Risk Management Essay: Impact on Strategic Objectives of Abacus Property Group
Question
Task
Write a 2000 word risk management essay describing two strategic objectives in your own words. Then, describe two cyber risks that are known to have taken place since January 2018. There two cyber risks must be related to the two strategic objective- illustrate how the strategic objective and the cyber risks are likely to impact each other.
Answer
Introduction
Over the years, rapid technological advancements have paved the way for various forms of innovations through which many organizations and even the general population have enhanced their activities carried out in their day to day lives (Hadlington, 2017). The drastic implementation of technological aspects within the working community has its pros as well as cons. While technology can help organizations and individuals of the general population to foster their needs effectively and convert the world into a global village; technology can also pave the way for certain enthusiasts to harm others and such enthusiasts are known as cybercriminals (Kaplan et al., 2015). Hence, many organizations within the information technology sector have developed various tactics and software through which they can counteract such cybercrimes and set up an encryption that helps to protect the users of technology. This essay reflects upon an ASX (Australian Securities Exchange) company known as Abacus Property Group which operates in the real estate sector and two strategic objectives have been outlines that coincide with two key risks that the company has faced since January 2018. This essay also reflects upon the key future cyber risks based on an external as well as an internal environment of the organization and an analysis has been drawn upon the impact of such future risks towards the strategic objectives of the company.
Two strategic objectives (Criterion 1)
One of the strategic objectives catered by the Abacus Property Group is to engage in investment opportunities and diversifying the real estate sector in Australia as well as New Zealand (Abacus Sustainability Reports, 2018). Such investments are made in forms of fund transfer or money wiring from the various stakeholders of the business organizations associated with the Abacus Property Group. The Abacus Property Group engages in activities that facilitate the growth of commercial and residential housing projects through which the company aims to grow its chain of business and attract tenants across the nations.
Another strategic objective of the Abacus Property Group is to promote marketing and sales to further enhance their brand image as well and market share. Abacus Property Group is one of the largest companies in terms of Australia’s market capital through which over the years, the company has significantly grown due to the services and the marketing activities that the company carries out within the communities of the country (Zerlang, 2017). Abacus Property Group aims to cater to the process of market segmentations through which they can target potential tenants and customers of the real estate sector and create a diversified business that caters to the needs of various investors within the real estate sector and facilitate the security holders and the investment community (Yang, 2017).
Two key risks since 2018 (Criterion 2)
BEC (business email compromise)
One of the most prevalent cybersecurity threats that organizations with huge investors within the real estate business is the threat of BEC (business email compromise). This cybersecurity attack is also commonly referred to as whaling, spear-phishing, or CEO fraud (Sun et al., 2018). BEC is carried out by cyber-attacks based on social engineering where an individual within an organization can impersonate fraudulent financial activities on a senior figure where the individuals are tricked to urgently transfer funds in various forms of transactions that occur routinely (Tisdale, 2015). For example, the routine payment such as paying suppliers is wired to an account that appears to be transferred to the supplier but the individual without even knowing transfers the funds to someone completely different, and the money trail is pretty hard to follow. The businesses can be the victims as well where the funds are lost while paying their suppliers and the attackers may divert the funds towards themselves or redirect it to an unknown source by bouncing various IP addresses (Onwubiko, 2015). In this form of cyber-attack, often the leaders and superiors of an organization such as the CEO are implicated as a fraud where they try to steal funds from the business linking to offshore accounts (Paulsen, 2016).
MITM (Man-in-the-middle)
This particular cyber attack is a process where the cyber attacker secretly portrays themselves as a part of an organization and caters to the authentic digital signatures of the organization to relay different forms of communications among the parties that are related during a particular event (Puthal et al., 2018). For example, the attacker impersonates as someone from an authentic organization on digital platforms and changes the communication contexts between the two parties where the victims believe that they are directly communicating with each other even when they are not. Such misinterpretation of information can lead to devastating results where the business may face incremental losses (Bada, 2019). For example, a contractor representing Abacus Property Group on digital platforms can act as an imposter where the customers within the real estate sector find it extremely difficult to identify whether they are authentic or not as the imposters portray digital signatures of the business organization and misinterpret actual information which is contradictory to the chosen regulatory aspects (Low, 2017).
