Risk Assessment Case Study: Security Of Inhouse HR Database in DAS
Question
Task: Prepare a report on risk assessment case study analysis on a risk assessment for in house HR database for DAS (Department of Administrative Services) in terms of security and privacy?
Answer
Introduction to the risk assessment case study
Cloud computing is among the widely using technology in the business organisations. The “Cloud First” policy of Australian government has made many organisations of private and public sector to adapt cloud technology for storing and handling their data. DAS (Department of Administrative Services) is among such organisation which offers its services to other department such as HR and personnel management and with implementation of this policy, it had to change its data management system from its data centres to SaaS services. The usage of cloud for handling data can prevent various threats that are involved in using data centre for storing data. This risk assessment case study analysis aims to discuss the existing intimidations and risks with the use of inhouse HR database in terms of security and privacy mainly. This work will also discuss the intimidations and risks involved in using SaaS service for managing data. the use of SaaS services has also made employees to use digital ID therefore, this work will also discuss the issues with the use of digital ID.
Security of employee data
Existing intimidations and menaces of using inhouse HR database
As per the given risk assessment case study, the HR database is used by HR professionals for storing personal information of the employees of a business entity. The use of this information is used for various activities like training details, awards, managing recruitment and others. An inhouse data centre requires use of server of the company within the office of company for storing data on location. It involves a specific space or building which is designed and reserved to accommodate servers and other network hardware. DAS uses its inhouse data centre for storing and managing data of employees from various government department such as personal information, identity proofs and others.
1. Flexibility: The flexibility policy of the companies provided to the employees can be a risk in the data security. This policy enables employees to bring their device like laptops to their workplace (Chung, 2017). The employees can access information and data from their device which can enable them to manipulate, alter or expose data. In the present scenario, when COVID-19 has obstructed the employees to work from office, the companies has allowed them to work from other places from their devise. The employees of DAS can manipulate or expose personal or other employee information or provide it to third party raising the risk to data security.
2. Authentic and unnecessary privilege abuse: While using inhouse database, some individuals from HR and other department have responsibility to managing data because of which they have access to the server and information of employees. These employees can manipulate or use such data for their benefit or also provide it to third party. The employees of DAS can use information or data about the government employees for their benefit or provide it to third party who can use it for identity theft or other illegal tasks. Such use of data from the authorised employees of a company is known as authorised privilege abuse. The employees from other department do not have authority to access server or data of other employees. The individual who access other employee data for misusing or manipulating it is termed as unnecessary privilege. DAS data centre store information of employees of other departments, these employees can access the employee data of same or other department which is a threat to the employee data security. This data can be used by them for their benefit like reducing competition, provide to third party for illegal use or others.
3. Negligence: In the inhouse infrastructure, negligence is also a risk to the employee data security. The negligence of employees or personnel who are responsible managing network system and devices can make the information vulnerable. Such negligence can cause system or server failure which makes the data vulnerable and making others to access it (Dominitz, 2016). Considering the readings of risk assessment case study, the data and information of government employees are very crucial because of their access to the government departments because of which many hackers need it for making money. The negligence towards server system can pose the threat of data theft. The negligence of network system or devices can also raise the threat of losing data which makes employees to restrict access to their workplace and system causing hinderance in their work. The lost of employee data restrict employee verification, their authorisation level and use of authentication card.
4. Malware: The data security concern from malware is not novice. The increasing dependency of financial, social and professional life of people on the digitalisation has made malware more harmful for the firm and individuals (Primiero, Solheim& Spring, 2019). The term malware is used for denoting all malicious software that are used for stealing or manipulating data. Malware is a major threat to the employee data stored in the inhouse database of DAS. The cyber attackers can use malware for harming data and system of data centre of gaining access about the data of government employees. The access to the data base canenables them to conduct data theft, identity theft or other misuse of employee data which can be harmful for both employee and department.
5. Database injection attack or SQL Injection:It is among most common intimidations to the database system. In this attack, the attacker augment SQL statement to an application through input box for gaining access of making change to information stored in the database (Alwan&Younis, 2017). Such attacks, make the information stored in database vulnerable and provide cyber attackers access to that information. SQL Injection attack in the database of DAS can pose the threat of data theft, identity theft and others to the employee data. The attackers can use information of government employees for gaining access to their department, stealing information, performingbribes and others.
