration testing. In order to critically analyze them it can be stated herein penetration testing assignment that:
ISSAF is an open portal, peer-reviewed, pen test framework developed by the OISSG or the Open Information Systems Security Group. ISSAF is defined as a structure as well as summarizes various methodologies in outline 0.2.1B (Tehrani and Vahid, 2018). It tries to cover all probable domains of a pen test from ideology to practicality. The authors propose that is simpler to delete data rather than create it from the ground up. On the other hand, OSSTMM is an open portal protecting testing means brought up in 2000 by ISECOM or the Institute for Security as well as Open Methodologies. OSSTMM was created under peer-review and profits from open portal licensing, but, an allowance to the recent version (v4), needs paid membership. It is described as a means that summarize models as well as channels as channels stand for various domain regions. The pen test methodology rooted inside the ISSAF structure is separated into three starting stages, namely, assessment, strategizing as well as preparing and clean up and reporting. One benefit of ISSAF discussed in the penetration testing assignment in specific is that the unique connection between the work as well as their related tools for each work is displayed.
OSSTMM is mainly auditing means, therefore, it is not as inclusive as ISSAF as well as does not give tools or means for finishing models but it is a worthy auditing resource, which might be utilized to content regulatory needs for the business possessions provided protecting auditors having enough skills to accomplish every stage. OWASP is a non-beneficial company concentrating on enhancing software protection. It gives a lot of tools, guides as well as testing means for cyber protection under open portal licenses, in specific, OTG or the OWASP Testing Guide. OTG is separated into three main segments, namely, the web application testing means, the OWASP testing framework for web app growth, as well as reporting. The web app means might be utilized autonomously, or in combination with the testing structure, a creator might utilize the structure to develop a web app with protection in mind leading to a pen test to check the design.
Building security in Maturity Model is a software protection structure registered under Creative Commons as well as created by McGraw, West, and Migues. In creating BSIMM, its founders examined the protection practices executed in 67 highly flourished organizations. BSIMM includes 112 processes separated into 12 practices, sustaining 4 domains primarily, intelligence, deployment, governance, as well as SSDL touch points. Penetration Security Execution Standard is a pen test standard that was mainly developed in 2009 by Nickerson (Khalid, 2018). PTES comprises intelligence gathering, vulnerability, post-exploitation, pre-engagement interactions, threat modeling, exploitation, and reporting. It takes benefits of other possessions with the move toward inventing the wheel, slightly, fits in other structures inside it. This process illustrated in this section of penetration testing assignment explains more about the penetration test in seven different points such as:
- Pre-engagement Interaction: This phase elaborates us about the penetration text. This phase mainly verifies the submitted documents and also checks the various tools needed for the text.
- Intelligence gathering: This stage is about collecting data from various external sources such as from various websites, social media, as well as several official records. This is an open source intelligence phase.
- Threat modelling: This process mainly consists of developing the security of a particular network by analyzing is key aspects and susceptibility, and explaining its various prevention steps, or decrease effects of system threat.
- Vulnerability Analysis: This phase analyses the various threats and approves susceptibility which could affect the system application.
- Exploitation: In this stage the analyst tries to gain the security of the main system objective using various susceptibility aspects.
- Post Exploitation: This phase mainly handles the main system as well as gathers the data required.
- Reporting: This process reflects the whole process of penetration such that users could know more about the objective of security.
- Metasploit – It is a set of pen tests as well as interference detection tools modeled to recognize and use weaknesses on a target system. Metasploit was mainly an open portal assignment created in 2003 however was obtained in 2009 by Rapid7 that is now accountable for its growth as well as sustenance. Metasploit Framework or MSF is accessible in four different editions. MSF is appropriate for the advanced protection expert who has a rigid understanding of the pen test and is satisfied using function line pen-testing tools.
Statutory and ethical consideration of a penetration tester
The following are some problems provided in the penetration testing assignment that may emerge between a client and the tester-
- The tester in unrecognized to his client – therefore, on what aspect, he shall be provided an allowance to sensitive information
- Who will ensure the protection of the lost information?
- The client might charge for the loss of confidentiality or information to tester
Pen testing might have an impact on the performance of the system, as well as might elevate integrity and confidentiality problems, thus, it is essential, even in an interior pen testing, and that is operated by an interior employee to get an allowance in writing (Jochelson and Gacek, 2017). There must be a written accord amongst a tester and the organization/company/client to elucidate every point about the information protection, disclosure, etc. before initiating the test.
A statement of intent must be illustrated up as well as accordingly signed by the tester as well as the client before any test that is to be conducted. It must be undoubtedly outlined in the penetration testing assignment that the aim of the task as well as that, we might or might not be whilst operating weakness tests.
As argued in the proposed penetration testing assignment, it is very essential for the tester to acknowledge who possesses the industry or systems that are being considered to be operated on, as well as the structure between testing co-ordinations as well as their aims, which might be possibly influenced by the penetration testing. The concept is to confirm:
- The tester has the allowance in writing, with all the clarifications described properly.
- The organization has the description of its penetration tester as well as a guarantee that he will not reveal any confidential information (Clark, 2018).
A legal agreement is profitable for the tester as well as the client. Always keep in mind, that guidelines as well as laws change from one country to another, so one must keep oneself updated with the rules as well as guidelines of the respective country. The investigation on penetration testing assignment signifies that an agreement must be signed after reviewing as well as considering all the respective laws.