The linkage between the objectives and the risks (Criterion 3)
The BECs are a form of malicious activity where the attackers essentially hack into a corporate account of an individual of an organization and impersonate the real owner to defraud the organization as the account which they hack in; comprises of the digital signature of the victims (Le Compte, 2015). The attackers or the hackers trick various internal and external stakeholders such as customers, partners, or even employees of the organization to pay huge funds or sensitive/ confidential data to the attacker's account (Paulsen, 2016). This is a serious form of threat towards the Abacus Property Group as they deal with huge funds involving various investors across the globe. Since the Abacus Property Group has the highest amount of market capital in the ASX (ASX200, 2020), the business organization must engage in various forms of cybersecurity measures to protect the funds of the investors as well as the stakeholders. Attackers can hack into the corporate accounts of the stakeholders within the business's database and trick their investors to transfer funds to various offshore accounts that implicate the fraud that has been committed by the account from which the attackers hack (Rothrock, 2018). The digital signatures pave the way for the identification of the source of defrauding even when the victims had no part to play whatsoever. The attackers pose as the CEO or any other kind of influential executive of the organization and send various emails to their employees in the finance department where requests are made to transfer funds to the account that they essentially control (Oltramari, 2015). Hence, the Abacus Property Group needs to protect its digital accounts set up an effective firewall through which such instances of BEC can be avoided and the huge funds of the organization can be protected and accounted for.
Abacus Property Group also aims to engage in various forms of marketing and sales promotions through which they can facilitate their high revenues that the organization has earned over the years (Abacus Sustainability Reports, 2018). Abacus Property Group hires various sales executives’ staffs that implement the marketing policies implemented by the organization and the MITM attack can hamper the effective process of marketing by misinterpreting essential information towards their existing and potential customers within the real estate sector. Since the MITM attack is a form of eavesdropping process where the attacker acts as a proxy to the actual executive and can aim to steal sensitive information that involves the marketing and sales strategies (Björck, 2015) of Abacus Property Group. The attacker can exploit the communications systems of the company and also hamper the real-time processing of transactions/ conversations which leaves the Abacus Property Group to various forms of exposure and possible future litigations. The marketing strategies are stored in the company database where the attackers can simply listen to any conversation between an executive and a customer and interpret such flow of data from a device’s browser and applications to transfer such sensitive information to third parties (Carr, 2016). The attackers can either sell the information which they have gathered or act as an executive of the organization and change the integral aspects in the company contracts and bylaws through which both the customer as well as the organization suffers a huge loss (Adams, 2015). Therefore the information technology department of Abacus Property Group has to make sure to confirm all forms of contextual information that are shared with the customers and establish a sense of authenticity through which any form of malicious activity is triggered fast and acted upon as soon as possible (Kostopoulos, 2017).
Future cyber risks (Criterion 4)
The two possible cyber risks that Abacus Property Group may encounter in the future are the risks of MITM and BECs.
Abacus Property Group is one of the largest ASX200 companies and caters to a huge amount of market capital; therefore it can be easily understood that the company deals with huge funds that are scattered in various departmental heads of the organization. The company drives in huge amounts of internal and external investments that need to be accounted for by the organization in their annual fiscal reports and if instances of BECs occur; the finance department of Abacus Property Group is compromised. The attackers can pose themselves as an influential executive or a CEO where they trick the finance department by sending emails to transfer funds to various accounts and often such accounts are bounced of various IP addresses that make it difficult to identify the real imposter and as a result, the not guilty parties are found guilty as their digital signatures are used in the process (Sabillon, 2017). The company can be charged with various class action lawsuits of embezzlement and litigations that may pave the way for the business to be bankrupt/ loss of customers/ hurting the brand recognition/ fall of stock prices in the Australian market (Ashenden, 2016).
If the Abacus Property Group faces a MITM attack then their sensitive data involving marketing policies and strategies are compromised. The attackers can alter and view the contextual communications on digital platforms of the company's database and use their digital signatures to transfer sensitive data to third parties or theft of intellectual property which can affect the profitability of the business (Leuprecht, 2016). This would essentially mean that the customers are engaging in different forms of communications with imposters who can steal the customer’s personal data while engaging in marketing activities such as surveys (Talesh, 2018). The customers are posed with offers that the management of Abacus Property Group does not adhere to and this generates instances of conflict of interest as well as litigations where the customers feel defrauded through the marketing activities (Boyes, 2015). An analysis of the aforementioned future risks is demonstrated by the attack tree scenario below in Figure 1.