Additional fears and perils to employee data after using SaaS application SaaS application is one of the evolving software applications which is based on the internet. This application is used by multiple users with different business services (Aleem, Batool, Ahmed &Khattak, 2018). The use of SaaS application by DAS can prevent the data from the existing risks to the data security. Although, the use of SaaS services raised new issues and threats to the data security of the government employee data. The new intimidations in the use of SaaS application considering the given risk assessment case study is as follows:
1. Data access: The use of SaaS application makes business entities to store their data outside from the boundary which is in the premises of SaaS vendor (Patel &Alabisi, 2019). The data access can be a threat to the data security of the employee data of DAS. The migration of data from datacentre to the cloud of SaaS vendor in California can make it more vulnerable tointrusion and hacking as they are using public cloud for altering and accessing the saved information.
2. Lack of transparency: There is lack of transparency between the service provider and DAS. Both firms do not want to share their methods because of their privacy policies. Such lack of transparency can be threat to the data security as DAS is unaware regarding the ways by which data of government employees is being saved, captured and transferred by the service provider.
3. Lack of visibility: The use of SaaS application makes the company to save its data to a cloud far from the premises of the firm. It raises the risk of lack of visibility as the client can not be able to know about the activities that a service provider is doing with the data (Yuen &Chuah, 2017). DAS has data about the government employees which is very critical in nature therefore lack of visibility can be a threat to the data security of employees.
4. Legal concerns and regulatory compliance: SaaS application provider of DAS is from US and has replica centre in Ireland and processing centre in India. It means the employee data from DAS firstly migrate to India and then US and Ireland. Every nation has their own data regulation policies and compliances regarding the data security. The gap in the legislation and regulation of these countries and Australia can cause legal concerns for DAS which can be a threat to its data security.
Assessment of severity of menace and hazard to employee data
The assessment of risk severity is important for an organisation to understand the consequence of their actions. In this section, the risk severity matrix is used for analysing the severity of risks involved in both use of inhouse data centre and SaaS application by DAS for storing employee data. The risks severity assessment basis the scenario of risk assessment case study for DAS is as follows:
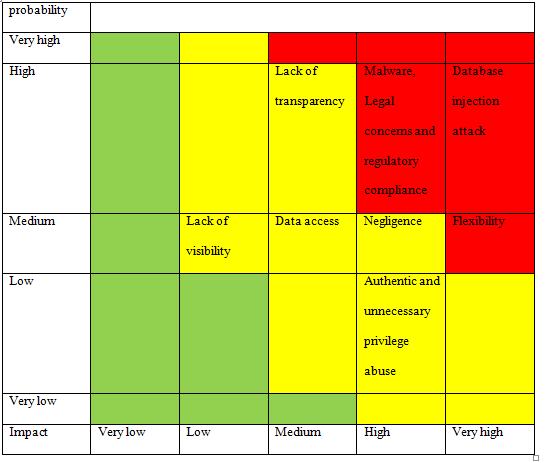
Privacy of Employee Data
Existing intimidations and menaces to data privacy in inhouse HR database
Data privacy is also known as information privacy which is related to the collection, storage and ownership of the data. in any organisation employee data involves their personal information, identity proofs, medical information, physical identity, behaviour at work and other crucial information. It is important for the firms to keep such data protected and safe for the benefit of both employee and firm therefore, privacy is an important factor in the collection and storage of their data. It has been discussed earlier in this risk assessment case study analysis that inhouse database has certain issues regarding the data security because of which there can be a risk of data privacy in the of employee data. The menaces of privacy to employee data are as follows:
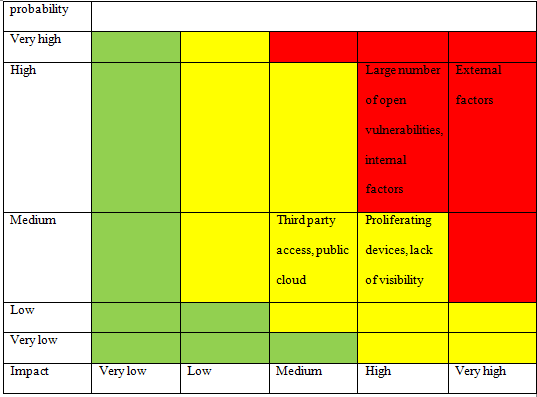
1. Proliferating devices: the maintenance of data privacy become more critical to handle due to the presence of factors like bring your own device, proliferating internet connected tables and internet of things (Shastri & Sharma, 2016). The increasing number of devices can made it difficult to manage larger data which make it vulnerable and enable others to have access to employee data. It can pose menace to the privacy of employee data. With the proliferating device, the privacy of employee data of DAS can be at risk of exposure.