SOP for penetration testing
SOP Number: <<fill data>>
SOP Title: <<fill data>>
|
NAME |
TITLE |
SIGNATURE |
DATA |
|
|
Author |
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
Reviewer |
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
Authorizer |
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
Effective Date: |
|
READ BY |
|||
|
NAME |
TITLE |
SIGNATURE |
DATE |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
|
<<fill data>> |
<<fill data>> |
<<fill data>> |
<<fill data>> |
- PURPOSE: The key objective of penetration testing highlighted in the present penetration testing assignment is to classify certain weaknesses of security system. This penetration testing process is also used to analyze company’s security policy, its faithfulness as well as concurrence compulsions, workers security alertness as well as the process how the company would classify and react to its security problems. SOP gives us a brief explanation about a certain machine or products, how these are to be managed and regulated. The main objective of penetration testing is to understand the security policy or weaknesses of the organization.
- INTRODUCTION: In the present world, where susceptibility and data breaches are responsible for companies destruction, thus for every organization it is very important to understand the use of cyber security. Cyber attackers are always one step ahead of the safety measures which the IT department is prepared as cyber security measures.
- SCOPE: The main scope of penetration testing discussed in this section of penetration testing assignment explains about the cardholder data environment (CDE) which mainly includes various processes, customers, as well as the machinery which stores the data, or broadcasts the authenticated data of the cardholder. Main scope of this testing process is to explain about the requirements of PCI DSS, also includes the whole of CDE confines as well as various measures which might disturb the security of cardholders. Similarly both external attacks also known as (public-facing attack surfaces) as well as also internal attacks of CDE known as (LAN-LAN attack surfaces)
- DEFINITION: In simple words it is stated herein penetration testing assignment that penetration testing is the process of verifying various weaknesses of an IT company. The following process gives us information about how experts examine the problems as well as threats for their company and solves the following issues related to cyber world. Various susceptible threats include: minute mistakes in designing and describing the code of the software. Not making proper use of the software. Various faults in backend of the coding ground which might further result in cyber threats for the company.
- RESPONSIBILITES: Certain responsibilities of penetration testing outlined in the penetration testing assignment mainly varies on the employee who carries out this specific task, thus below are few important key points while conducting this test:
- Performing various types of tests on the required web-based software’s and computer networks (Boulanger and Idriss, 2016). The person in charge uses several protocols and methods of ethical hacking which are some of major toots of this testing process.
- Physical security evaluation is a process in which the analyst performs various steps of device network security.
- Conducts security investigation to know how well the company is performing in its system security.
- Examines security policies in any improvement is required hence fourth.
- Prepares a final report of the security check.
- SPECIFIC PROCEDURE: There are several methods of Penetration testing which are mentioned below within the penetration testing assignment:
- External testing – This process mainly includes resources of the organization which is mainly published on internet such as various web applications, companies’ website, and email address (Learning Center, 2020). The main aim is to hack the site and gain valuable information.
- Internal testing – In this process the analyst tries to perform an attack into the software behind the firewall protection and inputs the data inside the software.
- Blind testing – In this type of test the expert is only provided with the name of the organization which is under target and thus he follows the reaming task for performing the test.
- Double-blind testing – According to this test analysis done in the penetration testing assignment, tester do not have any prior knowledge about the test to be performed.
- Targeted testing – In this process both the analyst and person in charge of the security both gives an equal contribution for the work to be fulfilled.
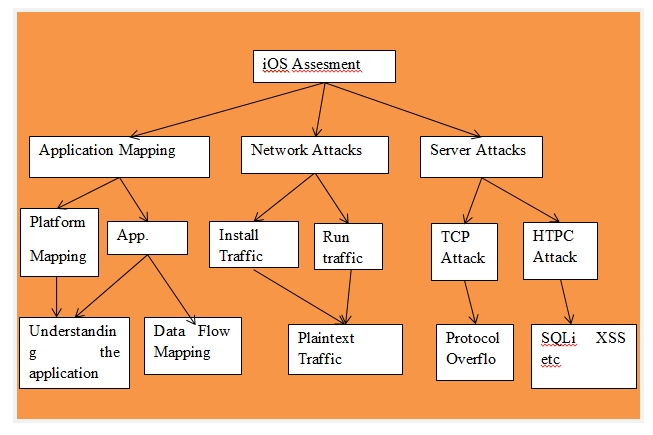
Decision making tree
References
Boulanger, R.W. and Idriss, I.M., 2016. CPT-based liquefaction triggering procedure. Journal of Geotechnical and Geoenvironmental Engineering, 142(2), p.04015065.
Clark, K., 2018. Specters of California's Homophobic Past: A Look at California's Sex Offender Registration Requirements for Perpetrators of Statutory Rape. UCDL Rev., 52, p.1747.
Jochelson, R. and Gacek, J., 2017. ‘Animal Justice’and Sexual (Ab) use: Consideration of Legal Recognition of Sentience for Animals in Canada. Penetration testing assignment Manitoba Law Journal, 40(3).
Khalid, M.N., 2018. A COMPARISON AND EFFECTIVE PENETRATION TESTING APPROACHES WITH NMPREDICTOR BASED ON MACHINE LEARNING (Doctoral dissertation, Bahria University Karachi Campus).
Learning Center. (2020). What is Penetration Testing | Step-By-Step Process & Methods | Imperva. [online]
Tehrani, F.S. and Vahid, G., 2018. Comparison of cavity expansion and material point method for simulation of cone penetration in sand. In Cone Penetration Testing 2018 (pp. 611-615). CRC Press.