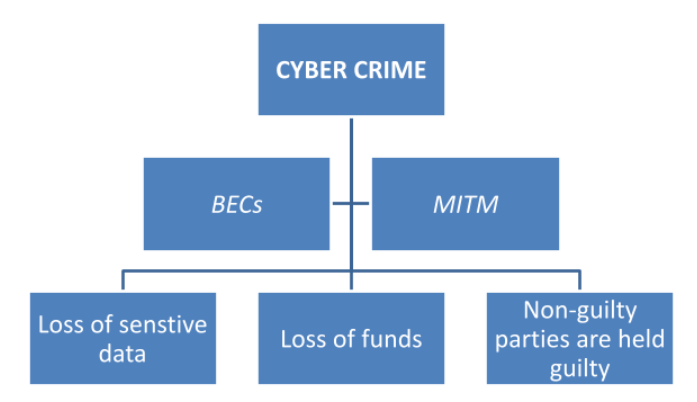
Figure 1: Attack Tree Scenario
Source: Created by the learner
Internal element (Criterion 5 + Criterion 7 included)
The major internal elements of the Abacus Property Group are the stakeholders of the business who are the various forms of investors. BECs essentially aim to defraud the members of the board by transferring funds to various unethical accounts and drain the resources of the company. The strategic objectives which are set by the management of Abacus Property Group can be adversely affected through the aforementioned attacks as funds can be transferred to offshore accounts using the digital signatures of the CEO or any other executive for which the finance department must implement measures that counteract such aspects of authenticity (Teoh, 2017). The emails which are not meant to be sent must be scrutinized by the finance department and establish a form of authenticity through which the funds as well as the members of the board are protected concerning the financial aspects of the business (Wang, 2015).
External element (Criterion 6 + Criterion 7 included)
The major external elements of the Abacus Property Group are the technological aspects through which the business organization faces an exposure or any form of future litigation in the future. The MITM attacks act as a proxy for the business through which the sensitive data of the customers can be stolen or even the attackers can pose themselves as executives of the organization and alter the contextual contracts and bylaws that have been established (Craig, 2015). The customers can essentially feel neglected and cheated where their personal data is hacked and sold to third parties for instances of corporate espionage (Hubbard, 2016). Hence, the technological advancements and lack of loyalty among the common mindset of the individuals of the organization can affect the effective decision-making skills of the organization (Kosseff, 2017). The external environment of technology must be used by the Abacus Property Group in such a manner that helps them to grow and protect themselves against any form of malicious activity.
The implications of the two aforementioned risks towards the future of the Abacus Property Group are analyzed through the attack tree scenario in Figure 2.
Figure 2: Internal and external implications of the cybercrimes Source: Created by the learner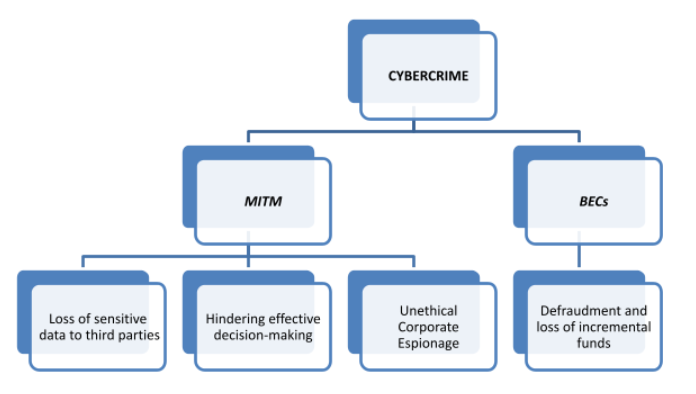
Figure 2: Internal and external implications of the cybercrimes
Source: Created by the learner
Reasons why the objectives may be impacted (Criterion 8)
The following table demonstrates the major reasons why the strategic objectives may be impacted when the cyber risks actually occur and the possible outcomes of such risks. Ratings of the risk levels have also been provided for the same.
|
Cyber risk |
Implications (consequence) |
Probability of risk (Scale of 1 to 5) |
The negative impact of the risk (Scale of 1 to 5) |
Impact on the objectives |
|
MITM |
|
3 |
4 |
Marketing policies and strategies are hindered as imposters aim to steal sensitive data from the customers as well as the business. |
|
BECs |
|
2 |
4.5 |
The funds of the business are lost where the influential executives of the business organization are held accountable and result in instances of litigation and class action lawsuits. |
Conclusion
This essay has identified the possible cyber risk factors for an ASX200 company known as Abacus Property Group where instances of the risks have been described along with the possible implications of the risks towards the strategic objectives as well as the internal and external elements of the business. The essay demonstrates how cyber risks can affect the proper functionality of the business in the real estate sector and why the organization must ensure proper cybersecurity measures to avoid the risks in the foreseeable future.
References
Abacusproperty.com.au. Abacus Property Group Sustainability Report 2018 [online]. Retrieved from www.abacusproperty.com.au [accessed October 5, 2020]
Adams, M., & Makramalla, M. (2015). Cybersecurity skills training: an attacker-centric gamified approach. Technology Innovation Management Review, 5(1).
Ashenden, D., & Lawrence, D. (2016). Security dialogues: Building better relationships between security and business. IEEE Security & Privacy, 14(3), 82-87.
Asx200list.com. ASX 200 List of Companies – Directory [online]. Retrieved from
Bada, M., Sasse, A. M., & Nurse, J. R. (2019). Cyber security awareness campaigns: Why do they fail to change behaviour?. arXiv preprint arXiv:1901.02672.