2. Large number of open vulnerabilities: As per the 5 Biggest Challenges in Global Data Privacy and Protection – Cipher (2020), there are about 15000 disclosed vulnerabilities recognised in 2017 which are 56% more than in 2016. The rapid enhancement in vulnerabilities can cause huge amount of data breaches. It is very difficult for the IT security team to manage such huge number of patches every year. This makes it difficult to a firm to maintain privacy of their data. It is stated in this risk assessment case study analysis report that the patch management on such large scale is also difficult for DAS which makes large number of open vulnerabilities a risk to the privacy of employee data.
3. Internal factors: The risks to data privacy that are imposed by internal elements of an organisation are the internal factors. The inhouse HR database is handled by the internal workforce of a company like HR manager and others. These employees have access to the personal and professional information of other employees which can be exploited by them. Beside of this, other employees from any department of the firm can also access employee data through their system. It also imposes risk to the privacy of employee data. These employees in DAS can cause menace to the privacy of employee data. the one more internal factor that can cause risk to data privacy of employees is the system and software that are used for the security and safety of database which assures the privacy and veracity of data. The entities use encrypted code for ensuring the privacy and safety of employee data. The risk that can compromise the data privacy is the poor encryption. The use of poor encryption can cause data breaches in the HR database which provide cyber attackers an ease to access employee data causing threat to data privacy. The one more internal factor that can cause risk to the privacy of employee data is the feeble cyber security software. Sometimes, the cybersecurity software fails to deliver the benefits like safety from external threats (Jardine, 2020). Such feeble software can cause risks of data breach in the database of a firm causing menace to the privacy of data. It enables hackers or attackers to have unauthorised access of the DAS database which have personal and professional data of employees causing obstruction in data privacy.
4. External factors: the factors outside the premises of a firm that impose threat to the data privacy are the external factors. The first external factor that can cause menace to data privacy is hackers. The hackers can cause data breach for gaining access to data base so that they can steal employee data. such individuals can cause threat about the data privacy. The one more external factor is snooping which can obstruct data privacy of the government employees. Th employee data in DAS has information about the government employees which is crucial and whose exposure is valuable for third party. The other externa factors that can cause risks to data privacy are vulnerabilities, spyware, trojan, webshells and others (Paul &Aithal, 2019). All such factors can provide unauthorised access to the third-party causing risk to data privacy.
New intimidations and hazards to data privacy in SaaS application
SaaS application is a cloud service which enable various firms to gain advantage of subscribing the service as an alternative of investing to it (Kaikkonen,, 2019). The use of this application can save cost and time of the firms in forming and managing data base. Although it also has certain risks and threats to the data privacy which can be as follows:
1. Lack of visibility: the data stored in cloud is outside the premises of the DAS and where Das does not have control or visibility of data. the employee data of DAS has intellectual property, personal recognisable information and other information of government employees. The lack of visibility enables the service provider to use or manipulate data which is arisk to the data privacy of employees.
2. Third party access: Data privacy involves the access to the data to any third party because of the cruciality of information. SaaS application is a third-party public cloud infrastructure which enhances the risk of exposure of the private data (Sharif, et al., 2016). The migration of government employee data of DAS to SaaS application makes the SaaS service provider a third party who has access to this data. Beside of this, the process of data transfer involves processing unit and replica unit of the service provider who also have access to this data. the involvement of these parties can pose a menace to the data privacy of DAS.
3. Public cloud: As per the scenario of risk assessment case study, in the SaaS application, the data of DAS will be store and manage in a cloud which is shared by various other firms. The involvement of multiple parties in SaaS application can cause the risk of violation of privacy of the user data (Mehmood, et al., 2016). SaaS application function on the public internet and has concept of share access. It makes easy for others to access the information of a firm or user. The data stored by DAS have crucial information on employee which can be used for generating fake identity or manipulating employees. Such access is a risk to the data privacy of the employees.
Assessment of severity of menace to the privacy of employee data The risk severity matrix for data privacy risks for DAS is as follows:
What is the digital identity issues identified from the risk assessment case study?
The data which is stored and managed by SaaS application from the DAS database involves data of government employees which is required for HR and personnel management. It has been discussed before that SaaS application also have certain menaces and threats regrading security and privacy of data but the cloud policy of Australian government has firms to migrate their data to the SaaS application. The employees are required to have access to their data because of which they have provided with digital id so that they can access it. The digital id involves digital biometric of a person along with a digital watermark which is encoded with personally identifiable information (Poder&Eckel, 2019). The use of digital identity also has certain issues such as identity theft. It enables a third party to generate false identity of employee and use it to gain access of the system, cloud and offices in which an employee can have access which can cause problem to employee and department. The digital id is also used for authentication of employees and manipulation in its data can cause restriction in the function and movement of employee in own and different departments. The human error can also be an issue in using digital id as the employees are required to remember their id. The failure in doing so can make them impossible to access their information, system and department. They can also face problem regarding their internal authentication.