Björck, F., Henkel, M., Stirna, J., & Zdravkovic, J. (2015). Cyber resilience–fundamentals for a definition. In New contributions in information systems and technologies (pp. 311-316). Springer, Cham.
Boyes, H., 2015. Cybersecurity and cyber-resilient supply chains. Technology Innovation Management Review, 5(4), p.28.
Carr, M. (2016). Public–private partnerships in national cyber-security strategies. International Affairs, 92(1), 43-62.
Craig, A. N., Shackelford, S. J., & Hiller, J. S. (2015). Proactive cybersecurity: A comparative industry and regulatory analysis. American Business Law Journal, 52(4), 721-787.
Hadlington, L. (2017). Human factors in cybersecurity; examining the link between Internet addiction, impulsivity, attitudes towards cybersecurity, and risky cybersecurity behaviours. Heliyon, 3(7), e00346.
Hubbard, D. W., & Seiersen, R. (2016). How to measure anything in cybersecurity risk. Hoboken: Wiley.
Kaplan, J. M., Bailey, T., O'Halloran, D., Marcus, A., & Rezek, C. (2015). Beyond cybersecurity: protecting your digital business. John Wiley & Sons.
Kosseff, J. (2017). Defining cybersecurity law. Iowa L. Rev., 103, 985.
Kostopoulos, G. (2017). Cyberspace and cybersecurity. CRC Press.
Le Compte, A., Elizondo, D., & Watson, T. (2015, May). A renewed approach to serious games for cyber security. In 2015 7th International Conference on Cyber Conflict: Architectures in Cyberspace (pp. 203-216). IEEE.
Leuprecht, C., Skillicorn, D. B., & Tait, V. E. (2016). Beyond the Castle Model of cyber-risk and cyber-security. Government Information Quarterly, 33(2), 250-257.
Low, P. (2017). Insuring against cyber-attacks. Computer Fraud & Security, 2017(4), 18-20.
Oltramari, A., Henshel, D. S., Cains, M., & Hoffman, B. (2015, November). Towards a Human Factors Ontology for Cyber Security. In Stids (pp. 26-33).
Onwubiko, C. (2015, June). Cyber security operations centre: Security monitoring for protecting business and supporting cyber defense strategy. In 2015 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA) (pp. 1-10). IEEE.
Paulsen, C. (2016). Cybersecuring small businesses. Computer, 49(8), 92-97.
Paulsen, C., & Toth, P. (2016). Small business information security: The fundamentals (No. NIST Internal or Interagency Report (NISTIR) 7621 Rev. 1). National Institute of Standards and Technology.
Puthal, D., Malik, N., Mohanty, S. P., Kougianos, E., & Yang, C. (2018). The blockchain as a decentralized security framework [future directions]. IEEE Consumer Electronics Magazine, 7(2), 18-21.
Rothrock, R. A., Kaplan, J., & Van Der Oord, F. (2018). The board's role in managing cybersecurity risks. MIT Sloan Management Review, 59(2), 12-15.
Sabillon, R., Serra-Ruiz, J., Cavaller, V., & Cano, J. (2017, November). A comprehensive cybersecurity audit model to improve cybersecurity assurance: The cybersecurity audit model (CSAM). In 2017 International Conference on Information Systems and Computer Science (INCISCOS) (pp. 253-259). IEEE.
Sun, N., Zhang, J., Rimba, P., Gao, S., Zhang, L. Y., & Xiang, Y. (2018). Data-driven cybersecurity incident prediction: A survey. IEEE Communications Surveys & Tutorials, 21(2), 1744-1772.
Talesh, S. A. (2018). Data breach, privacy, and cyber insurance: How insurance companies act as “compliance managers” for businesses. Law & Social Inquiry, 43(2), 417-440.
Teoh, C. S., & Mahmood, A. K. (2017, July). National cyber security strategies for digital economy. In 2017 International Conference on Research and Innovation in Information Systems (ICRIIS) (pp. 1-6). IEEE.
Tisdale, S. M. (2015). Cybersecurity: Challenges from a Systems, Complexity, Knowledge Management and Business Intelligence Perspective. Issues in Information Systems, 16(3).
Wang, P., Ali, A., & Kelly, W. (2015, August). Data security and threat modeling for smart city infrastructure. In 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC) (pp. 1-6). IEEE.
Yang, S. C., & Wen, B. (2017). Toward a cybersecurity curriculum model for undergraduate business schools: A survey of AACSB-accredited institutions in the United States. Journal of Education for Business, 92(1), 1-8.
Zerlang, J. (2017). GDPR: a milestone in convergence for cyber-security and compliance. Network Security, 2017(6), 8-11.