Conclusion
It is concluded from the above risk assessment case study analysis that SaaS application is among the most usable technology in the firms for storing and handling their data. Before this technology, every firm uses their inhouse database which has various risks and problems in terms of data security and data privacy. The SaaS application has made the process of data storage less time and cost consuming. Although, it has also raised certain menaces and threats to the privacy and security of data. This work has discussed the risks associated with the use of inhouse database and SaaS application related to the security and privacy of data of employees. The risk has also assessed by using risk severity matrix. The conclusion that can be drawn from this work is DAS can use SaaS service as it reduces their cost and time along with the pressure related to security and safety of data.
References
Aleem, S., Batool, R., Ahmed, F., &Khattak, A. M. (2018, November). Design guidelines for SaaS development process. In 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (
IEMCON) (pp. 825-831). IEEE. https://ieeexplore.ieee.org/abstract/document/8614745
Alwan, Z. S., & Younis, M. F. (2017). Detection and prevention of sql injection attack: A survey. Risk assessment case studyInternational Journal of Computer Science and Mobile Computing, 6(8), 5- 17. https://www.researchgate.net/profile/Zainab_Alwan2/publication/320108029_Detecti on_and_Prevention_of_SQL_Injection_Attack_A_Survey/links/59ce63840f7e9b4fd7 e1b495/Detection-and-Prevention-of-SQL-Injection-Attack-A-Survey.pdf
Chung, H. (2017). Work autonomy, flexibility and work-life balance final report. https://kar.kent.ac.uk/65922/1/Flexible%20working%20report.pdf
Dominitz, E. J. (2016). To Err Is Human; to Insure, Divine: Shouldn't Cyber Insurance Cover Data Breach Losses Arising (in Whole or in Part) from Negligence. Brief, 46, 32. https://heinonline.org/HOL/LandingPage?handle=hein.journals/tbrief46&div=57&id= &page=
Jardine, E. (2020). The Case against Commercial Antivirus Software: Risk Homeostasis and Information Problems in Cybersecurity. Risk Analysis. https://onlinelibrary.wiley.com/doi/abs/10.1111/risa.13534
Kaikkonen, T. (2019). SaaS Application Integration Challenges. https://www.theseus.fi/handle/10024/160365
Mehmood, A., Natgunanathan, I., Xiang, Y., Hua, G., & Guo, S. (2016). Protection of big data privacy. IEEE access, 4, 1821-1834. https://ieeexplore.ieee.org/abstract/document/7460114
Patel, K., &Alabisi, A. (2019). Cloud Computing Security Risks: Identification and Assessment. The Journal of New Business Ideas & Trends, 17(2), 11-19. http://jnbit.org/upload/JNBIT_2_Patel_Alabisi_17(2)_2019.pdf
Paul, P., &Aithal, P. S. (2019, October). Network security: threat & management.Risk assessment case study In Proceedings of International Conference on Emerging Trends in Management, IT and Education (Vol. 1, No. 1, pp. 85-98). https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3484110 Poder, D., & Eckel, R. A. (2019). U.S. Patent No. 10,282,802. Washington, DC: U.S. Patent and Trademark Office. https://patents.google.com/patent/US10282802B2/en
Primiero, G., Solheim, F. J., & Spring, J. M. (2019). On malfunction, mechanisms and malware classification. Philosophy & Technology, 32(2), 339-362. https://link.springer.com/article/10.1007/s13347-018-0334-2
Sharif, S., Watson, P., Taheri, J., Nepal, S., &Zomaya, A. Y. (2016). Privacy-aware scheduling SaaS in high performance computing environments. IEEE Transactions on Parallel and Distributed Systems, 28(4), 1176-1188. https://ieeexplore.ieee.org/abstract/document/7552583
Shastri, A., & Sharma, P. (2016, March). Data vault: A security model for preventing data theft in corporate. In Proceedings of the Second International Conference on Information and Communication Technology for Competitive Strategies (pp. 1-5) https://dl.acm.org/doi/abs/10.1145/2905055.2905358
The 5 Biggest Challenges in Global Data Privacy and Protection - Cipher. (2020). Retrieved 22 August 2020, from https://cipher.com/blog/the-5-biggest-challenges-in-global- data-privacy-and-protection/
Yuen, W. P., &Chuah, K. B. (2017, December). Data visibility and trust enhancement of enterprise customers in cloud computing services.Risk assessment case studyIn 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST) (pp. 417- 422). IEEE. https://ieeexplore.ieee.org/abstract/document/8356435












